Malware Shifting from SMS Trojans to Ransomware and Banking
While previous Android malware reports showed an increase in SMS Trojans that hijacked user phones to send text messages to premium-rated numbers, a new report on 2013’s first six months highlights new, more sophisticated threats.
With SMS Trojans as the ranking Trojan family – Android.Trojan.FakeInst having 72.51 percent of all global malware reports – Android ransomware is under the spotlight as a new and growing threat.
Info Stealers and e-banking Malware
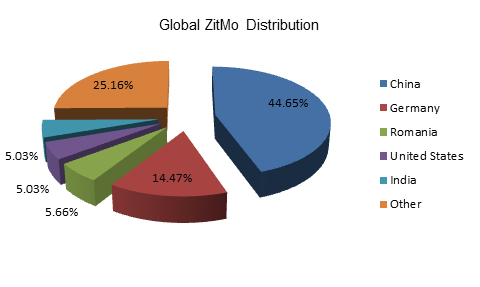
While most ZitMo reports come from China (44.65 percent), Germany appears to have also been targeted. With 14.47 percent of all reports originating from Germany, it’s safe to assume that attackers have been focusing on users who shop online a lot.
Android banking Trojans pretend to be security apps or sometimes display “ertificate update” messages to trick users into downloading and installing them. While Zeus is a notorious name in the world of banking malware for PCs, ZitMo is its Android counterpart. It’s equally devious.
ZitMo receives commands from a Command and Control (C&C) server and can forward all incoming SMS messages to it. This is of particular interest to attackers as they can receive the banking mTAN (mobile Transaction Authentication Number) as soon as users initiate the transaction. Having a Zeus deployed on a PC and ZitMo intercepting SMS mTANs, attackers gain complete control over e-banking transactions.
While hijacking online banking transactions may prove highly profitable, stealing private and personal user information from devices is also good business for crooks. Info stealers are not only limited to ZitMo, but also extend to other Android malware families and sometimes even adware.
Ransomware
A new breed of Android malware has been spotted in Asia, and behaves in pretty much the same was as PC ransomware. Disguised as anti-malware solutions, Android.FakeAV.C tricks users into downloading them and demanding payment to restore the device’s functionality.
The increased level of sophistication and its similarity with PC ransomware might suggest that Android malware coders are branching out. Emulating the behavior of PC malware on Android is no novelty, as we seen in the past how adware gained traction and evolved on the mobile OS.
The FakeAV malware family also includes the Android.FakeAV.B detection, which is a fake anti-malware solution that poses as legit. It even shares the same scanning engine as a legitimate Android security solution. Also posted in Google Play for a short while, its purpose was to steal sensitive information and send it to a remote machine.
The Android.FakeAV malware family – that’s made up of more than the two previously mentioned detecions – has been largely reported in India, with 32.70 percent, followed by Indonesia with 15.90 percent, and Malaysia with 6.96 percent. The malware family appears to target countries where users download apps from illegitimate marketplaces by luring them with the promise of an effective anti-malware solution.
European countries do not seem as targeted by this form of Android ransomware, as users are more likely to avoid downloading apps from non-official marketplaces.
Adware
Aggressive adware bundled with free apps have been known to collect personal and private data to better target users with custom ads. Marketers have also been known to value such information, as promotional campaigns would be considerably more accurate and more profitable.
Although the Android.Adware.Mulad family is made up of reports from several obscure adware SDKs, the Android.Adware.Plankton adware family makes up 53.34 percent of all global adware reports.
Conclusion
With BYOD policies still lacking in terms of personal devices that access sensitive company data, attackers could be skillfully exploiting both Android vulnerabilities and users’ lack of training to gain a foothold in a targeted company.
Android mobile security is no longer optional, but mandatory, when confronted with these new attack vectors and threats.
tags
Author
Liviu Arsene is the proud owner of the secret to the fountain of never-ending energy. That's what's been helping him work his everything off as a passionate tech news editor for the past few years.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks











