Defend Your Organization from Browser-based Attacks with Bitdefender Browser Isolation

- The web is a dangerous place, but denying end-users access isn’t realistic
- Isolate browsers from end-user systems via application virtualization
- Secure virtualized browsers to protect against attacks in high-risk scenarios
The Web is a Dangerous Place Which Users Need
There are few administrators who would express confidence in the security posture of web browsers and their associated plug-ins. Whether it is highly sensitive users (CxO’s, human resources, etc.) or when publishing old, unpatchable browsers to support legacy applications. At the same time, end-users demand access to a wide variety of internal and external web resources. Part of the problem is that web browsers are designed to download a wide variety of rich content, executing some of it locally to render pages. That execution of content puts organizations at risk as attackers continue to exploit vulnerabilities in browsers and the extremely wide variety of plug-ins they run. In the worst cases, this can lead to complete compromise of the end-user system, which may result in ransomware or other malware being installed, or attacks on adjacent infrastructure on your network.
The Problems with Known-bad and Known-good
There are a variety of solutions such as endpoint antimalware and Secure Web Gateways (SWG) which are a necessary part of the security fabric, but have not led to end-users being able to securely browse with confidence. Robust antimalware looks for known malware and monitors processes for unusual behavior, but even the best solutions will sometimes let things slip through the cracks. The primary problem with hunting for known-bad is that new malware and novel attacks are created at a blistering rate.
Likewise, using something like an SWG to limit browsing to only known-good web resources is not a complete solution. Managing known-good is onerous, even at modestly-sized organizations, as the list of resources which end-users require tends to be long and dynamic. Adding to this, even trusted web sites can be compromised in a variety of ways, instantly making a known-good resource malicious. Even using a hybrid approach such as URL reputation is, by definition, reactive.
Isolating Browsers Is a Great First Step
Administrators have long designed datacenters to isolate web-facing resources, such as web servers, in Demilitarized Zone (DMZ). More sensitive resources, such as application and database servers, are hosted on parts of the network which are not directly accessible from the outside. The same concept applies to web browsers.
Since web browsers are external-facing resources, they should be isolated from end-user systems. Virtualizing web browsers using solutions like Citrix Virtual Apps is a great way to move the epicenter of browsing activity from end-user systems to virtualized servers. Citrix is a long-time leader in providing excellent end-user experience in this area.
