Bitdefender Labs warns of Agent Tesla phishing campaign

Bitdefender Labs has spotted a malicious phishing campaign trying to infect users with the infamous Agent Tesla remote access Trojan.
The malspam campaign tries to sneak the malicious payload through in the guise of a price quotation request (which comes as an attachment) from what seems to be a South Korean company in the mining and metals industry.
A closer look at the delivery address, however, shows the delivery domain of the phishing emails impersonating an oil and gas group in Kazakhstan.
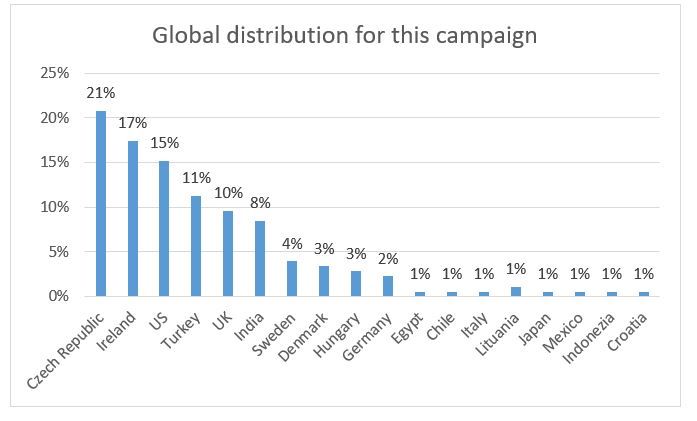
Most of the attacks seem to have originated from IP addresses in the Netherlands (42%) and the United States (38%), with telemetry showing a global dispersion of the malspam campaign:
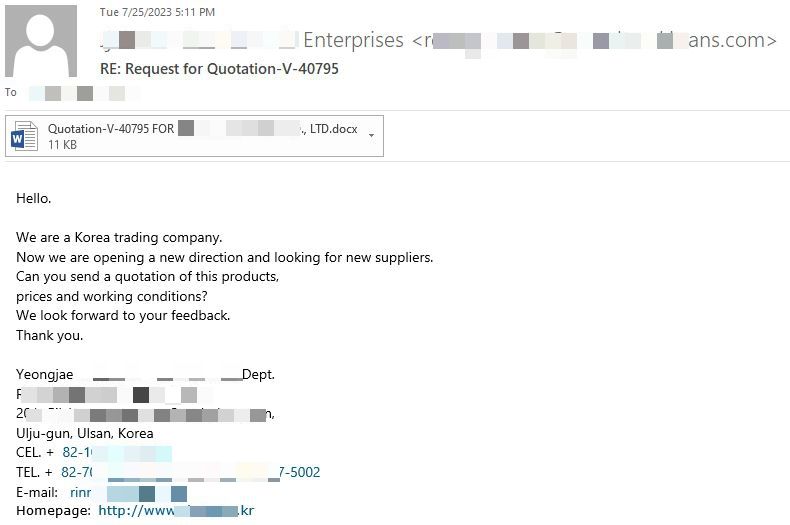
The messages are designed to look like an inconspicuous business email asking the recipient to provide a potential customer or supplier with more information and costs for particular goods and services listed in the attachment.
“Hello. We are a Korea trading company.
Now we are opening a new direction and looking for new suppliers.
Can you send a quotation of this products,
prices and working conditions?
We look forward to your feedback.
Thank you.”
The malicious attachment is, in fact, an RTF document exploiting the CVE-2018-0802 vulnerability. It contains 3f1f8ef6e454f2631b42c29a0ac1c4aa linking to an external link http://87.121.221[.]212/yugozx.doc. When accessed it will prompt the download of Agent Tesla Malware to the victim’s machine.
Indicators of Compromise
- 3f1f8ef6e454f2631b42c29a0ac1c4aa
- http://87.121.221[.]212/yugozx.doc
Once Agent Tesla is deployed onto the infected machine, the malicious software begins collecting sensitive information from the system, exfiltrating data via the SMTP protocol (email) back to an email account registered in advance by the attackers or to a Telegram account.
Agent Tesla infections primarily spread through phishing campaigns. The well-known data stealer, often seen in malware-as-a-service offerings by cybercriminal groups, is also known to be a first-stage malware in an attack, as the remote access Trojan gives criminals remote access to any compromised systems and allows them to deploy more sophisticated or devastating attacks, such as ransomware.
Agent Tesla is an attractive choice for threat actors and it can be delivered in different forms of attachments including .zip, .cab, .msi, .img and Microsoft Office documents.
In this particular campaign, the attackers don’t seem to have put much work into the tone of the visual template of the message, most likely hoping that recipients would, out of curiosity, check the bogus attachment.
Bitdefender detects the attachment as Trojan.GenericKD.68349949.
How can you protect against Agent Tesla attacks
The best way to mitigate and protect against malicious attacks including Agent Tesla infections is to install a security solution on your device that can detect and block malware from spreading on your devices and network.
Since the remote access Trojan is designed to steal login credentials from machines and give attackers access to sensitive accounts and data, users should enforce MFA wherever possible in case of compromise.
Of course, users should always brush up on ways to spot phishing attempts and always verify the validity of messages before accessing any attachments, and make sure to patch any used software.
Bitdefender Total Security provides robust anti-malware protection against e-threats, including Agent Tesla across all major operating systems. The real-time protection feature included in our security software offers continuous protection against all e-threats, including viruses, worms, Trojans, ransomware, zero-day exploits, rootkits, and spyware to keep you and your data safe.
tags
Author
Alina is a history buff passionate about cybersecurity and anything sci-fi, advocating Bitdefender technologies and solutions. She spends most of her time between her two feline friends and traveling.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








