Identifying Security Gaps Using the NIST Cybersecurity Framework: Part 2

In our last post, we explored the vital role cybersecurity frameworks play in guiding organizations as they build and refine their security programs. We introduced the National Institute of Standards and Technology Cybersecurity Framework 2.0 (NIST CSF 2.0), the go-to framework for most organizations, and broke down its six core functions, each designed to help shape a resilient cybersecurity strategy.
But understanding the framework is just the beginning. The real challenge lies in putting it to work—using it to uncover security strengths and expose critical gaps. In this post, we’ll dive into how to leverage NIST CSF 2.0 to conduct a thorough internal assessment, helping prioritize actions and build a stronger defense against emerging threats.
Identifying the Different Parts of the Organization
Today’s organizational environments are vast, spanning numerous services and systems. No longer confined to on-prem corporate offices, organizations are now comprised of a vast network of interconnected networks, applications, services, hosts, users, and devices. While this is part of the NIST CSF 2.0, it’s important to group these into high-level categories in order to begin our assessment. Typically, these areas are grouped into:
1. Physical Premises: All the hardware and physical components that make up the organization that must be secured.
2. Users/Identity: Employee’s accounts/credentials that are basically the keys to the organization’s environment (how they access all the apps and services).
3. Endpoints: The computers, desktops, and laptops used by users.
4. Network: The systems that make up the extra- and intra- network for the company including firewalls and other systems setup to secure it.
5. Servers (on-prem): Any servers that are used and maintained on-prem in a corporate office. Things like Exchange server, databases, storage, etc.
6. Applications (on-prem): Any applications being used that are installed or hosted on-premises or on devices.
7. Custom Applications: These are any applications (whether on-prem or cloud-hosted) that are custom-built by the organization and may not be fully protected by standard, widely available security tools.
8. Cloud/IaaS: Infrastructure as a Service systems such as AWS, GCP, and Azure that organizations utilize to host some or large parts of their organization.
9. SaaS: Any applications hosted online by a third party that the company uses. This can be anything from CRMs like Salesforce to HR systems like Paylocity, to other functional applications used widely across the org (ServiceNow, Atlassian, Slack, Office365 or Google Workspace, etc).
Creating the Rubric for Assessment
The first step in performing an assessment is to establish a standardized grading scale. There are several approaches to this, but one of the most effective is using a matrix with a rating system. The scale can be customized to fit different needs, and here are a few options to consider:
- High Level/Binary Choices: A simple scale that can be used to quickly identify where attention is needed, what can be improved, and what is a strength. This can be comprised of three values:
-
- Weakness/Needs Help: This is an area that needs immediate attention and is a clear security gap/vulnerability that poses a security risk to the organization if not addressed.
-
- Neutral/OK, Cand Improve: An area that has some coverage and is likely enough to not pose a high-security risk to the organization but would benefit from a re-evaluation when the time allows after security gaps are addressed.
-
- Strength/Well Covered: An area of strength that is well covered with proper planning, systems, and tools deployed to provide good coverage minimizing security risks.
- Number Rankings: A more detailed and defined way of assessing each area. The scale can be anything, 1 to 5, 1 to 10, 1 to 100, etc (where 1 is weakest and the top number is the strongest or well covered). The point is to create a scale that can be used to clearly identify where each area of the cybersecurity program is rated and then use that scale to prioritize the work and investment required to improve security and reduce risks and vulnerabilities. The Capability Maturity Model Integration (CMMI) has a good rubric on a 1 to 5 scale where each ranking is clearly defined.
Now with the grading scale in hand, we can create the system we will use to perform the assessment. For this next step I would recommend using a matrix to separate each of the different organizational areas for grading.
