4 min read
Gartner on Security: You WILL Be Breached. So Make Sure Attackers Linger No Longer
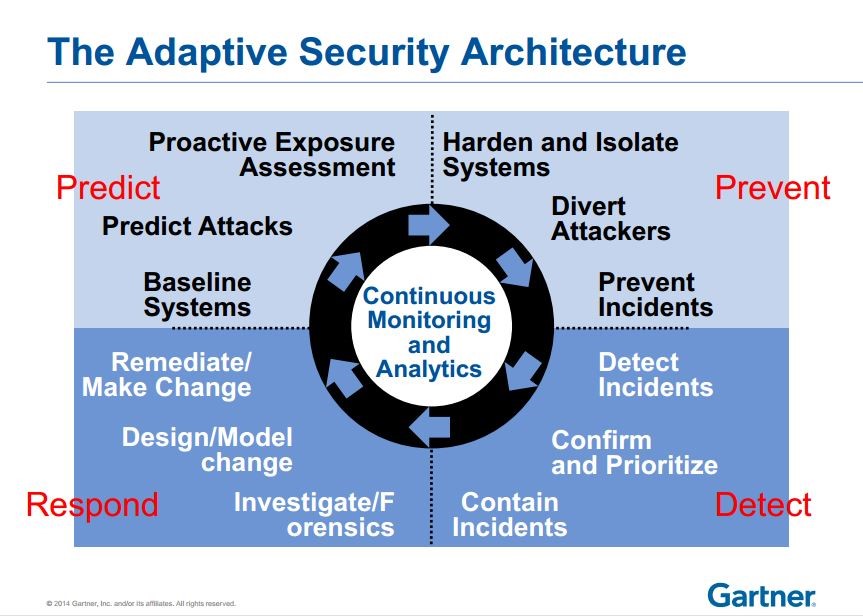
At the Gartner Security and Risk Management Summit in London last week, Gartner’s Neil McDonald shared a novel approach to security with a packed room of CSOs and IT professionals.
No matter what security measures your organization takes, it WILL be attacked and/or breached, he said during a discussion of Gartner’s Adaptive Security Architecture.
So, beyond preventing attacks, CSOs face the challenge of making sure intruders don’t linger undetected in their networks.
The novelty lies in the attention to detecting incidents already underway, and being able to respond and remediate them quickly to limit the damage.
Of course you still need to predict trends and prevent attacks, just as you have always done with your Endpoint protection software and the relationship you build with your AV vendor. As Gartner’s Peter Firstbrook said,” the notion that signatures are dead is a misguided hyperbole”, so your AV still has a bright future. And, by the way, most leading AV vendors include other components from the “prevent” quadrant in their products. Bitdefender is one of those vendors to include white listing, machine learning and behavior monitoring technologies for example.
The Adaptive Security Architecture model is smart, and nicely future-proof (it still is today, more than a year after Gartner started presenting it). Many up and coming vendors cover each niche within the model. But for now the model is a challenge to implement; CSOs have to make a lot of choices. What segments to cover from the model? Which type of attacks are a priority in terms of detection?

Photo Caption : Gartner’s Adaptive Security Architecture
As Gartner’s Mario de Boer explained, different types of attacks require different solutions. In the end, a large enterprise would probably have to work with multiple small vendors to achieve adequate coverage. This implies researching the smaller vendor extensively to make sure they are sound in terms of human resources and finances, and that they will still be around in a few years. (Thankfully, Gartner analysts do a good job guiding enterprises in making those choices).
The model looks solid and, as the larger players integrate additional features into their solutions (by acquiring technologies or in-house development), it will become increasingly relevant. We have already written about the chaos of choosing multiple endpoint protection solutions on purpose. So, how does adding multiple Endpoint Detection and Response solutions on top of that work for your organization?
{{cta('92c8aec5-8145-462b-967a-598913501326','justifycenter')}}
tags
Author

Damase TRICART is Global Communications Director for Bitdefender. His 20 years of experience with some of the security industry’s leading vendors taught him that the human is the weak link in the security chain. A strong advocate for security awareness and education for home users and enterprise employees, he leads a team dedicated to taking complex security issues, explaining them simply and placing them back into the business context. When he is not thinking security, he is playing around with the latest connected tech gadget or listening to rock music.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










