Content Creators: How Hackers Steal Your Account

Online accounts are the livelihood of every content creator. Whether it's YouTube, Instagram, or TikTok, losing control of these social media accounts can have devastating consequences. Hackers are growing increasingly sophisticated, using a method known as account takeover (ATO) to target creators like you.
This article explains how hackers steal your account, detailing the attack chain and offering critical insights on how to protect yourself.
How the Attack Chain Works
Hackers use a multi-step process to take over creator accounts:
1. Information gathering – In this initial phase, hackers uncover vulnerabilities and gather personally identifiable information (PII) such as your email address and phone number, and even details about your content or brand partnerships. Many creators make this kind of information accessible through social media profiles, public interviews, or websites, allowing hackers to tailor a convincing attack.
2. Setting the bait via a well-crafted phishing email – Phishing remains a highly effective way for cybercriminals to hack creator accounts. The unsuspecting content creator receives what appears to be an email from a potential sponsor or from a platform such as YouTube warning about possible violations of community guidelines. The messages may contain a link redirecting you to a fake login page that steals your login data.
3. InfoStealer malware to bypass two-factor authentication (2FA) – in many cases involving hacked creator accounts, cybercriminals use malware to steal login credentials and browser cookie sessions that let them bypass 2FA features. Once in possession of your session cookie, the hacker can access your account without the second authentication step.
4. Account compromise - Once the hacker has access to your online account, they quickly change your password and recovery options to lock you out. Not only that, but they will attempt to exploit your fans and followers by promoting scams. This harms your reputation, and can inflict significant financial loss.
Let’s break down the attack chain and explore how each stage plays a role in compromising your account. By understanding how these attacks unfold in real time, you can recognize warning signs and take steps to protect your account.
The Calm Before the Storm
You’re in the zone, having just finished editing a new video for your followers, and can’t wait to share it on your YouTube account. You log in and open YouTube Studio.
- You upload the video and add a title, description and tags.
- You select the perfect thumbnail, one that will surely grab your viewers’ attention.
- With everything set, you begin scheduling the video’s release for the following day. Unbeknownst to you, this will be the last video you post—for a while.
Everything seems normal, but behind the scenes, a hacker is already scouting your account.
A Hacker Finds You a Perfect Target
While you’re busy preparing for your next project, a hacker has already singled you out from the crowd and begins gathering personal information and other details about you – data that will allow for a successful phishing attack.
The hacker navigates your YouTube channel:
- Clicks on the ‘About’ section.
- He finds your business email, listed for all to see. That’s all they need for the next step.
Now that the hacker has your email address, he can proceed to steal the keys that unlock access to your creator account.
The Phishing Email Arrives In Your Inbox
With your contact information in hand, the hacker delivers a convincing phishing email.
Here’s an example of what such an email could look like.
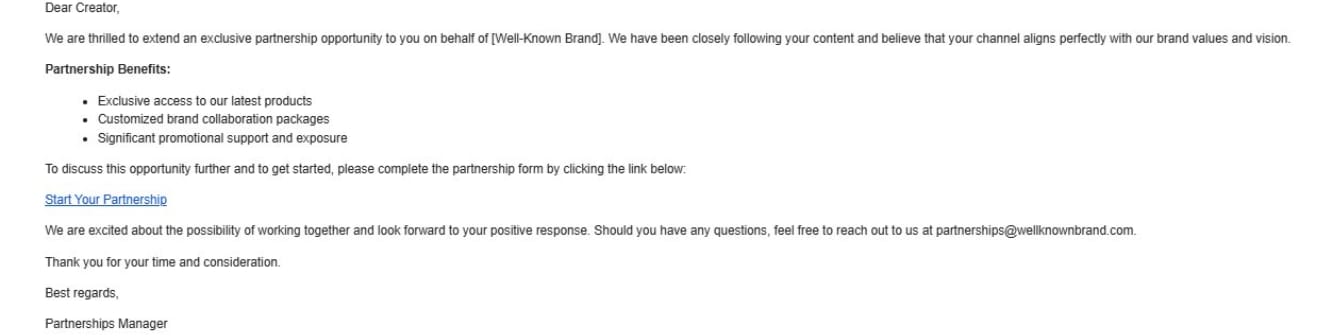
- They send you a phony partnership offer that has been tailored just for you and includes details about recent video uploads and audience engagement.