The Cybersecurity Defense Matrix
The Cyber Defense Matrix is a widely recognized and effective method for mapping an organization’s structure against the NIST functions. This matrix offers a clear way to visualize how each part of the organization aligns with the six primary NIST CSF functions, helping to identify strengths and gaps. 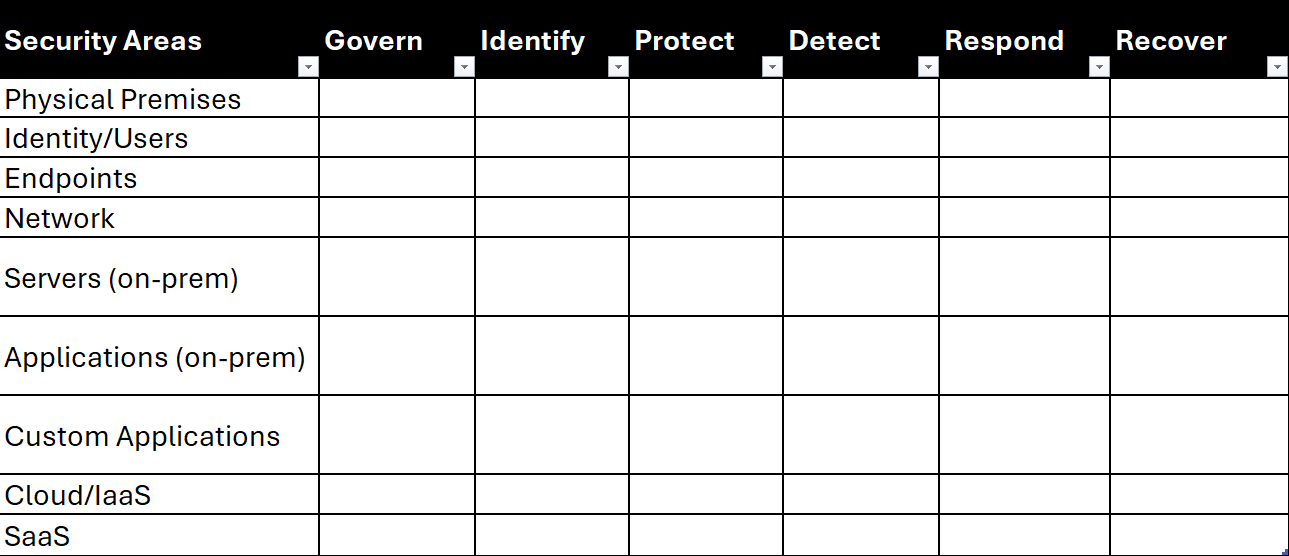
Using a matrix lay out the six primary functions of NIST CSF 2.0 across the top and then have each of the internal areas of focus down the side. This can be used as a high-level way to rate and assess each area overall compared to the NIST functions using the grading scale decided on above. Assess each of the category areas by NIST CSF 2.0 function and apply a grade based on the results of the assessment.
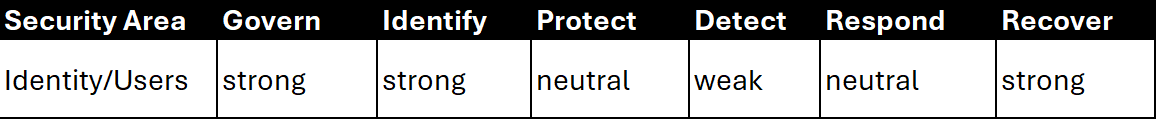
For instance, if the high-level rating system is used, the organization can assess how well each area is covered. For example, are there effective plans and systems in place to identify, manage, and track user accounts (e.g., through an identity provider or management tool)? If so, this would be marked as a strength. The same process would then be applied across the other areas, resulting in a comprehensive assessment similar to the example above.

Conversely, if we chose a full number rating system—such as a 1-10 scale where 1 is weak and 10 is strong—we can apply a more detailed assessment to each area. For example, when evaluating the Detect function, we might acknowledge that while some tools are in place, they’re noisy, and we lack the in-house manpower to fully monitor them. Even if someone on our team noticed an alert, they might not have the expertise to respond effectively. In this case, we’d rate ourselves on the lower end, recognizing that while something is in place, it’s not enough to consider this area neutral, and it would be a priority to address.
If choosing to do the more granular rating system, it might be helpful to build out additional matrices that cover each of the individual NIST functions on their own. We can then create a matrix listing out each of the individual categories of the function (or even subcategories too if we want to get that granular) across the top and then the organizational areas down the side. For example, the Protect function has 5 categories under it, so a dedicated matrix for Protect would look like:
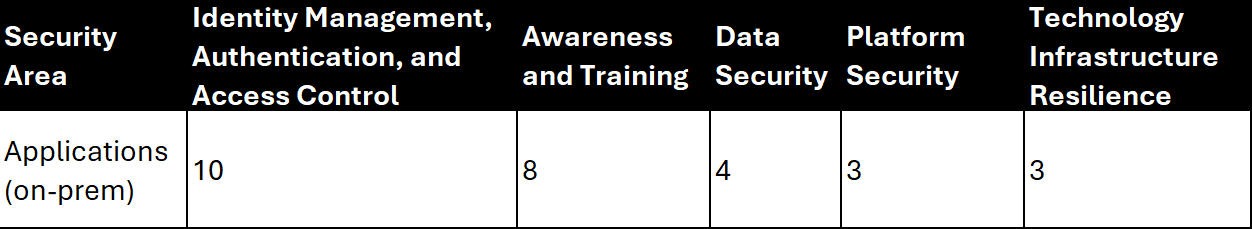
With this matrix we can break down the Protect function into categories to see which parts of Protect we have covered and which we don't. For example, in the matrix above looking only at Applications (on-prem), we have a good processes and systems in place for managing user identity and access to those applications as well as security training for our internal security team and org, but maybe we don’t have the best tools and plans in place for data and platform security as well as infrastructure resilience. Using this we can then help prioritize those later 3 categories to ensure we can create a plan and implement a process and the necessary tools and other requirements to fill that security gap.
