Alleged North Korean Threat Actor Targets Select Victims with another Critical Zero-Day Vulnerability Attack

Attributing cyberattacks and advanced malware to a particular country or entity is usually troublesome. Forensic artefacts can sometimes be planted or forged to point to a specific country or cybercriminal group.
However, analyzing the current geopolitical context and matching it against victims and available forensic evidence can sometimes make attribution more plausible. This holds true with a recently discovered advanced threat that leveraged a critical Adobe Flash zero-day vulnerability (CVE-2018-4878).
Primarily targeting the public and private sectors of South Korea, as well as Japan, the Middle East and other parts of Asia, security researchers believe the likely culprit to be a North Korean threat actor known as APT37, Group123 or Reaper.
Threat actors rely on zero-day vulnerabilities and exploits because of the unique ability to allow automatic and non-interactive entrance to a system, enabling malware to be executed. The problem with zero-day vulnerabilities is that traditional security solutions cannot protect against them.
Exploiting the vulnerability
The alleged North Korean threat actor that leveraged the zero-day vulnerability targeted victims using spearphishing emails containing tainted attachments and promising time-sensitive information.
This recent campaign used a document that contained a Flash object to be opened within a browser as soon as the victim executed the attachment. Once opened, the Flash object exploited a vulnerability within the Adobe Flash application and downloaded an additional payload from a command and control (C&C) server.
This second-stage payload was to be loaded and executed within memory to unpack a surveillance tool or piece of malware on the targeted system. Interestingly, the malware allocates and executes in the context of the browser it runs in.
While multi-stage attacks are commonly used to prevent security solutions from tagging the final payload, attackers have increasingly been abusing in-memory loaded shellcode.
These memory manipulation techniques help threat actors dodge traditional file-scanning security solutions, especially since so called next-gen security solutions rely only on machine learning techniques. The issue is that machine learning only applies to files, clustering them based on features. So machine learning is ineffective against memory-based attacks, because they leave no on-disk footprint.
Real-time hypervisor-level introspection detects zero-day exploits, prevents breaches
Technologies such as memory-based introspection that run completely outside the operating system are specifically designed to identify memory manipulation techniques associated with advanced threats. Since business and organizations regularly use virtual workloads – such as VDIs – to boost productivity, augmenting in-guest security solutions with hypervisor-enforced security is far more effective in protecting against sophisticated attacks.
The demo video below illustrates an attack against an unprotected VDI - as virtual servers don’t run Adobe Flash – using the CVE-2018-4878 Adobe Flash vulnerability that’s triggered when users open the tainted attachment from the spearphishing email.
Commonly deployed within organizations, VDIs often bring greater flexibility and ease of management using limited resources. Attack scenarios in which VDIs are compromised are both plausible and very effective in breaching an organization’s infrastructure.
The first part of the demo involves running the exploit on a virtual workload not protected by hypervisor introspection, revealing how easily it can be compromised without a security solution that can detect the CVE-2018-4878 exploit.
The second part of the video show how, by detecting zero-day exploits in real-time, Bitdefender Hypervisor Introspection prevents the attack from unfolding and dropping a payload on its target. The provided incident report offers unique insights into the attack for forensic investigations, helping organizations better secure their virtual environments.
Game changer in breaking the attack-chain
Hypervisor introspection technology (HVI) was designed to counter advanced threats. It’s completely compatible with any in-guest security solution and completely outside the operating system, and its performance impact on the virtual workload is minimal. Consequently, regardless of the security solution victims would have been using within their virtual machine (VM), hypervisor introspection would have detected it.
The hypervisor introspection technology can also immediately inject a remediation tool within the memory of the affected virtual workload, for remediation. This remediation tool does not conflict with any other in-guest security agents and it’s completely offloaded once it addresses the security issue.
Check out a simple diagram below, detailing where during the attack chain HVI would have prevented the Adobe Flash zero day vulnerability (CVE-2018-4878) from being exploited.
