800,000 DrayTek routers at risk of DNS hijacking attack - update your firmware!

Router manufacturer DrayTek has issued a warning that several of its wireless routers are at risk of exploitation by hackers, after a vulnerability was discovered that could let an attacker remotely change the devices’ DNS and DHCP settings.
What that means is that a criminal could redirect web traffic via a rogue DNS server under their control to bogus websites, replace adverts on legitimate sites, or even block your access to security updates.
DNS hijacking attacks are insidious, partly because a hacker might only *occasionally* direct you to a rogue site, meaning that your web browsing works normally for most of the time and reducing the chances of raising suspicion.
DrayTek customers would be wise to not only update their firmware, but also check their router’s DNS settings straight away.
The manufacturer advises that an indicator that your router may have been compromised is if its DNS settings have been configured to use a known rogue DNS server at 38.134.121.95.
Instead your DNS settings should be either blank, set to the DNS server addresses from your ISP, or a well-known DNS server such as the one run by Google at 8.8.8.8
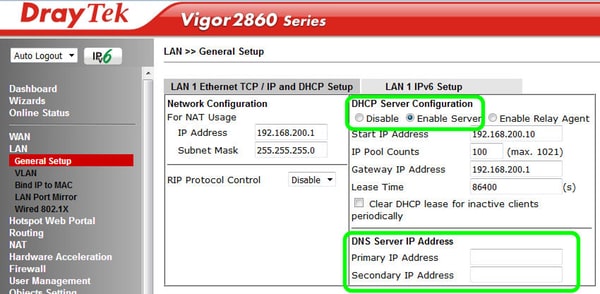
There is lots more good advice in DrayTek’s security advisory, including the recommendation to change your passwords on any websites that you may have logged into recently, in case the attackers managed to phish your credentials through the DNS hijacking.
Security researcher Kevin Beaumont tweeted that in a search via Shodan he found 790,423 impacted DrayTek routers, with the largest proportion being located in the United Kingdom and the Netherlands.
Thankfully, patches are now being rolled out by DrayTek, and customers would be wise to install firmware updates for the following affected devices:
- Vigor 2760 Series
- Vigor 2762 Series
- Vigor 2830db
- Vigor 2830nv2
- Vigor 2830sb
- Vigor 2832 Series
- Vigor 2850 Series
- Vigor 2860 Series
- Vigor 2862 Series
- Vigor 2920 Series
- Vigor 2925 Series
- Vigor 2926 Series
- Vigor 2952
- Vigor 3200 Series
- Vigor 3220
- VigorBX 2000
DrayTek devices that are unaffected by the exploit are its VigorAP wireless access points, VigorSwitch network switches, and the following Vigor routers: 2950, 2955, 2960, 3900, and 3300.
DrayTek says that it advises customers to always use the latest firmware to ensure they have the latest features as well as “vital security improvements”, regardless of whether you are using one of the vulnerable routers or not.
The company goes on to remind users that “critical updates should be deployed immediately”.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








