Feds Take Down Cybercrime Marketplace ‘PopeyeTools,’ Seizing Crypto Profits and Domains

US authorities this week obtained judicial authorization to dismantle a confirmed cybercrime platform whose administrators now face a decade behind bars.
According to a criminal complaint unsealed this week, Abdul Ghaffar, 25, of Pakistan; Abdul Sami, 35, of Pakistan; and Javed Mirza, 37, of Afghanistan, are charged with conspiracy to commit access device fraud, trafficking access devices, and solicitation of another person for the purposes of offering access devices, arising from their roles as administrators of the PopeyeTools website.
PopeyeTools – an illicit marketplace dedicated to selling stolen credit card information and other tools for cybercrime and fraud - made a name for itself by advertising reliable, quality “services” to eager fraudsters.
‘We believe in quality not quantity’
The PopeyeTools motto was ‘We Believe in Quality Not Quantity,’ and the website gained a reputation for selling stolen access to devices and “live” data – translating into “valid and thereby suited to committing financial fraud,” according to court documents cited by the US Justice Department.
“For instance, the ‘Live Fullz’ section offered unauthorized payment card data and PII for cards that were marketed as ‘live’ — i.e., could be used to conduct fraudulent transactions — at a price of approximately $30 per card,” the DOJ notes. “Other sections included ‘Fresh Bank Logs,’ which offered logs of stolen bank account information, ‘Fresh Leads’ or email spam lists, ‘Scam pages,’ and ‘Guides and Tutorials.’”
Refunds for ‘expired’ data
PopeyeTools sold access to services that could be used to check the validity of a bank account, credit card, or debit card numbers offered through the website, and prided itself on offering refunds or replacement cards if the ‘assets’ sold were no longer valid at the time of sale.
Some of the stolen information included bank account, credit card, and debit card numbers and associated data for conducting transactions.
Since its inception, PopeyeTools has offered compromised personal and financial data of at least 227,000 individuals and generated at least $1.7 million in revenue, the DOJ says.
As part of the actions undertaken this week, US authorities obtained judicial authorization to seize the domains www.PopeyeTools.com, www.PopeyeTools.co.uk, and www.PopeyeTools.to, “which long hosted and facilitated access to the PopeyeTools website,” and approximately $283,000 worth of cryptocurrencies from a wallet controlled by Abdul Sami, one of the three alleged administrators now facing 10 years in prison if caught.
The DOJ press release is unclear about where the trio are currently, whether they’ve already been arrested, or whether they’ll be extradited to face the charges in the US.
The DOJ is careful to point out that “All defendants are presumed innocent until proven guilty beyond a reasonable doubt in a court of law.”
What it’s not shy about is that PopeyeTools customers’ data is now in the feds’ hands, suggesting that this operation may yet take more people down.
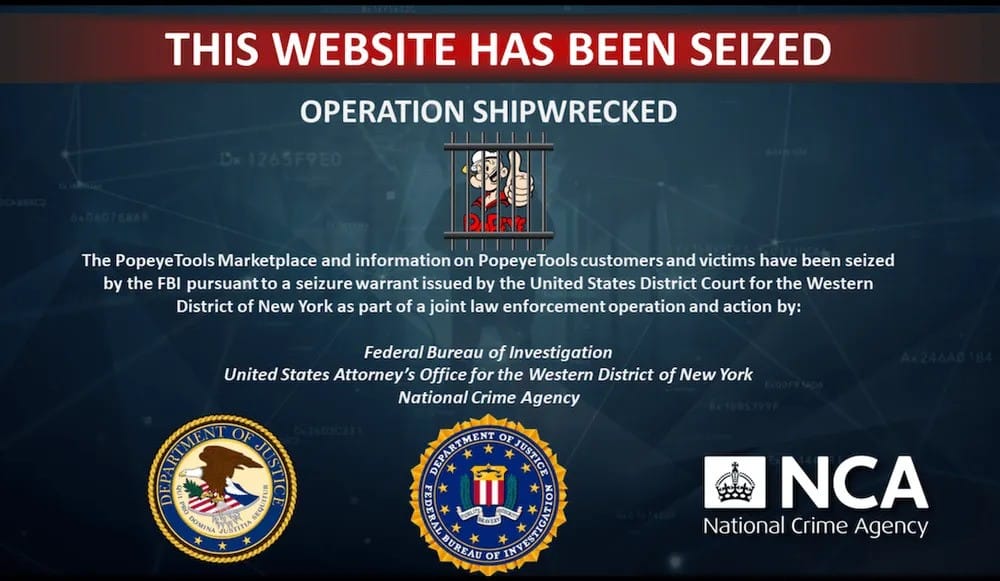
Splash page posted by US law enforcement after seizing PopeyeTools websites
Source: justice.gov
Feds double down on cybercrime
US authorities have cracked down on cybercrime operations in recent months, culminating with multiple arrests and seizures in November alone.
A Russian national believed responsible for the Phobos ransomware operation now faces a long sentence after being extradited from South Korea to the US.
Five men linked to the ‘Scattered Spider’ crime ring are also looking at decades in prison over costly phishing attacks on staff working at organizations known to have suffered data breaches.
Protect yourself
PopeyeTools and similar illicit marketplaces thrive on data dumps resulting from corporate breaches.
Bitdefender strongly advises netizens to consider using dedicated security on their personal devices, including services like Bitdefender Digital Identity Protection, to prevent fraudsters from exploiting leaked data like usernames, passwords, full names and addresses, phone numbers, email addresses, social security numbers, and banking data.
Fraudsters also use data stolen in breaches to weave intricate social engineering scams, like phishing lures delivered by email and SMS. According to the results in the Bitdefender 2024 Consumer Cybersecurity Assessment Report, text-based scams are the most common threat consumers face today. Yet four in five netizens make sensitive transactions on their phones without adequate cybersecurity practices – all while saying their main fear is that hackers will access their money.
If you're suspicious about a certain phone call, email or text, consider using Scamio, our clever scam-fighting chatbot designed specifically to combat socially engineered fraud attacks.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