However, just as administrators don’t leave systems in the DMZ unprotected, the systems where virtualized browsers run, and the browsers themselves, must be protected.
Combining Unique Bitdefender Security and Virtualized Browsers
Citrix Virtual Apps includes an entitlement to Citrix Hypervisor, which has unique security capabilities which Bitdefender takes advantage of. Bitdefender Browser Isolation applies its patented security technology, known as Hypervisor Introspection, to monitor the raw memory of running Virtual Apps servers, and the browsers which they host. Rather than looking for known-good or known-bad, the solution proactively detects and blocks sophisticated attack techniques which are used over and over to compromise browsers.
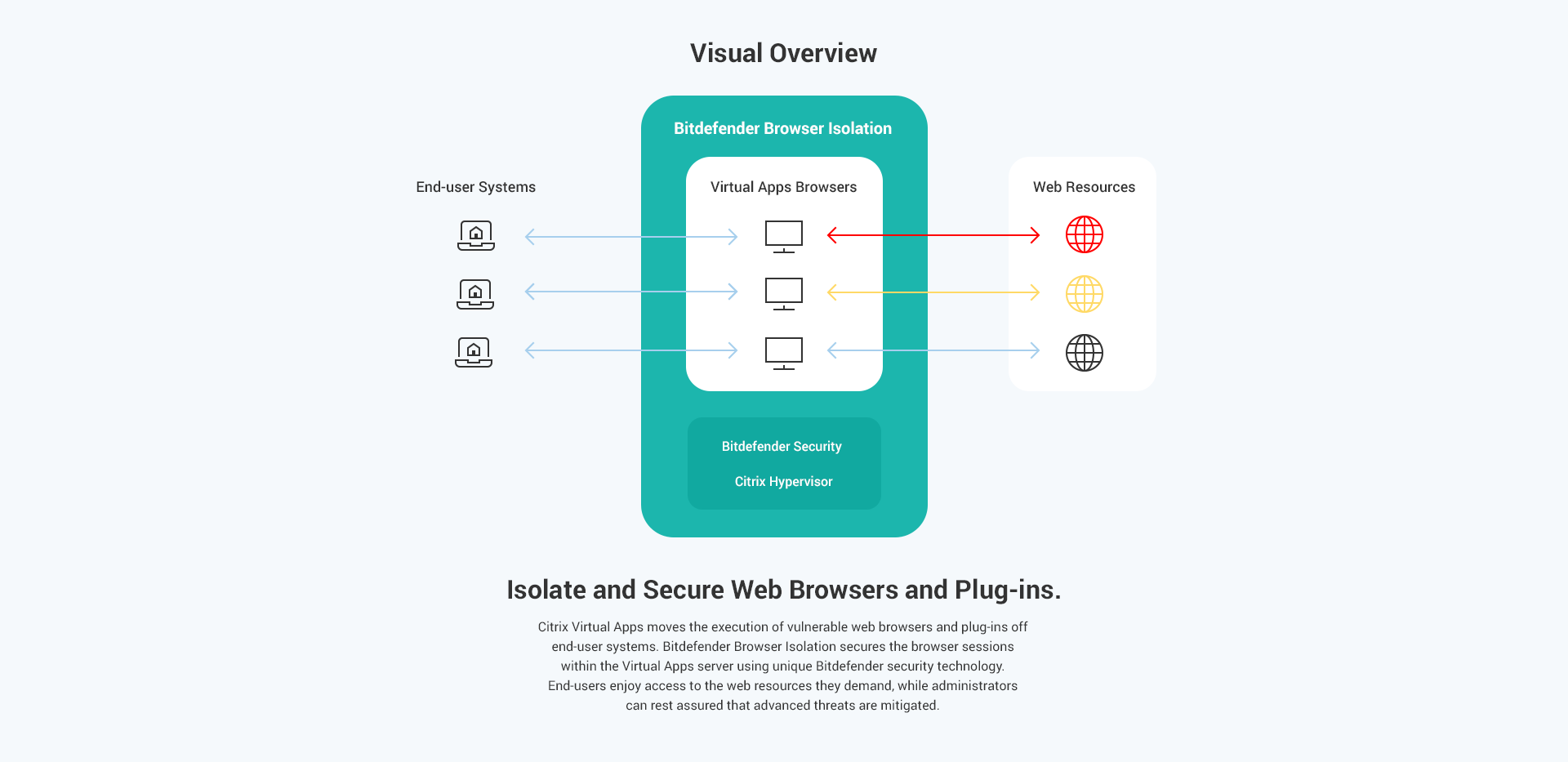
These are techniques which we often hear about when new vulnerabilities are exploited. They include buffer overflows, heap spray, and code injection. In other words, if an attacker tries to exploit a vulnerability, known or unknown, Bitdefender Browser Isolation detects and blocks the attack so malicious actors cannot get an initial foothold in your environment through the browser.
How You Get Started
If you are already virtualizing browsers with Citrix Virtual Apps and using Citrix Hypervisor, you are already on the path to isolating browsers. The next step is to identify critical use-cases, such as specific end-users (CxO, finance, human resources), high-risk resources (untrusted external URLs), and/or high-risk browsers (old versions published to support legacy applications). These are scenarios for which you may already be providing virtualized browsers. The next step is to employ Bitdefender Browser Isolation to protect those virtualized browsers.
If you are not running Virtual Apps on Citrix Hypervisor, Bitdefender will help you protect just these critical use-cases or all browsing activity in your enterprise by moving their execution to Virtual Apps servers on Citrix Hypervisor, and applying Bitdefender Browser Isolation. This will result in a greatly increased security posture of browsers, without changing the end-user experience.
For more information about Bitdefender Browser Isolation, visit https://www.bitdefender.com/business/enterprise-products/browser-isolation.html
tags
Author
.jpg)
Shaun Donaldson is Editor-at-large at Bitdefender Enterprise. Shaun is also responsible for supporting relationships with strategic alliance partners and large enterprise customers, and analyst relations. Before joining Bitdefender, Mr. Donaldson was involved in various technology alliances, enterprise sales and marketing positions within the IT security industry, including Trend Micro, Entrust, Bell Security Solutions and Third Brigade.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks









