No, Attackers Don't Have Compromising Videos of You. Don't Give Them Blackmail Money.

Threatening someone with the release of images and videos captured from an infected device has been a common criminal tactic for years. You would think there's no chance someone actually believes it. The fact that we're still dealing with this ridiculous claim from criminals means that it's working and that there are enough victims out there to warrant more caution.
A long time ago, criminals and hackers had a much easier time compromising devices, especially computers. Taking control of a webcam was much easier and it usually involved tricking people into installing the malware themselves.
To be fair, this type of malware is still present, but security solutions are a lot more common. Getting people to install malware voluntarily now requires a lot of social engineering, and criminals are likely to use the time and effort for more lucrative attacks. For example, tricking people into installing a banking trojan that gives hackers direct access to banking apps has the potential to do a lot more harm.
Hacking into devices is really hard
Over the years, one thing that has changed is the ease of compromising a device without having the user knowingly or unknowingly take part. Today, it takes complex social engineering techniques to persuade a user to install a third-party app on Android or to trick an Apple user into offering his credentials in a phishing attack.
This should be the first line of defense against attacks in which criminals claim to have access to your device. This kind of scam has a name: sextortion.
The underlying message is simple, and criminals don't mince words. They had malware installed on your device, phone or computer (they don't specify), and they recorded you in a compromising posture. They threaten to release the recordings only if they don't receive a payment, usually in Bitcoin.
Of course, they don't actually have any recording of you, and your device hasn't been compromised. Criminals know that these types of emails might end up in the inbox of someone who doesn't know much about cybersecurity or who doesn't know that what criminals are saying in the email is highly unlikely.
Trying to be convincing
Like all attacks, sextortion emails have evolved significantly over the years. Before the advent of tools such as ChatGPT, text were written in mangled English and it was easy to tell that it was likely a scam.
Unfortunately, texts are now written very well, likely generated with the help of such tools, making them grammatically correct. Using grammar to spot a scam is no longer a valid strategy.
Another tactic that will offer attackers more credibility is inserting a password that the potential victims had used in the past. We know from our market studies that around 30 to 40 percent of people reuse the same password on multiple online accounts. Also, a large swath of those users will also keep the same password even after being notified of a data breach.
Seeing your password mentioned in an email from someone threatening to release your private videos might be enough for users to believe that attackers actually do have access to your device.
The truth is much simpler. Criminals use the passwords from data breaches to give their email credence, knowing many users won’t catch on.
Protecting your private life against sextortion scams
Here’s a simple example of an email from a criminal that claims to have videos of you.
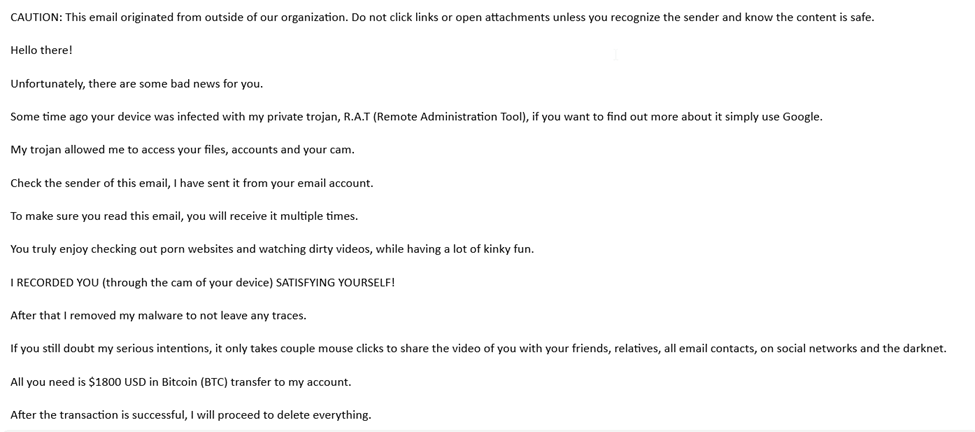
He asks for $1,800 USD and offers a Bitcoin wallet address to send the money, accompanied by a promise to delete the files once payment has been completed. He’s nothing if not honest.
He also offers a three-day ultimatum and says that he already knows if you’ve read his email. The “countdown” has officially begun. This is all fake, of course, but it makes it sound very official.
The first line of defense is also the most important one. Users knowing about the existence of this scam give them a great deal of power. They are easy to recognize, and deleting an email is a very quick action.
Some companies might have dedicated filters that can protect users, but what of users that don’t have the benefit of a company email armed to the teeth? Fortunately, Bitdefender Ultimate Security offers a brand new feature named E-mail Protection that integrates perfectly with Gmail and Outlook, showing people if their email is safe or not.
Scamio, the best way to determine if it’s a scam or not
There’s also a third way to determine if a message you’ve received is a scam, and it involves using Scamio, a free chatbot provided by Bitdefender that can be queried with text and images. Feeding it this email would immediately result in Scam verdict.
If you feel like someone may be trying to scam you, instead of playing detective, start a conversation with Scamio. You can copy-paste the message, upload an image, send a link, or describe your situation. Scamio analyzes it and lets you know if it’s safe or not.
· Free, easy-to-use AI chatbot
· No download, no install needed
· Available on web, WhatsApp, and Messenger
· Extensive threat analysis and scam detection
· Practical tips and tricks to avoid scams.
tags
Author
Silviu is a seasoned writer who followed the technology world for almost two decades, covering topics ranging from software to hardware and everything in between.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks







