QR Code Bug In iOS 11 Tricks Camera App to Open Unpredictable Websites
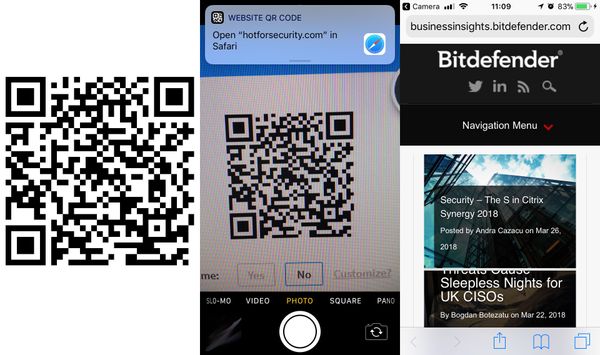
A recent vulnerability in the way Apple”s iOS camera app handles automatic QR code scanning, could potentially be abused to trick users into opening potentially nasty websites, according to security researchers.
The bug is triggered whenever users point their cameras at QR codes that redirect to various websites. Because the URL is not properly sanitized by the iOS camera app, threat actors can redirect users to a different domain than the one displayed in the notification bar, according to security researcher Roman Mueller.
Both the camera app and the Safari browser opening the URL embedded in the QR code appear to have different ways in parsing URLs, which in turn leads to the current issue.
“The URL parser of the camera app has a problem here detecting the hostname in this URL in the same way as Safari does,” wrote Mueller. “This leads to a different hostname being displayed in the notification compared to what actually is opened in Safari.”
The example used by Mueller involves creating a QR code from the following URL: https://xxx\@facebook.com:[email protected]/. Instead of redirecting users to Facebook, as the notification on iOS displays, it will actually redirects them to infosec.rm-it.de.
While it”s unclear where exactly the bug occurs, as Apple”s software is notoriously gated, the vulnerability has been reported to Apple”s security team on 2017-12-23.
Testing the vulnerability, as shown in the screenshots above, revealed that it has yet to be patched. Creating our own QR code, it prompts users that hotforsecurity.com will be opened, only for Safari to redirect to businessinsights.bitdefender.com.
Until an update addressing the bug becomes available, caution is advised when scanning QR codes.
tags
Author
Liviu Arsene is the proud owner of the secret to the fountain of never-ending energy. That's what's been helping him work his everything off as a passionate tech news editor for the past few years.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