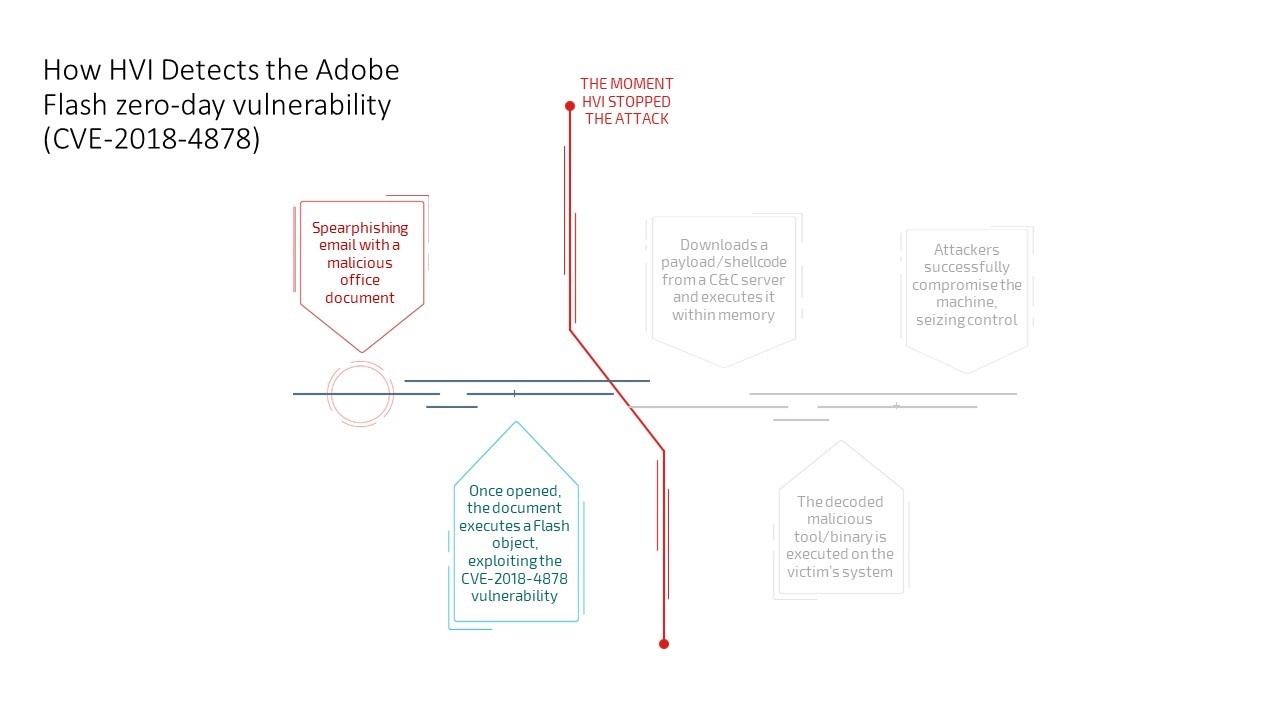 Fig. 1
Fig. 1
This means that, even if the spearphishing email had reached a client’s inbox, the moment the tainted document oped opened our HVI technology would have successfully blocked the unknown critical zero-day Flash vulnerability from being leveraged by threat actors to compromise the victim.
Bitdefender Hypervisor Introspection, launched in May 2017 in collaboration with Citrix, is the only solution able to provide raw memory introspection on virtual infrastructures. The solution was awarded ‘Best New Technology’ and ‘Industry Innovator’ and IDC called it ‘a qualitative improvement in the security of virtual environments’.
For more information about business security solutions or the Bitdefender Hypervisor Introspection technology, check out https://www.bitdefender.com/hvi or https://www.bitdefender.com/business/.
tags
Author
Liviu Arsene is a Global Cybersecurity Researcher for Bitdefender, with a strong background in security and technology. Researching global trends and developments in cybersecurity, he focuses on advanced persistent threats and security incidents while assessing their impact in critical public and private business infrastructures. His passions revolve around innovative technologies and gadgets, focusing on their security applications and long-term strategic impact.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











