LinkedIn Password Change Notification Randomly Sent to Previous Employers
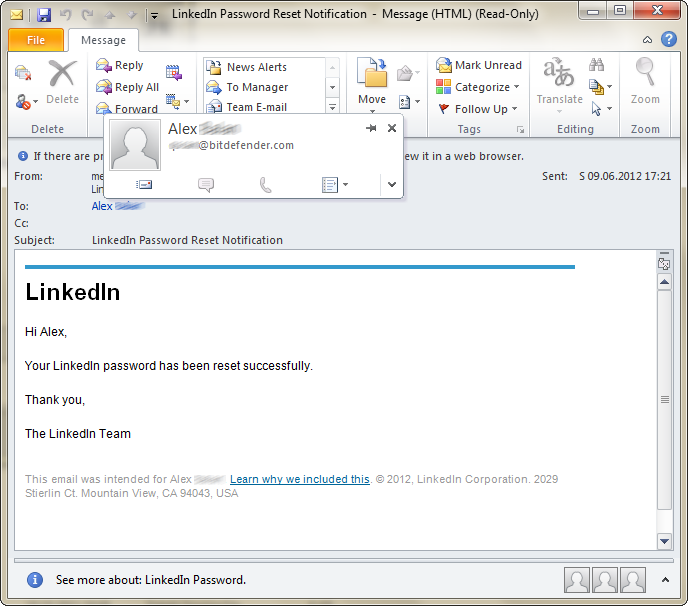
After the leak of roughly 6.5 million hashed passwords last week and the failed “mandatory password update for the affected account”Â, LinkedIn’s password reset confirmation e-mail has backfired by disclosing the reset to victim’ previous employers.
The password-reset confirmation appears to be randomly sent to a number of e-mail addresses the user is likely connected with. Based on our observations, these notifications are sent to e-mail accounts with current or previous employers – even if these e-mail addresses have never been associated with the LinkedIn account.
Example: Password reset notification for a user, sent to qscan@bitdefender. The Quick Scan account has never been associated with LinkedIn in any way.
The service notifies the user at e-mail addresses he or she doesn’t control allegedly to minimize phishing attacks following the leak of the hashed passwords. Although the LinkedIn message doesn’t mention the username, password or other identification for the user’s account, this alleged security feature counts as unnecessary disclosure of activity that may actually work against the user by informing third parties of his or her whereabouts.
We have notified LinkedIn about the issue.
tags
Author
Right now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








