Speed Up Incident Investigation and Resolution with Network Traffic Analytics

The effectiveness of security incident investigation and resolution is key to the effectiveness of all defense efforts. But improving incident investigation and resolution does not come without challenges: Too many alerts to handle and poor correlation between alerts.
Network Traffic Analytics (NTA) addresses these challenges and accelerates incident investigation and resolution by:
- Improving the quality of security alerts
- Providing better correlation between alerts
Improving the quality of security alerts
Although an excess of alerts is among the most important challenges Security Analysts and Security Operating Centers (SOC) face, only 54% of respondents in the 2018 Security Operations Center Survey by SANS Analyst Program collected SOC metrics. Organizations missing SOC KPIs have trouble adjusting their skill level, processes and tools to ensure proper handling of all security incidents.
How many security incidents are too many to handle? This varies from organization to organization, but the outcome of alert fatigue seems to be the same: around 30% of alerts globally are simply ignored.
These alerts are ignored mainly for 2 reasons:
- The sheer number of alerts
- The quality of these alerts
What can be done? The quest to increase the efficiency and effectiveness of incident investigations must start by improving the quality of alerts and reducing their number. Most devices in the environment, from end-user devices to servers, switches, routers or firewalls, generate some sort of alerts. But which ones should take priority? Which ones, if ignored or not investigated promptly, pose the highest risk.
Alerts generated by Network Traffic Analytics solutions are arguably more likely to be relevant than alerts generated by other elements. In a recent blog post on RSA 2019, ESG senior analyst said “ESG research indicates that network security monitoring is most often the center of gravity for threat detection. In other words, SOC analysts detect suspicious activity on the network first and then pivot elsewhere for further investigation... CISOs can get a big bang for their buck by implementing one of the more modern network security monitoring/analytics tools”
Should the other alerts be ignored? Absolutely not. But using NTA as the sentinel of your organization reduces the workload and improves the effectiveness of incident investigation. It will not completely eliminate the problem of alert overload, but choosing a more reliable signal source can help overcome the challenge of noise.
Better alert correlation
Only 30% of organizations rely on fully automated or mostly automated alert correlation. The other 70% are manually triaged. Amid the current severe shortage of skilled cybersecurity industry workers, this situation doesn’t look good at all.
There are multiple approaches to the alert triage problem, including efforts from SIEM (Security Information and Events Management) and SOAR tools (Security Orchestration Automation and Response). While a SIEM solution ingests loads of alerts and tries to make sense of them, NTA solutions work with the initial source: the network traffic. By directly analyzing network traffic and correlating dozens or hundreds of events from the environment, NTAs can generate a crisp, complete picture of each security incident.
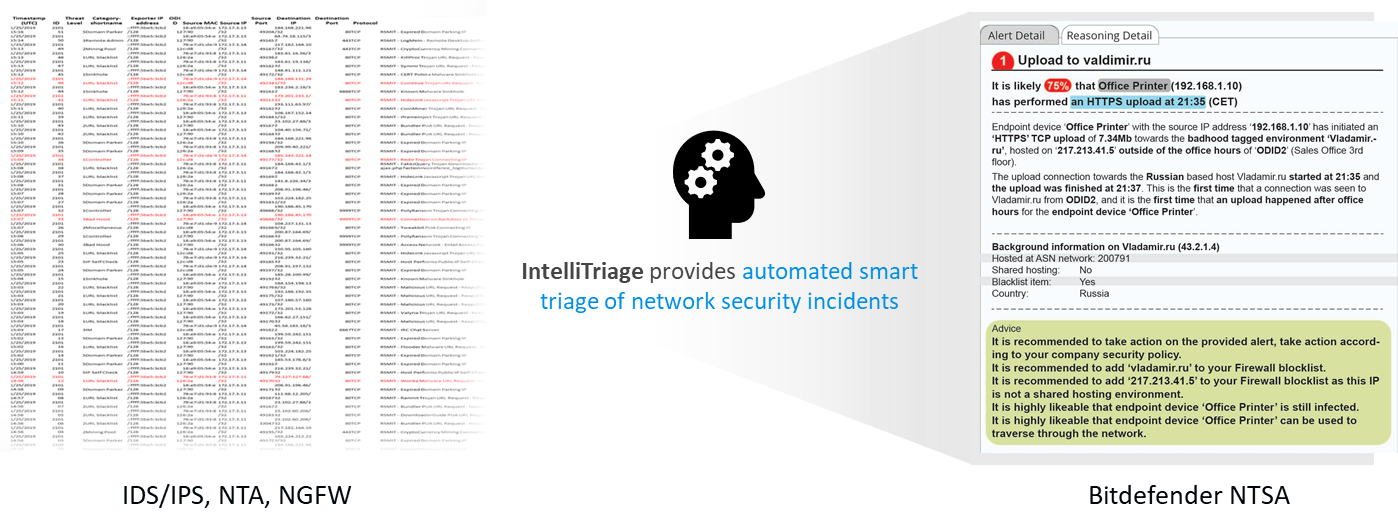
Bitdefender Network Traffic Security Analytics (NTSA)
Bitdefender NTSA provides a clear understanding of threat-related network activity using a collection of all network meta-data information (data about network flows instead of communication content) and automates security incident triage with NTSA IntelliTriage. IntelliTriage combines ML, behavioral analytics and complex detection scenarios with Bitdefender threat intelligence to automatically triage security incidents and provide recommended incident response.
Using IntelliTriage, SOC analysts can dramatically reduce the time it takes to investigate incidents and hunt.
Want to know more?
Join our on-demand webinar to learn more about how to reduce security incident investigation and resolution time with Network Traffic Analytics. We also recommend visiting the Bitdefender Network Traffic Security Analytics webpage to gain insights into how NTA can reduce your cyber risk exposure by providing complete visibility on all threat-related network activity.
Resources:
The Definition of SOC-cess? SANS 2018 Security Operations Center Survey, by Christopher Crowley and John Pescatore - August 13, 2018 https://www.sans.org/reading-room/whitepapers/analyst/membership/38570
tags
Author

Acting Cybersecurity Professional and Product Marketing Director at Bitdefender, Bogdan has extensive international experience in various roles across IT Industry, including IT Systems Integration, Cybersecurity, Sales Engineering, and Product Management. He enjoys combining his engineering background with industry knowledge and business sense to fulfill his professional mission: help businesses grow by leveraging technology.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










