Hacking cars remotely with just their VIN

Your car's mobile app might have allowed hackers to remotely unlock your vehicle, turn on or off its engine, and even honk its horn.
Those are the findings of Sam Curry, a security researcher and bug bounty hunter, who explored vulnerabilities that could affect Hyundai, Genesis, Nissan, Infiniti, Honda, and Acura vehicles, amongst others.
Curry and his colleagues first turned their attention to the official mobile apps used by owners of Hyundai and Genesis vehicles, that allow authenticated users to start, stop, lock, and unlock their cars.
In a series of tweets, Curry demonstrated how he was able to exploit vulnerabilities in the Hyundai app and API to bypass authorisation checks and remotely unlock a vehicle just by knowing its owner's email address, and ultimately achieve complete takeover of their account.
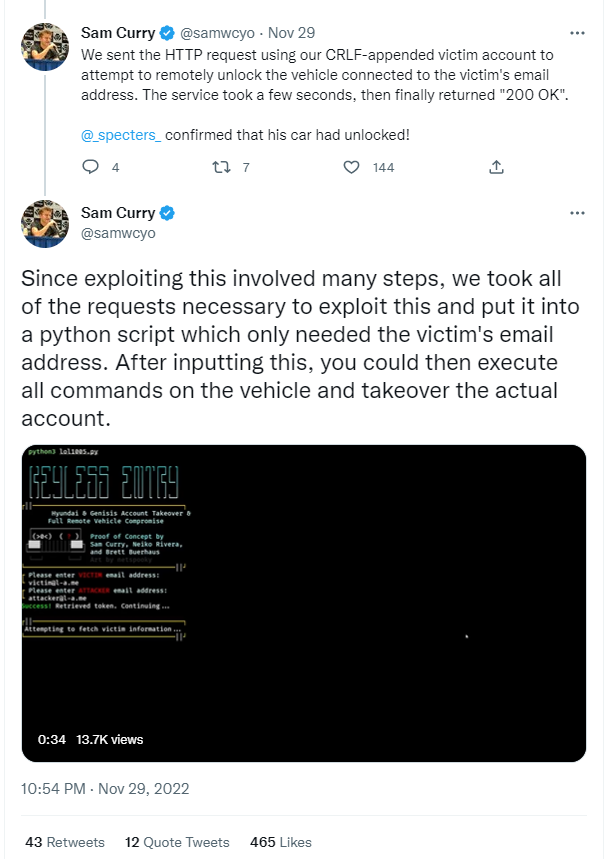
It later transpired the same risk was present for owners of Genesis vehicles.
Curry responsibly disclosed the security issue to Hyundai and Genesis.
A Hyundai spokesperson told The Record that "other than the Hyundai vehicles and accounts belonging to the researchers themselves, our investigation indicated that no customer vehicles or accounts were accessed by others as a result of the issues raised..."
Which is, I suppose, something of a relief. But it's still a great worry that the security risk was present in the first place.
Perhaps emboldened by their discovery related to Hyundai and Genesis vehicles, Curry went on to explore vulnerabilities affecting other manufacturers - specifically those who made use of the SiriusXM Connected Vehicle Services telematics platform.
As Curry has now described unauthorised parties were able to send commands to a Nissan, Infiniti, Honda, and Acura vehicle, just by knowing its Vehicle Identification Number (VIN).
And even if a specific car was no longer actively subscribed to SiriusXM's service, Curry found he was able to sign it up to the service by simply knowing the VIN, which is typically visible through the car's windscreen.
Using this technique, cars could be remotely stopped or started, locked or unlocked, flash their headlights, or honk their horn. Even an owner's personal details (name, phone number, address, and car information) could be extracted without authorisation.
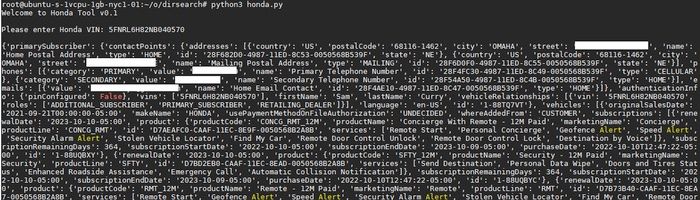
And although the API calls for telematic services worked even if the user no longer had an active SiriusXM subscription, Curry noted that he could enroll or enroll vehicle owners from the service at will.
Fortunately, being a responsible security researcher, Curry informed the relevant parties of the issue privately - allowing them to patch the vulnerability before details were made public.
Apps are supposed to make motorists' lives more convenient, not
decrease their security. We can only hope that manufacturers will put
greater effort in the future into ensuring that smartphone-connected
cars will be better protected.
Update
Hyundai have offered the following statement:
"Hyundai worked diligently with third-party consultants to investigate the purported vulnerability as soon as the researchers brought it to our attention. Importantly, other than the Hyundai vehicles and accounts belonging to the researchers themselves, our investigation indicated that no customer vehicles or accounts – for either Hyundai or Genesis – were accessed by others as a result of the issues raised by the researchers."
"We also note that in order to employ the purported vulnerability, the e-mail address associated with the specific Hyundai/Genesis account and vehicle as well as the specific web-script employed by the researchers were required to be known. Nevertheless, Hyundai and Genesis implemented countermeasures within days of notification to further enhance the safety and security of our systems. Separately, Hyundai and Genesis were not affected by a Sirius XM authorization flaw that was recently disclosed."
"We value our collaboration with security researchers and appreciate this team’s assistance."
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
Scammers Sell Access to Steam Accounts with All the Latest Games – It's a Trap!
May 16, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








