How should businesses respond to the TechCrunch hack?
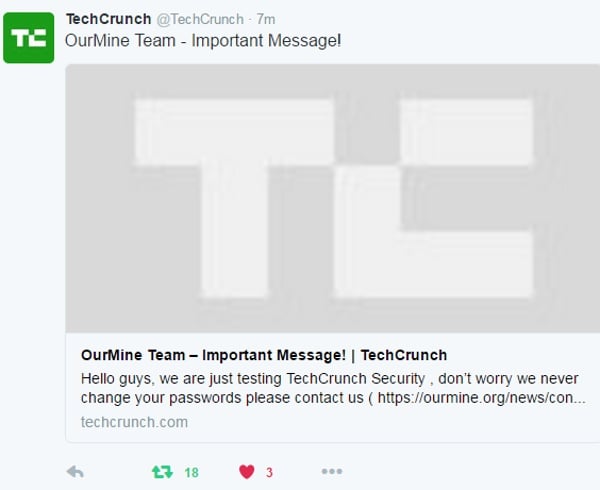
If it can happen to a website as popular as TechCrunch, it might happen to you too.
TechCrunch’s website was compromised by members of the notorious OurMine hacking team this week. The website, like millions of other popular websites, is running WordPress as its content management system.
It appears that OurMine managed to gain access to TechCrunch’s backed after one of the site’s bloggers’ credentials were compromised.
The result? A message from OurMine was briefly published on TechCrunch’s website and even made it to their Twitter account.

Whether the unfortunate TechCrunch blogger’s password was grabbed as the result of one of the recent mega-breaches, phishing or keylogging malware is unclear – but that’s irrelevant to the discussion today.
Because, if your business runs a WordPress website it probably wants to know – how can it ensure that it doesn’t suffer a similar fate to TechCrunch?
It should go without saying that if you are the administrator of a site running WordPress, you should be conscious of the importance of keeping the site secure and up-to-date. Updates for WordPress itself, as well as new patches for third-party plugins are coming out all the time, some of them addressing important security vulnerabilities that could leave your website unguarded if ignored.
Nothing beats asking a WordPress security expert for assistance in protecting your site, but here are some tips on what you could consider doing in order to harden your defences against the most likely way OurMine broke into TechCrunch's website.
Some of the below tips are technical, and we would recommend that you don’t put them into action if you are not experienced with WordPress. If in doubt, get an adult to help you. :)
Change defaults
By default, WordPress creates two login URLs for contributors and administrators to use:
/wp-admin
and
/wp-login.php
These login pages act as the gateway to your website's content management system, so there may be advantages in changing the URLs something less predictable.
TechCrunch has chosen not to change the login URLs on its website, which are freely accessible to anybody on the net.
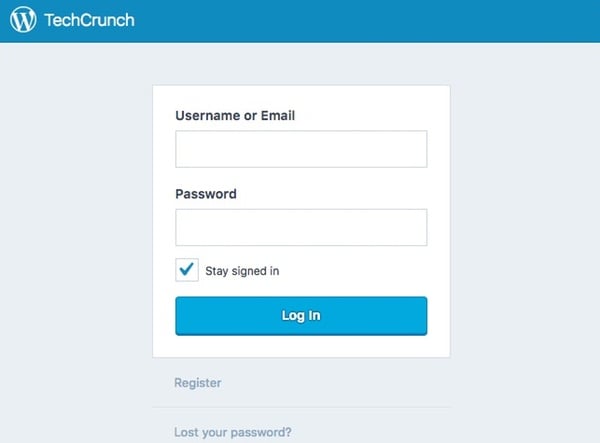
There are WordPress plugins that can help you easily rename your login URLs to something that your staff and contributors know, but that hackers are less likely to guess.
In addition I would recommend avoid having an easy to guess username for your site's administrator. So change it from the likes of 'admin' to something less obvious like 'ZaphodBeeblebrox'.
Passwords
Recent versions of WordPress have become much better at indicating to users whether they are choosing a weak password for their account.
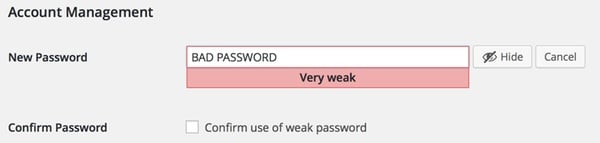
However, it's still possible that users might choose a weak password or have created an account years ago that still has a weak password. Be sure to remind users of the importance of not using the same passwords on different websites, and consider the enforcement of strong passwords that hackers will find hard to crack.
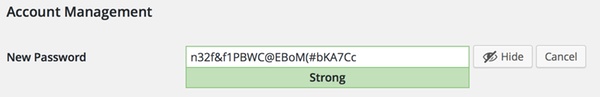
You may even wish to educate your staff and contributors about the benefits of a password manager at the same time. :)
Limit who can login
Consider protecting your login URLs so only whitelisted IP addresses can access your WordPress dashboard. You could also use geo-IP lookups to prevent logins from countries where you know you do not have staff or contributors, or request all users log in after connecting to your company's VPN to prevent unauthorised external access.
Enable 2FA
Enable two-factor authentication on your WordPress login page, forcing users to use an additional form of authentication beyond the traditional username and password. If your WordPress site is defended with a two-factor authentication plugin like Clef, Duo, or Authy, Google Authenticator then hackers are going to have a hard time breaking in without access to the user's mobile phone or hardware token.
Disable XML-RPC
Consider disabling XML-RPC, a technology primarily used to allow users to remotely post content from mobile devices, but that has also been abused by spammers or DDoS attackers in the past.
Where's the WAF?
OurMine's hack was probably achieved through simple credential compromise, but to help prevent other attacks WordPress users might be wise to put a Web Application Firewall (WAF) in place, which can help by blocking malicious requests and attacks on your site such as exploit attacks and visits from blacklisted IP addresses.
Much more advice on protecting sites can be found by reading WordPress.org's article on "Hardening WordPress", and in this great recently-published guide by Yoast.
Make your WordPress site more secure now, and raise awareness about security and sensible password practices amongst your staff and contributors. Because if you don’t, there is the risk that in the future hackers might break into your website, and will have more malicious intentions than OurMine.
tags
Author

Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s, having been employed by companies such as Sophos, McAfee and Dr Solomon's. He has given talks about computer security for some of the world's largest companies, worked with law enforcement agencies on investigations into hacking groups, and regularly appears on TV and radio explaining computer security threats. Graham Cluley was inducted into the InfoSecurity Europe Hall of Fame in 2011, and was given an honorary mention in the "10 Greatest Britons in IT History" for his contribution as a leading authority in internet security.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










