Microsoft: Phishing Attacks Increased 250% from January to December 2018

Phishing remained a preferred attack vector in 2018, with hackers ramping up their efforts by 250% between January and December. Phishing attack methods have also evolved in recent times, as bad actors are forced to bypass increasingly efficient anti-phishing tools and techniques.
Phishing campaigns – which place “lures” inside devious emails to trick recipients into handing over passwords or other sensitive data – have always been an effective attack avenue for cybercriminals. For one, phishing campaigns are very cost-effective. Secondly, they capitalize on the human factor, and research shows staff negligence abounds in virtually every industry. And, as anti-phishing mechanisms evolved, so did adversaries’ methods.
In its latest security intelligence report, Microsoft says attackers continue to use phishing as a preferred attack method. In fact, detections rose 250% between January and December 2018, the software giant noticed after analyzing more than 470 billion email messages every month for phishing and malware.
“Phishing promises to remain a problem for the foreseeable future because it involves human decisions and judgement in the face of persistent efforts by cybercriminals to make victims fall for their lures,” according to the Windows maker. “As the tools and techniques used to protect people from phishing become more sophisticated, attackers are forced to adapt themselves.”
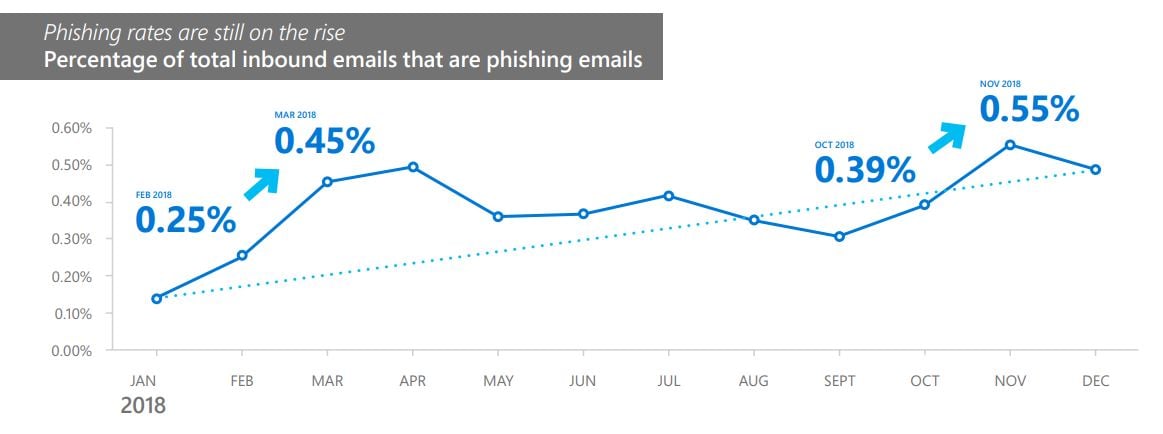
Credit: Microsoft
One key measure undertaken by bad actors has been to make their campaigns polymorphic, in that they used a varied infrastructure (instead of a single URL, domain or IP to send email) with multiple points of attack. Another trend involves a shift from short-span attacks to longer high-volume campaigns. Attackers also increasingly use hosted infrastructure and other public cloud infrastructure. This makes it easier to avoid detection by hiding among legitimate sites and assets.
“For example, attackers increasingly use popular document sharing and collaboration sites and services to distribute malicious payloads and fake login forms that are used to steal user credentials,” according to the report.
Compromised accounts have also been used more often in distributing malicious emails. And, depending on the entity in the attackers’ crosshairs, phishing campaigns range from “targeted" (i.e. spear phishing) to “generic.”
Microsoft offers a list of seven phishing “lures” that businesses and regular users alike should watch out for:
- Domain spoofing (the email message domain is an exact match with the original domain name)
- Domain impersonation (the email domain is made to look like the original domain name)
- User impersonation (the email appears to come from someone you trust)
- Text lures (the text appears to come from a legitimate source such as a bank, government agency, or other company and typically asks the victim for sensitive information such as usernames, passwords or sensitive financial data)
- Credential phishing links (the email links to a page that resembles a login page for a legitimate site, so users will enter their login credentials)
- Phishing attachments (the message contains a malicious file attachment)
- Links to fake cloud storage locations (the email appears to come from a legitimate source and entices the user to give permission or enter personal information to access a fake cloud storage location)
While phishing also remains a top attack avenue to deliver zero-day payloads, Microsoft says it’s actively hardening against these attacks with additional anti-phishing protection, detection, investigation and response capabilities.
tags
Author
Filip is an experienced writer with over a decade of practice in the technology realm. He has covered a wide range of topics in such industries as gaming, software, hardware and cyber-security, and has worked in various B2B and B2C marketing roles. Filip currently serves as Information Security Analyst with Bitdefender.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks

.jpg)