Using these matrices can take a lot of time and require a lot of work, focus, and input from multiple parts of the organization. In the examples above I showed a zoomed in view for just one sample area of the organization and one NIST function. But to properly create a functional and successful cybersecurity program requires a realistic and honest assessment of the entire organization. Without a full understanding of what needs to be protected and where the security gaps are, it will be impossible to create a successful plan to secure those areas to help prevent threats.
In House or Outsourced?
With our matrices filled out and a fairly accurate assessment of our organization in hand, we can now start the real work in this process...deciding how to move forward. The biggest decision when reviewing each area is to determine what must be done in-house, what can or should be outsourced and what can be co-managed alongside a trusted partner. To get a better idea of what I mean, here’s a few examples:
- In-house: Things that cannot be outsourced to third party organizations and must be handled or maintained internally for a variety of reasons. This could be because it involves extremely sensitive data or intellectual property or could be related to complex internal processes and organizational structure. For example, much of the Govern function and its associated categories are things that must be kept in house. It’s about how the organization views and oversees the other functions so these are all about internal discussions and decisions (such as when to keep functions in house or outsourced). Another example could be Asset Management. This is likely something that is best and more easily done in-house due to the oversight requirements and day-to-day work involved rather than outsourcing to a third-party security company.
- Outsourced: These are different areas of focus that could be fully outsourced to a third-party security organization due to internal limitations or a strategic decision. For example, lack of resources, time, or staffing may lead organizations to seek third-party help to provide assistance or coverage in certain areas. Threat research and intel are often outsourced whether by subscribing to threat intel feeds or relying on threat intel platforms. Organizations also often partner with Managed Service Providers or cybersecurity consultancies to offload other responsibilities or seek help.
- Co-managed: These can be a variety of areas that could easily fall into either of the other two categories. Similar to reasons for fully outsourcing, due to resource limitations, companies might look to partner with a trusted third-party security organization for assistance and to co-manage a particular area. A great example would be threat detection and response. While many services like Managed Detection and Response (MDR) help supplement this area, the best approach is to treat it like a partnership. The MDR can help handle the majority of the alert and event monitoring, but the organization should still have a role in reviewing the information sent by the MDR. In addition it’s beneficial for organizations to work alongside MDR vendors to inform them about their company, how it works, how users typically work, the type of assets they are covering in order for the MDR vendor to have a better understanding of the cybersecurity landscape and environment to enable them to make the most informed decisions when monitoring security tools and events.
With our three categories defined, we can then mark each cell in our matrices with how that area of focus will be handled. We can do this by either writing it out, or possibly a little easier, applying a color code to each of these 3 options. For example:
- In-House – Green
- Outsourced – Red
- Co-managed – Blue

In the example above, we took our Endpoint matrix example and color coded it while leaving our ratings in. We can see that we decided to keep Govern, Identify, and Recover all in house as these are things that can be hard to outsource or even co-manage and, in the case of Govern and Identify, we were already well covered to begin with. For detection, i.e. most of the threat monitoring, we decided to fully outsource to an MDR but that we would co-manage the processes and deployments as well as the response with that MDR or trust security partner.
What’s Next?
The fun part? In reality the next step, once a plan is in process and we have decided in-house, co-managed, or outsourced, is to decide the who, what, when, and how. I.e. we need to pick the tools that we will invest in, which security vendor would be the best to help our organization, and in what order we should prioritize our investments. Over the final 3 blog series, we’ll dive into the 3 parts of the attack phase covered in part 1 (prevention, active threat, post threat). In part 3 we’ll begin with the first section – prevention.
If you're looking to get your cybersecurity journey started, check out how Bitdefender's security platform can help you. Read up on our GravityZone XDR solution or learn how our MDR service can help empower your team.
tags
Author

Kevin is the Principal Product Marketing Manager at Bitdefender. With a technical background, he excels at storytelling and messaging across a variety of cybersecurity fields.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











