Dyre malware targets millions of Salesforce users, stealing passwords and bypassing 2FA
We’re all used to the idea of malware which snoops upon our online banking, attempting to steal our login credentials to help hackers gain access to our bank accounts.
Many of us are also aware of spyware trojan horses that target users of other websites, including popular webmail services or social networks, in the hope of plundering private information or using the platforms as a springboard for other attacks and committing fraud.
But sadly there are other online services which are catching the attention of cybercriminals because of the treasure trove of information they contain.
Late last week, the immensely popular cloud-based CRM Salesforce issued a security warning to its millions of business users about the Dyre malware, which is attempting to steal login credentials from Salesforce’s many customers.
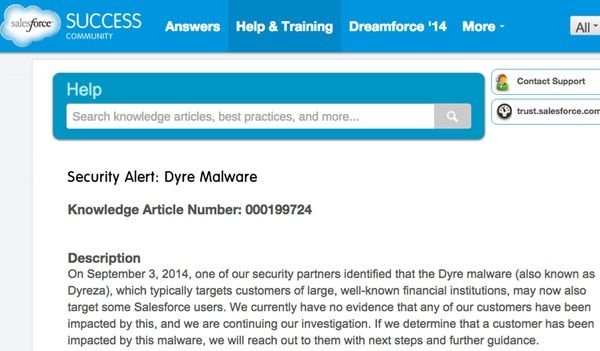
Part of the advisory read:
On September 3, 2014, one of our security partners identified that the Dyre malware (also known as Dyreza), which typically targets customers of large, well-known financial institutions, may now also target some Salesforce users. We currently have no evidence that any of our customers have been impacted by this, and we are continuing our investigation. If we determine that a customer has been impacted by this malware, we will reach out to them with next steps and further guidance.
This is not a vulnerability within Salesforce. It is malware that resides on infected computer systems and is designed to steal user log-in credentials and resides on infected customer systems.
The advisory went on to offer sensible advice about how users could strengthen their accounts’ security, by restricting the IP range of computers which were allowed to access accounts, and enabling two-factor authentication.
Interestingly, whoever created the Dyre malware was obviously keen to break into Salesforce accounts even if they were already protected by two-factor authentication.
As SC Magazine reports, if the Dyre malware has already infected a targeted computer it will redirect attempts to visit the genuine Salesforce website by taking users to a copycat site instead.
The bogus site grabs victims’s username and passwords, and then cunningly simultaneously logs into the genuine Salesforce website at the same time as the user tries to log into the false one, by intercepting the victim’s one-time password.
That’s a level of effort that malware authors would normally only go to for, say, a banking website.
Clearly these criminals are keen to get their hands on confidential business information, either for their own ends or to sell it on to others.
Fortunately, according to VirusTotal, most of the major anti-virus products are now able to detect the malware (which is also known as Dyreza) – including Bitdefender which protects against it generically as Trojan.GenericKD.1762927.
Salesforce says it will reach out to any customers who it believes has been affected by the malware.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks









