Hackers May Redirect Your Internet Traffic through D-Link Router Bugs
Several vulnerabilities in the DIR-600 and DIR-300 routers of network solutions company D-Link may allow hackers to redirect Internet traffic and compromise users` devices, according to German security researcher Michael Messner. The holes are supported by the lack of password hashing and root passwords being saved in plain text.
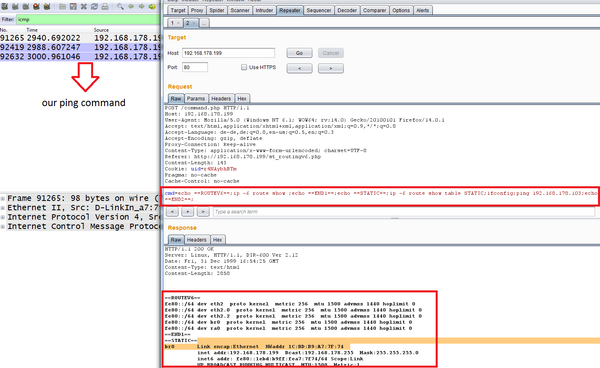
The Cross-Site Request Forgery (CSRF) vulnerability allows an attacker to easily change a password through malicious software, as there is no request for the password. The OS Command Injection vulnerability allows hackers to compromise users` devices.

Source: www.s3cur1ty.de
“The vulnerability is caused by missing access restrictions and missing input validation in the cmd parameter and can be exploited to inject and execute arbitrary shell commands,” Messner said in a blog post. “It is possible to start a telnetd to compromise the device.”
The H-Online also ran tests and discovered many of the devices can even be accessed from the Internet and managed to inject a harmless command into such a router. “A real attacker could randomly exploit systems, for example to divert a router’s entire internet traffic to a third-party server.”
According to Messner, D-Link said the issues are browser-related and they will not provide a fix. The security expert informed the company in December of last year.
tags
Author
Bianca Stanescu, the fiercest warrior princess in the Bitdefender news palace, is a down-to-earth journalist, who's always on to a cybertrendy story.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








