Rejuvenated FluBot Campaign Moves to Finland; iPhone Users Also Targeted

Finland’s national cybersecurity center is warning citizens to steer clear of text messages advertising an incoming transmission adorned with a link. The reason? FluBot operators are at it again.
“The FluBot malware campaign for Android devices has been activated again in Finland,” reads a machine-translated warning from the country’s cybersecurity authority.
Fins have had similar run-ins with FluBot in the past, as have other regions around the world.
“The malware steals data from the user's device and is distributed via SMS and MMS,” the warning says.
Bitdefender can independently confirm a considerable spike in FluBot activity in Finland in the last few days.
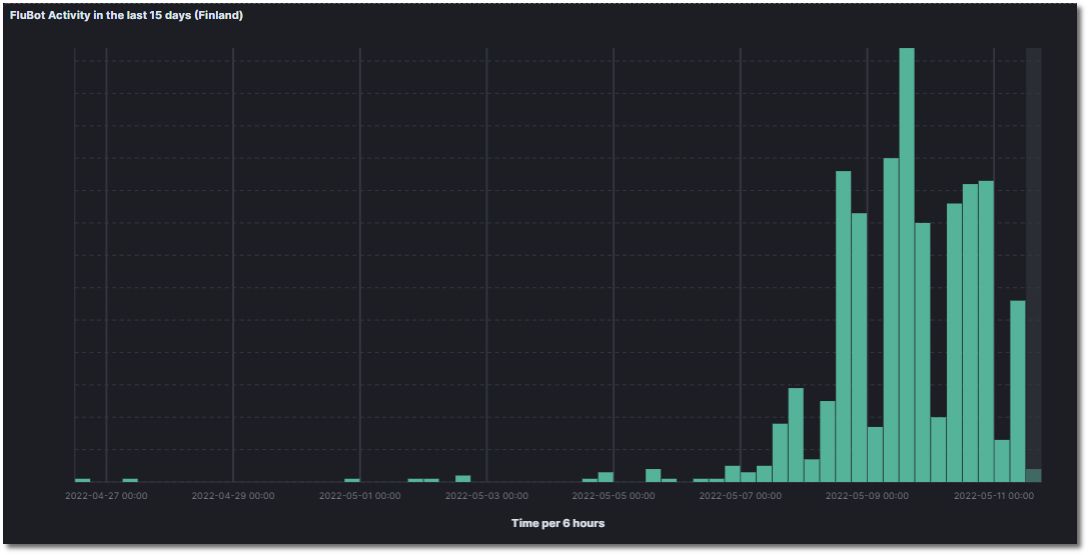
FluBot activity in the last 15 days (Finland)
Credit: Bitdefender
The campaign is similar to its predecessors, with users receiving an SMS or MMS featuring a fake voice message, a missed call, “or a notification of an incoming transmission,” according to the advisory.
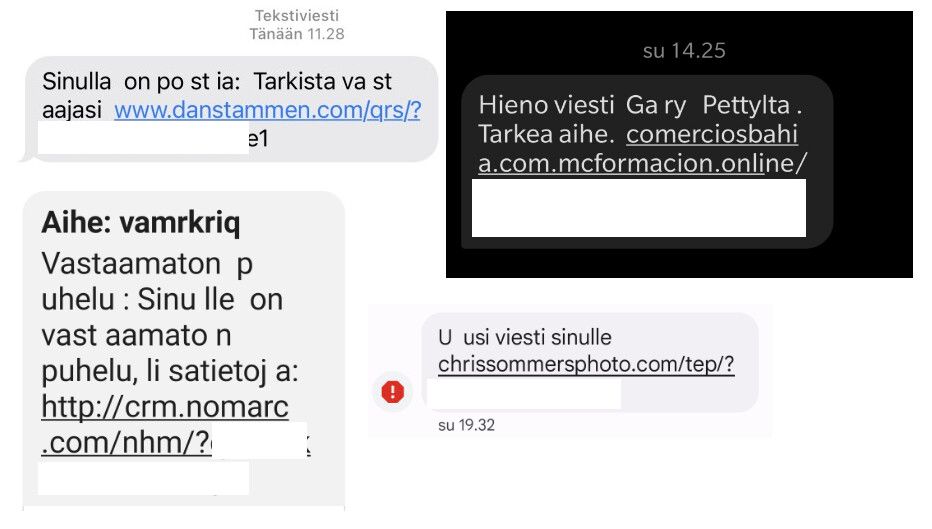
Credit: kyberturvallisuuskeskus.fi
Thousands of malicious messages are actively circulating asking users to install an app to access the purported content. The app, however, is FluBot malware, the center warns.
‘Like the flu’
Originally designed as a banking Trojan, FluBot lets its operators yank out credit card information and login data (credentials) and raid the victims’ various accounts - mainly their bank accounts. It also copies the victim’s contact list and automatically sends infected links to them, spreading like the flu. Hence the name, FluBot.
“The malware requests the user's explicit consent for installation. An attempt is made to persuade the user to disable the device security settings to install the malware,” according to Finland’s cyber center.
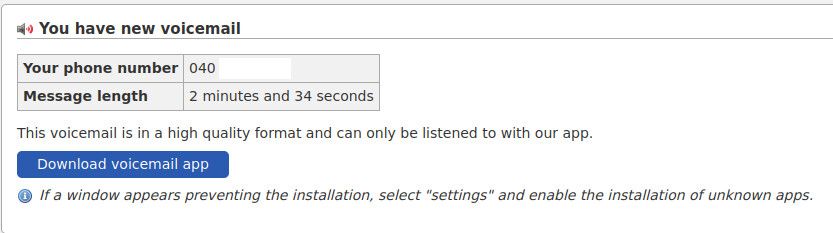
Credit: kyberturvallisuuskeskus.fi
Because iOS prevents third-party app installs outside Apple’s walled garden, iPhone owners on the receiving end of this campaign are redirected to subscription scams and other types of social engineering. In other words, Apple customers are not exempt from this malicious campaign by any measure.
Identical to campaign targeting Romania around Easter
The campaign is identical to one that swept through Romania around Easter, when thousands of Android users registered a wave of smishing. Like with Finnish iOS users, iPhone owners in Romania were redirected to phishing sites and other scams, Bitdefender independently confirmed at the time.
The advisory notes that simply opening the link doesn’t install the malware, but if victims eventually allow it to be installed they should reset their devices to factory settings ASAP, then restore from a backup saved before the malware infection.
While the mitigations described in the advisory are certainly accurate, the best way to keep FluBot off your Android phone is to use a security solution capable of blocking mobile-specific malware. Attackers’ tactics vary over time and will undoubtedly improve in future campaigns, which makes it imperative to maintain an advanced detection mechanism on your device.
Bitdefender Mobile Security alerts users that a scam is being attempted on their device even before they can access the malicious content. Any subsequent attempt at installing the disguised FluBot malware is blocked.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








