Researchers Discover New Way for Telcos and ISPs to Protect Consumer IoT Devices from DDOS Attacks

IoT devices in the home network are becoming more and more vulnerable to digital threats, and most smart-home device owners are unaware of the impending risks.
According to a study from Ben-Gurion University of the Negev (BGU) and National University of Singapore (NUS) researchers have discovered a new way that enables telecommunications and Internet service providers to monitor vulnerable IoT devices, hampering DDoS attacks via a botnet of compromised devices.
Vulnerable smart devices in our homes are not limited to compromising local networks, but could impact the infrastructure and telcos and ISPs as well.
“Most home users don’t have the awareness, knowledge, or means to prevent or handle ongoing attacks,” says YairMeidan, a Ph.D. candidate in BGU’s Department of Software and Information Systems Engineering (SISE). “As a result, the burden falls on the telcos to handle. Our method addresses a real-world problem that has already caused challenging attacks in Germany and Singapore, and poses a risk to telco infrastructure and their customers worldwide.”
As such, the scientist duo propose “a method to detect connected, vulnerable IoT models before they are compromised by monitoring the data traffic from each smart home device.”
“This enables telcos to verify whether specific IoT models, known to be vulnerable to exploitation by malware for cyberattacks are connected to the home network,” the researchers said. “It helps telcos identify potential threats to their networks and take preventive actions quickly.”
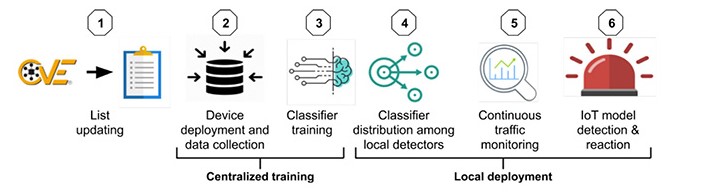
Overview of key steps in proposed method by researchers
“We consider an additional measure for telcos to use in their defense against IoT-based attacks launched from their customers premises and propose a method for detecting connected vulnerable IoT models before they are compromised,” the researchers said.
“This method, which takes a preemptive approach, can assist telcos in identifying potential threats to their networks and enable them to take preventive actions in a timely manner,” they added. “Our method monitors the traffic of each smart home separately to verify whether specific IoT models, known to be vulnerable to exploitation by malware for the purpose of executing cyber-attacks, are connected to the home network.”
This proactive measure lets a telco or ISP provider detect vulnerable IoT devices connected behind a NAT, and use this information to take action in case of a DDoS attack, sparing both the company and its customers from harm. By applying this method, telcos can prevent traffic surges from hitting its infrastructure, and ensure availability of their services.
The researchers also noted that this research is a key step toward mitigating risks posed to telecommunication service infrastructures by IoT models connected behind a domestic NAT. In the long run, they plan to further expand their method to include a wide range of IoT devices and manufacturers.
“Although our method is designed to detect vulnerable IoT devices before they are exploited, we plan to evaluate the resilience of our method to adversarial attacks in future research,” Meidan says. “Similarly, a spoofing attack, in which an infected device performs many dummy requests to IP addresses and ports that are different from the default ones, could result in missed detection.
tags
Author
Alina is a history buff passionate about cybersecurity and anything sci-fi, advocating Bitdefender technologies and solutions. She spends most of her time between her two feline friends and traveling.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








