"Unauthorised code" on Juniper firewalls gives attackers admin access, decrypts VPN traffic

With many companies shutting down for the holidays, chances are that the IT team at your business are running - if anything - a skeleton staff and many are hoping to have a relaxing Christmas and New Year break.
Sadly a bombshell security announcement from firewall manufacturer Juniper Networks may have just put paid to that.
Within ScreenOS, the firewall management operating system used by Juniper Networks in its high-end enterprise NetScreen devices, there sits a backdoor, giving attackers access to admin functions and the ability to decrypt supposedly-secure encrypted VPN traffic.
And it appears the problem may have been present in Juniper firewalls for years.
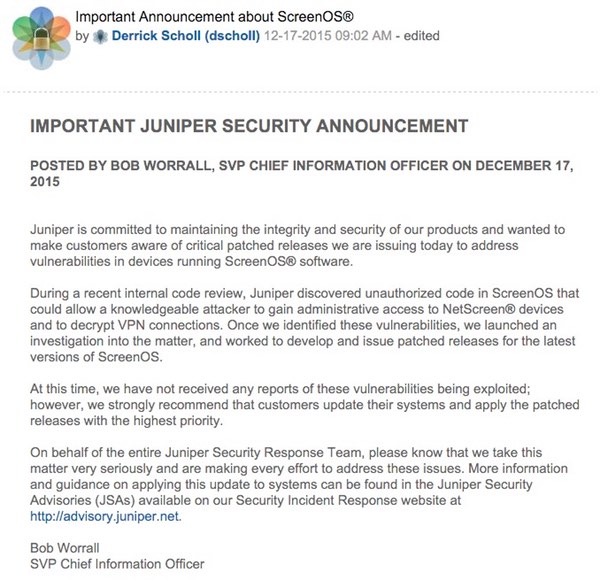
"During a recent internal code review, Juniper discovered unauthorized code in ScreenOS that could allow a knowledgeable attacker to gain administrative access to NetScreen® devices and to decrypt VPN connections. Once we identified these vulnerabilities, we launched an investigation into the matter, and worked to develop and issue patched releases for the latest versions of ScreenOS."
"At this time, we have not received any reports of these vulnerabilities being exploited; however, we strongly recommend that customers update their systems and apply the patched releases with the highest priority."
In a separate Juniper knowledgebase article, the company warns that there is no way to detect that the VPN-snooping vulnerability has been exploited and that skilled attackers would likely be able to cover their tracks if they had managed to gain remote administrative access.
The fact that Juniper describes in its security advisory that it found "unauthorised code" immediately sets off alarm bells. That wording strongly suggests that the backdoor wasn't the result of a programming bug, but was instead placed in the operating system by saboteurs.
In the wake of Edward Snowden's revelations in recent years, it's understandable that many may view the tampering as the likely work of an intelligence agency such as the NSA.
They do, after all, appear to have a track record in covertly tampering with network gear before it arrives on customers' sites.
But sneaking unauthorised backdoor code into an operating system used by thousands of large companies around the world to protect themselves from unwanted access from the outside is all the more audacious, and appears to back up a claim made by Der Spiegel two years ago that Juniper's products were being targeted.
So what does this mean to your business?
Well, your company's private, confidential communications may have been monitored, and unauthorised parties could have had remote access to your firewalls.
That's a pretty scary thought and although Juniper has no evidence that the problems have been exploited, the dangerous backdoor appears to have been present in the company's products for years, without it knowing. Trust will undoubtedly have been shaken by this revelation.
All NetScreen devices using ScreenOS 6.2.0r15 through 6.2.0r18 and 6.3.0r12 through 6.3.0r20 are affected by the issues and require patching. Juniper strongly recommends that all customers update their systems and apply these patched releases with the highest priority.
So much for a relaxing holiday, eh?
tags
Author

Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s, having been employed by companies such as Sophos, McAfee and Dr Solomon's. He has given talks about computer security for some of the world's largest companies, worked with law enforcement agencies on investigations into hacking groups, and regularly appears on TV and radio explaining computer security threats. Graham Cluley was inducted into the InfoSecurity Europe Hall of Fame in 2011, and was given an honorary mention in the "10 Greatest Britons in IT History" for his contribution as a leading authority in internet security.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











