Cybercriminals Hijack Over 6,000 WordPress Sites to Distribute Malware
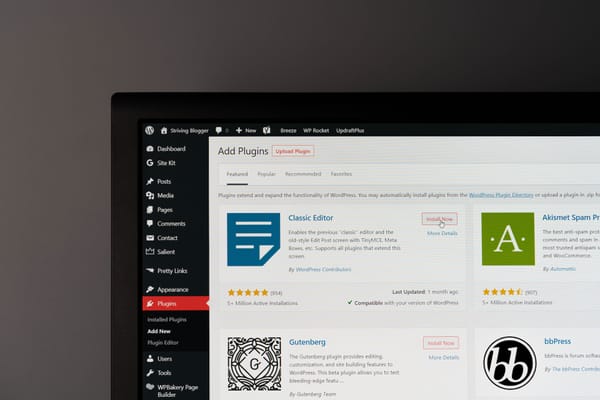
Cybersecurity researchers have spotted a massive campaign targeting WordPress websites for use in pushing malicious plugins.
Threat actors turned over 6,000 WordPress websites into malware peddlers. By leveraging rogue software updates and error messages, they distributed information-stealing malware to unsuspecting victims.
New Malicious Campaign Born From the Ashes of 2023’s ClearFake
Over the last few years, information-stealing malware has become a favorite tool of hackers worldwide, letting them gain access to sensitive credentials, breach networks and steal valuable data.
A malicious campaign reportedly launched in 2023, dubbed ClearFake, involved weaponizing compromised websites to display phony web browser update banners, luring users into downloading info-stealing malware.
A year later, the campaign has once again risen, wearing a different brand: ClickFix. Like its predecessor, ClickFix deceived users by prompting them to download “fixes” for popular software and services, including Google Chrome, Google Meet, and Facebook.
More than 6,000 WordPress Websites Compromised by ClickFix
Last week, web hosting company GoDaddy reported that threat actors orchestrating the ClickFix/ClearFake campaigns breached over 6,000 WordPress websites. Perpetrators used stolen credentials to access websites and install seemingly legitimate plugins, pushing fake update prompts to website visitors.
“These seemingly legitimate plugins are designed to appear harmless to website administrators but contain embedded malicious scripts that deliver fake browser update prompts to end-users,” reads GoDaddy’s security advisory. “This technique leverages social engineering strategies to trick users into executing malicious code, ultimately compromising their systems with various types of malware and information stealers.”
Numerous WordPress Plugins Weaponized to Deliver Malware
Between June and September 2024, the following malicious plugins were identified as part of the ClickFix/ClearFake campaign:
|
LiteSpeed
Cache Classic |
MonsterInsights
Classic |
Wordfence
Security Classic |
Custom CSS
Injector |
|
Custom Footer
Generator |
Custom Login
Styler |
Search Rank
Enhancer |
Dynamic
Sidebar Manager |
|
SEO Booster
Pro |
Easy Themes
Manager |
Google SEO
Enhancer |
Form Builder
Pro |
|
Rank Booster
Pro |
Quick Cache
Cleaner |
Admin Bar
Customizer |
Responsive
Menu Builder |
|
Advanced User
Manager |
SEO Optimizer
Pro |
Advanced
Widget Manager |
Simple Post
Enhancer |
|
Content
Blocker |
Social Media
Integrator |
Universal
Popup Plugin |
|
These rogue plugins inject malicious JavaScript into the compromised website’s HTML, which then loads scripts from a Binance Smart Chain (BSC) smart contract. The script ultimately displays the fake banners used in both ClearFake and ClickFix campaigns.
Mitigation Tips for WordPress Website Administrators
WordPress website administrators should closely monitor their websites for signs of unusual update prompts or fake alerts.
To mitigate this threat, administrators should review all installed plugins and remove any unauthorized or unfamiliar ones, reset all admin passwords, enable multi-factor authentication (MFA) and monitor server access logs for suspicious login attempts.
Avoid Falling Prey to Info-Stealing Malware
Users should consider installing specialized security software, such as Bitdefender Ultimate Security, to prevent their visits to compromised websites from falling prey to info-stealing malware. It works against all digital threats, including info-stealers, viruses, worms, Trojans, zero-day exploits, ransomware, spyware, and rootkits.
Bitdefender Ultimate Security comes with complete, real-time data protection, behavioral detection that takes instant action upon detecting suspicious activity in active apps, and a web attack prevention module that keeps you from landing on harmful websites.
tags
Author

Vlad's love for technology and writing created rich soil for his interest in cybersecurity to sprout into a full-on passion. Before becoming a Security Analyst, he covered tech and security topics.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks