Apple Issues Emergency iOS 18.3.1 Update to Plug ‘Extremely Sophisticated’ Attack Vector on iPhones and iPads. Patch Now!

Apple has issued iOS 18.3.1 as an emergency update addressing “an extremely sophisticated” bypass of its iOS safeguards.
Just two weeks after plugging the first important security hole of the year, Apple this week issued an even more urgent security notice for iDevice owners, warning that “this issue may have been exploited in an extremely sophisticated attack against specific targeted individuals.”
According to the advisory, a motivated hacker with physical access to a vulnerable iPhone or iPad could bypass security restrictions to gain access to the device’s contents.
USB Restricted Mode
In 2018, with the release of iOS 11.4.1, Apple introduced a security mechanism called USB Restricted Mode which prevents tethered access to an iPhone’s content if the phone has not been unlocked and connected via cable within the past hour.
The feature, seen as a blow against abusive use of digital forensics tools, was designed to prevent data extraction outside law enforcement purposes.
Read: FBI Hacked Trump Shooter’s Phone in 40 Minutes Using ‘Unreleased Technology’
But according to this week’s advisory, abusers have apparently found ways to bypass the restriction.
“A physical attack may disable USB Restricted Mode on a locked device,” according to the security advisory for iOS 18.3.1 and iPadOS 18.3.1.
“Apple is aware of a report that this issue may have been exploited in an extremely sophisticated attack against specific targeted individuals,” reads the notice.
Spyware crusaders to the rescue
Apple credits Bill Marczak of The Citizen Lab at The University of Toronto’s Munk School for discovering and reporting the vulnerability. The Canadian cybersecurity outfit is notorious for its crusade against spyware makers exploiting zero-day vulnerabilities in Apple’s iOS and Google’s Android mobile operating systems.
The Cupertino tech giant doesn’t point fingers at any group of wrongdoers. Historically, this type of wording is typically a response to state-sponsored hacks of the iPhones of political activists, dissidents, journalists, free speech advocates, and pretty much anyone picking a bone with a regime.
The most recent example came in December last year, when the same Citizen Lab discovered spyware covertly implanted on the phone of a Russian programmer who’d been held in custody by Russian authorities for supplying monetary aid to war-stricken victims in Ukraine.
Read: ‘Security Service Installed Spyware on My Phone,’ says Programmer who Fled Russia
Update your iGear!
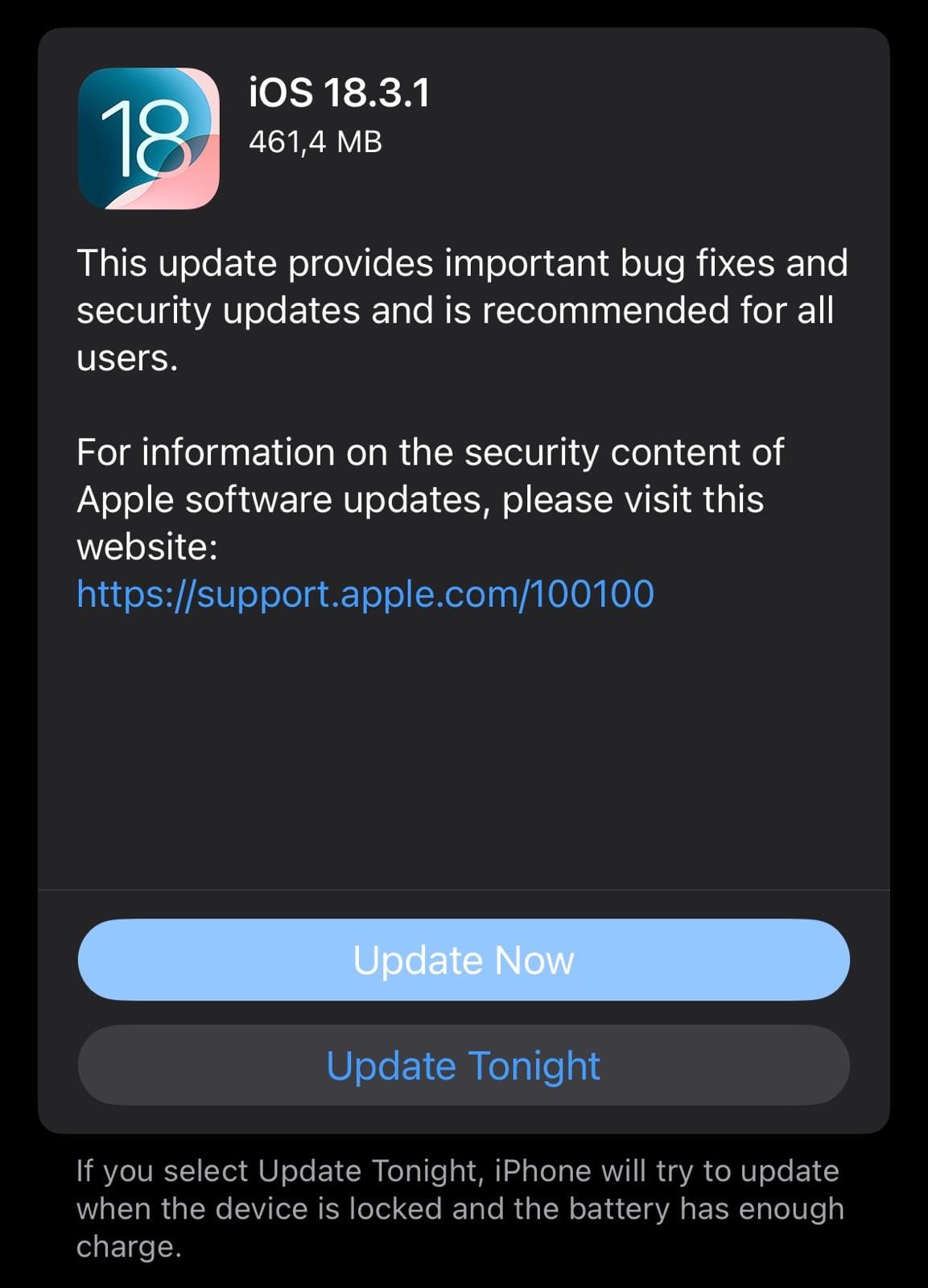
While such warnings typically address high-profile targets, keeping your iDevice updated to the latest version is always a good idea.
As we note in our latest security guide for iPhone users, Apple’s proverbial walled garden has long been lauded for its robust security, thanks to a tightly controlled ecosystem, a strict app review process, and timely software patches. As we move further into 2025, though, advanced cyber threats targeting Apple users – especially iPhone users – persist.
Read: 10 Cyberthreats iPhone Users Can’t Afford to Ignore in 2025
As of today, you want to be on iOS 18.3.1 and iPadOS 18.3.1 – available for iPhone XS and newer models, and most iPads currently in circulation today. Simply navigate to your Settings menu, choose General, Software Update, and let your iPhone or iPad fetch the latest version from Apple’s servers. When prompted, tap Update Now and wait for the update process to cycle through.
iPadOS 17.7.5 is also available with the same emergency fix for some older iPad models, including the iPad Pro 12.9-inch 2nd generation, iPad Pro 10.5-inch, and iPad 6th generation.
For peace of mind, run a dedicated security solution on all your personal devices. On iOS and macOS, keep the trusty Lockdown Mode toggle handy whenever you believe hackers might be targeting you.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








