Malware Writers Target SMB Employees with Fake Policy Violation
A new cyber-crime attack tricks SMB employees into downloading Zbot and other Trojans by accusing them of violating company policy, according to antivirus software provider Bitdefender. The spam wave started to accelerate a week ago with dozens of unique .ARJ compressed files infecting computers, as the Bitdefender AntiSpam Laboratory has determined.
The malware attack is based on Zbot or Zeus, which includes a password-stealing component, enabling it to snatch banking, financial usernames and passwords, and email or FTP credentials. “ARJ-compressed files used to distribute malicious attachments are just starting to become popular and many zip file software programs can easily open them,” Bitdefender AntiSpam Researcher Adrian Miron said. “Because the compression system is rarely used, spammers very well may think of it as a new method to avoid being detected by traditional security software or email filters.”Â
Bitdefender has also identified the main countries of origin of the spam attack: Spain, Korea, Germany, the US, the UK, France, Italy, Russia, Portugal and Saudi Arabia. To dodge law enforcement, scammers may hide their real coordinates, so these are rather the countries where they have placed bots to help them spread the infection.
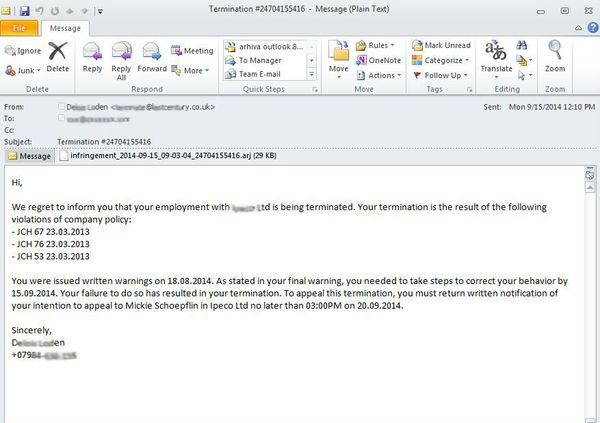
Here’s a typical malicious email:
Greetings,
We regret to inform you that your employment with [company name removed] is being terminated. Your termination is the result of the following violations of company policy:
– 1T7 72 14.09.2012
– 1T7 52 14.09.2012
– 1T7 56 14.09.2012
You were issued written warnings on 27.08.2014. As stated in your final warning, you needed to take steps to correct your behavior by 15.09.2014. Your failure to do so has resulted in your termination. To appeal this termination, you must return written notification of your intention to appeal to [names removed] no later than 07:00PM on 21.09.2014.
Sincerely,
[name removed]
+07535 XXXXXXX”
Here’s the attachment name variation: infringement, interruption, breach, infraction, violation, term, disturbance etc.
 To avoid suspicions, the malware opens a clean .rtf document which includes discipline programs and measures that companies take in case of policy violation.
To avoid suspicions, the malware opens a clean .rtf document which includes discipline programs and measures that companies take in case of policy violation.
Without the victims’ knowledge, the malware tries to connect the computer to several Zbot-infected web sites registered on German, Brazilian or French domains (.de, com.br, .fr). Victims are then connected to the command and control center, where hackers can give computers further instructions such as to download additional malware.
The malicious attack also circulates with “overdue invoice” and “fax” spam waves, using similar social engineering techniques to persuade victims to open attachments.
Millions of malware attacks target companies every month and hackers manage to steal confidential data by taking advantage of system vulnerabilities. Given the rise of the BYOD trend, the attack could be even more successful this time. In the US and in several other countries, many employee-owned mobile devices have full access to the company’s VPN” a vast amount of private corporate data that hackers can easily mine.
A worrying Bitdefender study showed that almost one in five SMBs in countries including the US face major security risks as they continue to use Windows XP, even though Microsoft ended support and security updates for the operating system.
To help users stay clear of dangerous email attachments, Bitdefender offers some security advice:
- Don’t trust email attachments, even if they are not executable files. To better hide malicious code, scammers often make them look like PDFs, Word documents, JPG images or other types of files.
- Avoid clicking on attachments even when they seem to come from reputable institutions (flight and travel companies, banks and financial institutions etc.). Malware infections are a click away even after opening a simple HTML file.
- Don’t fall for e-mail subject lines meant to trick you or pique your curiosity. There is no reason to get an unpaid bill via e-mail or airplane tickets by accident, and you probably haven’t won the Microsoft lottery.
- Keep your security solution updated on all Internet-connected devices and be careful with the private data you store. Trojans installed through malicious attachments usually have spyware and password-stealing capabilities.
- In most cases, scammers’ repertoires are redundant and industry blogs such as HotForSecurity tackle e-threat topics on a regular basis, so a simple search on the Internet will tell you if a message is fake.
This article is based on the technical information provided courtesy of Bitdefender Malware Researchers Cosmin TARSICHI and Octavian MINEA, and Bitdefender AntiSpam Researcher Adrian MIRON.
All product and company names mentioned herein are for identification purposes only and are the property of, and may be trademarks of, their respective owners.
tags
Author
Bianca Stanescu, the fiercest warrior princess in the Bitdefender news palace, is a down-to-earth journalist, who's always on to a cybertrendy story.
View all postsRight now Top posts
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
Your Device ‘Fingerprint’ Will Go to Advertisers Starting February 2025
December 24, 2024
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