- The email also contains a PDF attachment named “partnership details.” But it’s loaded with InfoStealer malware, designed to steal your login credentials and session cookies and bypass 2FA.
- The hacker clicks “send” and waits for you to take the bait
It’s now a waiting game.
The Phishing Email Is a Success
You check your inbox and see a few new emails have just popped up, including the phishing email from the hacker.
- Next, you click on the partnership offer, intrigued. The email looks professional, you like the idea of collaborating with the business, so you decide to download the attachment.
- The moment you open the file, session tokens are sent directly to the hacker’s server, allowing the hacker to bypass 2FA.
You, unimpressed with the supposed contract or it seems too good to be true, delete the email, completely unaware that your device and account have already been compromised.
The Takeover – Hackers Take Control of the YouTube Account
The hacker now has your session tokens and cookies and a free pass to your account
- Using specialized software, the hacker injects the stolen session tokens into their own browser, gaining direct access to your YouTube account without triggering any security alarms and without needing your password or even 2FA.
- They immediately begin altering the account, changing the channel’s name to make it look like a crypto channel and making all videos private to avoid arousing suspicion from the creator’s fans.
- Finally, the hacker uploads a crypto scam livestream, a pre-recorded loop encouraging viewers to participate in a crypto-doubling scheme, usually with deepfake videos from well know public figures. The scam link is spread across the description and comments, disabling any interaction to prevent the fans from warning each other.
The hacker sits back, watching as unsuspecting viewers begin sending crypto to their accounts.
Read more in these dedicated articles:
· What Is Account Takeover (ATO) And How to Protect Against It
· YouTube Account Hacked? How to Recover & Secure Your Account
· How to Protect Your Social Media Accounts from Hackers
Realization Hits Hard and Panic Sets In
A few hours later, you receive a warning message from a close friend: “Your YouTube channel looks hacked!” Panic sets in.
- You try to log in to your account, only to find that the password no longer works.
- You quickly reset the password and delete the livestream scam, but the hacker just posts a new one.
- As you try to regain control, you’re locked out of your account once again, powerless to stop the ongoing scam.
With every second that passes, the hacker gains more from the livestream scam while harming your reputation and fans.
Your Loss Is The Hacker’s Payoff
The hacker watches the scam unfold, satisfied with the results.
1. The scam worked and dozens of your fans have fallen for the bait, believing that the livestream was genuine.
- Since you’re now locked out of your account, the hacker begins browsing for their next victim, ready to repeat the process.
Just another successful day in the business of taking over the accounts of unsuspecting content creators.
How to Break the Attack Chain and Protect Your Accounts and Reputation
Unfortunately, this scenario is far too common for content creators across all platforms. While the hacker may seem unstoppable, understanding how the chain works can help you recognize and break it before it gets to the point of no return.
- Be mindful of your publicly accessible information. Don’t list your personal email on your YouTube profile or other social media platforms unless you find this absolutely necessary. Instead, use dedicated business tools for communications.
- Be skeptical of unexpected emails. Always verify partnership offers and be cautious about clicking links or downloading attachments from unknown sources.
- Use Security Tools Tailored for Creators. Bitdefender Security for Creators, for example, offers real-time phishing and hacking protection, ensuring you’re protected even if you accidentally click on a malicious link.
- Enable recovery options. Keep your account recovery options up to date, and always use two-factor authentication, even though some attacks can bypass it.
Are you a YouTube content creator who wants to take a proactive approach to safeguarding your online accounts, content, followers, and reputation against hacks?
Check out Bitdefender Security for Creators and benefit from 24/7 account monitoring and protection, advanced hacking prevention, anti-phishing protection, account recovery assistance and much more.
You can read more about Bitdefender Security for Creators here.
Find Security for Creators plans that suit your creative spirit from a worldwide and award-winning security provider!
tags
Author
Alina is a history buff passionate about cybersecurity and anything sci-fi, advocating Bitdefender technologies and solutions. She spends most of her time between her two feline friends and traveling.
View all postsRight now Top posts
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
Your Device ‘Fingerprint’ Will Go to Advertisers Starting February 2025
December 24, 2024
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








