New Android Security Feature Aims to Keep Snoops Out of Your Phone

Google introduced an important security feature for its users this week, making it harder for snoops to access data stored on Android phones.
“Google System updates make your Android devices more secure and reliable, and give you new and useful features,” says the tech giant. “They include updates from Google to the Android operating system, Google Play Store, and Google Play services.”
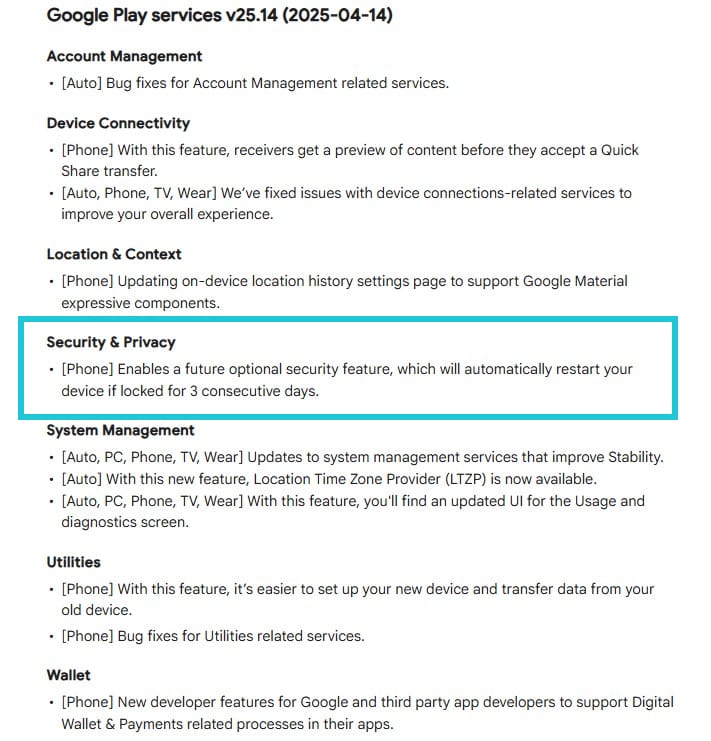
The latest Google Play services update (version 25.14) includes the usual bug fixes and enhancements in areas like Account Management, Device Connectivity, Location & context, Security & Privacy, System Management, Utilities, and Wallet.
In the Security & Privacy department, Google mentions a notable new addition – a security feature designed to keep prying eyes out of your Android phone.
Auto-reboot after 3 days of inactivity
With the new Google Play services v25.14, Android phones automatically reboot after 3 days of inactivity:
Enables a future optional security feature, which will automatically restart your device if locked for 3 consecutive days.
Source: support.google.com
The feature, already deployed by Apple for iPhone users, aims to make it harder to extract data from a device – for example, in the context of digital forensics (or abuse thereof).
Rebooting sends the phone into BFU (Before First Unlock) mode, which refers to the device’s cryptographic state relative to when the user first unlocks the device with a valid PIN or biometrics, after a reboot.
In BFU mode, data extraction is heavily constrained. While certain files or partitions can still be accessed – typically those not fully protected by the user’s credentials (for example, some logs or metadata) – the core user data remains encrypted and inaccessible to snoops.
This is in contrast to AFU (After First Unlock) mode, which refers to the period after a valid credential has been entered to unlock the phone. In this state, the phone’s critical cryptographic keys for protected storage are loaded into memory. Forensic tools are designed to pluck those keys and decrypt the data as needed—either by investigators or abusers. Since there’s no way to know the purpose of the data extraction, Google is making an extra push to prevent abuse.
The fight against spyware
Last year. security researchers discovered spyware covertly implanted on the Android phone of a Russian programmer who’d been held in custody by Russian authorities for supplying monetary aid to war-stricken victims in Ukraine.
Authorities had physical access to his phone after obtaining the passcode to unlock it.
Read: ‘Security Service Installed Spyware on My Phone,’ says Programmer who Fled Russia
Apple, Google, and Meta, Facebook’s parent company, have been fighting mercenary spyware for years.
Apple last year announced it was dropping its legal tussle with Pegasus spyware maker NSO Group to avoid disclosing the threat intelligence it has developed over the years to fight its monitoring software.
Since many spyware infections also occur remotely – with no need for physical access to the device, and sometimes with no input from the victim – Bitdefender recommends keeping your device up to date with the latest vendor-issued security patches as the first important step against infection - especially if you consider yourself a target.
Read: How Spyware Infects Smartphones and How to Defend Against It
Google and Apple issue periodic security updates designed to close holes exploited in commercial spyware attacks. For peace of mind, run a dedicated security solution on all your personal devices.
You may also want to read:
WhatsApp Patches Zero-Click Spyware Attack Vector on Android
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








