Business Payroll Compromise – a New Way for Criminals to Steal from Your Company

Firms are being warned about a threat which evolves traditional business email compromise scams into a whole new way of extracting money from unwary companies.
Most of us are familiar with business email compromise (BEC) also sometimes known as “CEO Fraud” or “whaling”.
A typical attack sees a criminal either pose as your boss, sending emails that ask you – a lowly employee – to transfer business funds into a bank account under their control, or forward sensitive information.
And if you work in an environment where you feel uncomfortable saying “no” to the CEO, there’s a good chance that you’ll do what they request.
More sophisticated attacks take things one stage further. Having broken into company email accounts, criminals spy upon communications, and learn about their victims’ suppliers and contractors. With that information they then create fake invoices for genuine projects being undertaken, and try to fool finance departments into paying large amounts of money into bank accounts under fraudsters’ control.
Last year, the FBI calculated that globally over $12 billion worth of losses had been exposed by business email compromise scams between October 2013 and May 2018.
That’s obviously a huge amount of money, and if you thought it would be hard for things to get much worse think again.
A report from Agari describes a new trend in Business Email Compromise which sees criminals attempting to get themselves literally on the payroll of targeted companies.
As the researchers describe, an attack can begin in the tradition fashion with an employee’s email account being compromised (perhaps because they were phished, reused a password, or had fallen victim to password-stealing malware).
With the email account hijacked, a fraudster then emails the human resources or finance department requesting that their salary be paid into a new bank account.
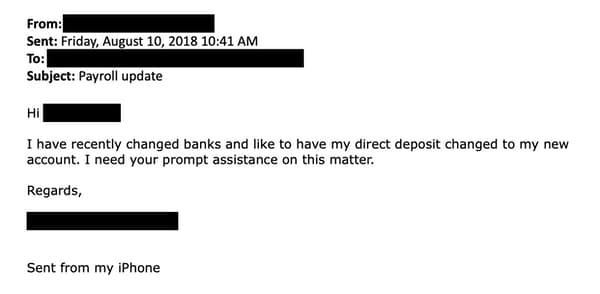
In some cases, an HR department may ask that the request be accompanied by documentation confirming the new bank account details, perhaps printed on the bank’s letterhead.

At this point the scammer has a choice, they can either forge a letter on the bank’s letterhead (which is not difficult to do, especially if the HR department is happy to receive it in the form of a digital scan) or use social engineering techniques to trick the administrator into making the change.
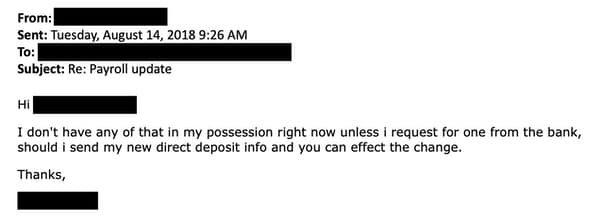
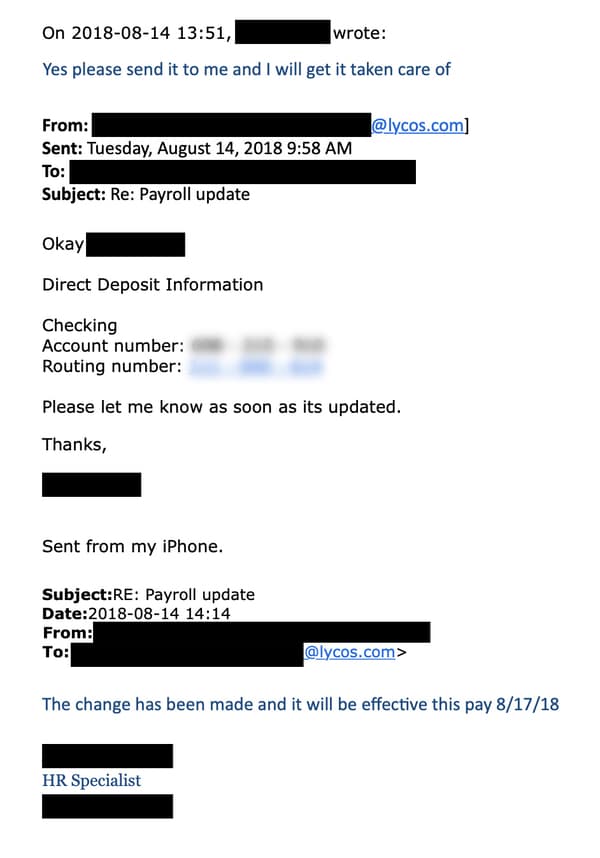
Things would be even easier, of course, insider corporations which allow staff to update their own payroll details – without having to request an HR or finance department to assist them – by accessing a self-service system.
Depending on how often the genuine employee checks their bank balance, it may take weeks or months before they notice that they have not received their salary as expected.
Agari’s advice for organisations is simple – take a look at your current process for updating payroll systems, and evaluate if you are doing enough to prevent fraudulent requests.
Two-factor authentication can definitely play a part, but if that is not available ensure that an additional “element of human contact is established before completion of the request” in addition to check that email address is from a legitimate source.
So, where next could attacks evolve? One possibility that remains, although it may be tricky to pull off, would be to find a way to fool a business into not just changing the payment details of an employee but into actually adding an actual fake employee to their payroll.
I wonder whether a large disorganised company could actually be duped via emails from compromised management accounts into adding a fraudster as a new employee, and how many months it would take until the firm realised that they had been paying a criminal a monthly wage.
tags
Author

Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s, having been employed by companies such as Sophos, McAfee and Dr Solomon's. He has given talks about computer security for some of the world's largest companies, worked with law enforcement agencies on investigations into hacking groups, and regularly appears on TV and radio explaining computer security threats. Graham Cluley was inducted into the InfoSecurity Europe Hall of Fame in 2011, and was given an honorary mention in the "10 Greatest Britons in IT History" for his contribution as a leading authority in internet security.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










