Shellshock two years on – has your company forgotten about it?

It’s just over two years since a critical Shellshock vulnerability was uncovered.
The Shellshock vulnerability (sometimes known as “the Bash bug”, and more technically as CVE-2014-6217) could be exploited by remote hackers to execute malicious code on vulnerable systems, potentially hijacking them for nefarious purposes.
Astonishingly, the bug had been present in most Linux and UNIX distributions for about twenty years without anybody noticing. But news of the flaw and how simply it could be exploited had experienced users and system administrators racing to update their systems to patch against the flaw.
So, with patches available two years ago it would be nice to think that we didn’t have to worry about Shellshock anymore wouldn’t it?
Unfortunately, new research released by IBM reveals that not only is Shellshock not dead – it’s actually currently on the rise, with over 20,000 Shellshock scans detected in the single month of September 2016:
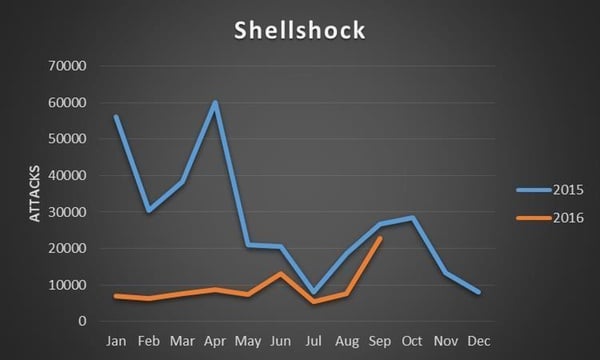
“As though in anticipation of its anniversary, Shellshock attack activity recently surged to levels not seen since 2015. As of Sept. 22, the month of September accounted for more than 26 percent of the total activity recorded in 2016.”
“A little over 70 percent of the attack traffic originated in the U.S., whereas another 18 percent comes from Australia. Top targets of these attacks, according to IBM MSS data, include organizations located in U.S. (26 percent), Japan (18 percent), India (16 percent) and Brazil (11 percent).”
When looking at the types of industries that have been targeted, it’s the IT and communication sector that tops the list – accounting for some 46% of all Shellshock attacks – followed by financial services (26%) and manufacturing (16%).
According to the researchers, this makes sense because of the fact that major telecoms and IT companies often have Linux-based environments as part of their infrastructure.
Meanwhile, in the manufacturing sector there might be particular difficulties and nervousness in updating critical systems, such as ICS and SCADA hardware, which may be leaving them unpatched.
The key, of course, is for all businesses to adopt a policy of timely patch management, as leaving systems vulnerable to known threats is playing a dangerous game of Russian Roulette with your infrastructure and data.
Chances are that there will always be vulnerable systems out there, and that even today online criminals are continuing to discover unpatched systems ripe for exploitation.
So don’t put your head in the sand, patch your systems.
Furthermore, ensure that you have a layered defence in place to provide additional levels of protection, and increase the chances of preventing a threat reaching the critical parts of your organisation.
Because sometimes the threat you have to worry about most is not the one that is making the sexy breaking headlines today, but the one which was discovered two years ago, has been mostly forgotten, but is still lurking out there on the net…
tags
Author

Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s, having been employed by companies such as Sophos, McAfee and Dr Solomon's. He has given talks about computer security for some of the world's largest companies, worked with law enforcement agencies on investigations into hacking groups, and regularly appears on TV and radio explaining computer security threats. Graham Cluley was inducted into the InfoSecurity Europe Hall of Fame in 2011, and was given an honorary mention in the "10 Greatest Britons in IT History" for his contribution as a leading authority in internet security.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










