Pegasus Spyware Users Tried (and Failed) to Infect Serbian Journalists’ Phones, Amnesty International Says

NSO Group’s Pegasus spyware is again in the spotlight after two high-profile journalists were allegedly targeted – but not infected – with the infamous surveillance software.
“Two journalists from Balkan Investigative Reporting Network (BIRN), an award-winning Serbian network of investigative journalists, were targeted with NSO Group’s Pegasus spyware last month,” according to an investigation by human-rights group Amnesty International.
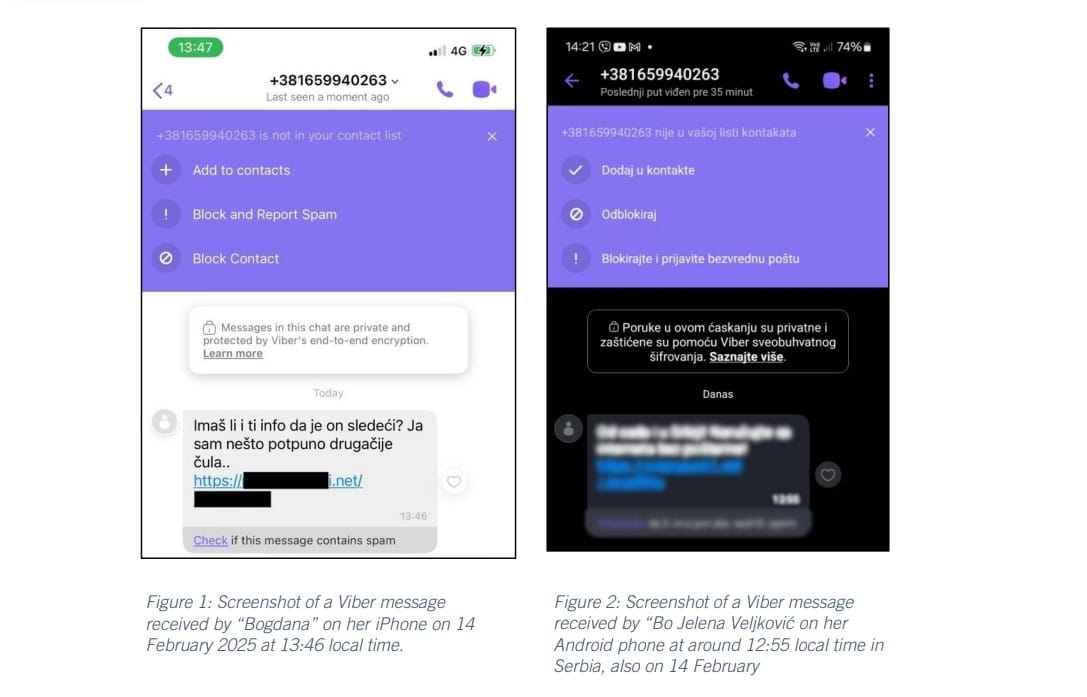
The two female journalists, identified in the report as Bogdana (not her real name) and Jelena Veljkovic, received “suspicious messages” on the Viber messaging app from an unknown Serbian number linked to Telekom Srbija, the nation’s telecoms operator.
Confirmed suspicions
Bogdana said that, on Feb. 14 at 13:46 local time, her iPhone lit up with a message linking to a news article and a tantalizing text reading: “Do you have info that he is next? I heard something completely different.”
Bogdana never interacted with the content.
An hour earlier on the same day, Jelena received a nearly identical message on her Android phone, also on Viber, from the same Serbian number. She deleted it without interacting.
Screenshots of the attack unfolding via the Viber messaging app
Source: amnesty.org
“Suspecting that their smartphones were being targeted by a spyware attack, they approached Amnesty International’s Security Lab, whose forensic analysis confirmed their suspicions,” says the human rights group.
BIRN and its staff face frequent threats, harassment, and lawsuits for their investigative journalism. According to Amnesty, this is the third time in two years that its researchers have found Pegasus used against civil society in Serbia.
The technical analysis indicates that the spyware used in the attacks was Pegasus, from the Israel-based NSO Group.
Researchers confident it was a Pegasus attack
NSO and its fellow spyware developers in Israel and elsewhere in the world make regular headlines over abuses involving their surveillance software.
NSO maintains that its sole mission is to create “technology that helps government agencies prevent and investigate terrorism and crime to save thousands of lives around the globe.”
It also stresses every time it’s pressed by the media that it refuses to sell its solutions to unethical clients.
Based on the nature of the attack vector – a tainted link that required a tap from the victim – Amnesty researchers concluded that this was a one-click infection attempt.
According to Donncha Ó Cearbhaill, the head of Amnesty International’s Security Lab, the text messages contained hyperlinks to a Serbian language domain name which the lab “determined with high confidence to be associated with NSO Group’s Pegasus spyware.”
Responding to the allegations, NSO Group said: “We cannot comment on specific existing or past customers. Additionally, as a matter of policy, we are unable to disclose any information regarding our technical specifications, functionality or operational features of our products.”
The human rights advocacy says its data indicates that Serbian authorities are abusing many digital surveillance technologies “to target journalists, activists, and other members of civil society amid widespread student protests that have gripped the country since November 2024.”
How to protect yourself against spyware
As we regularly remind readers when the spotlight hits spyware, make sure to keep your devices and software updated with the latest security patches from your vendor as a first important step against potential infection.
Sophisticated attacks like these typically target high-profile, high-risk individuals. Even if you don’t consider yourself a target, it’s always a good idea to secure your devices against potential attacks.
Read: How Spyware Infects Smartphones and How to Defend Against It
On iOS, remember to keep the trusty Lockdown Mode handy if you consider yourself vulnerable to an attack.
WhatsApp has recently addressed a vulnerability used in mercenary spyware attacks.
Apple released updates across its product lineup this month to address a weakness likely exploited by hackers in similar attacks.
And Google, as recently as this week, rolled out an updated version of its Chrome browser to the masses after mending a grave security flaw said to be exploited in espionage.
Read: WhatsApp Patches Zero-Click Spyware Attack Vector on Android
Read: Google Releases Urgent Chrome Update to Thwart Espionage Exploit
Read: 10 Cyberthreats iPhone Users Can’t Afford to Ignore in 2025
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








