Beware of Scam Emails Seeking Donations for UNICEF or Other Humanitarian Groups

A new wave of spam emails is spreading worldwide, using the UNICEF name and a seemingly official email in an effort to persuade people to donate money for the victims of the Gaza conflict.
Spam emails and scams flooding email accounts always follow any humanitarian crisis. In fact, the same goes for events that have global reverberations. Criminals always try to take advantage of notable events to persuade people to donate.
For the most part, scams rely on one of two scenarios: On the one hand, criminals present their targets with some type of emergency to compel them to open a link or an attachment or install an application. On the other hand, victims might be enticed with a money prize or an expensive smartphone.
The goal is the same: to get users to enter their credentials and financial information or, even worse, to install malware on their devices.
However, a third option is to appeal to humanity by pretending to represent a humanitarian organization. We’ve seen this over and over. Less than 24 hours after the two massive earthquakes claimed the lives of thousands of people in Turkey and Syria in 2023, for example, the first scam campaigns were already up and running.
UNICEF is just one organization affected
The UNICEF name carries a lot of weight, especially when it comes to humanitarian aid, which is why criminals use it in their campaigns.
The email looks convincing and tries to appeal to the users’ empathy. Also, some of the tools people have to spot these scams will not work in this case.
For example, the email used in the attack seems to be an official one.
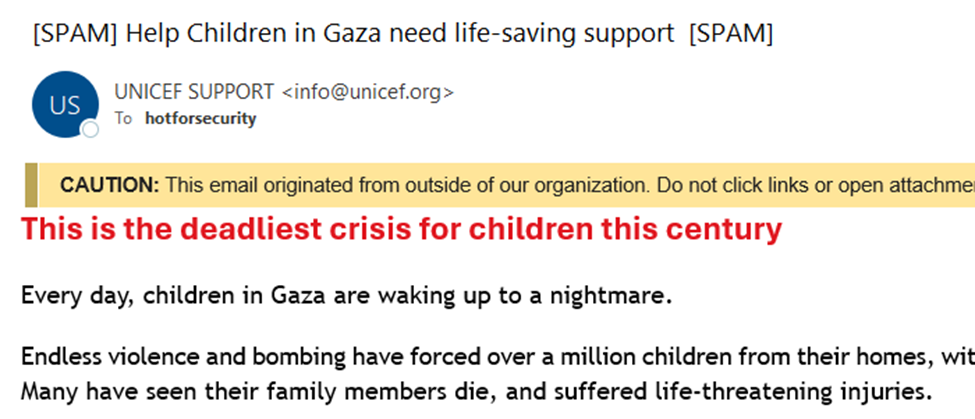
Even if the user looks closer, it still looks like an official email address.
The other handy tool is a check for grammatical errors, but that can’t always be trusted. With the advent of AI-powered translation tools, getting the text right is no longer difficult.
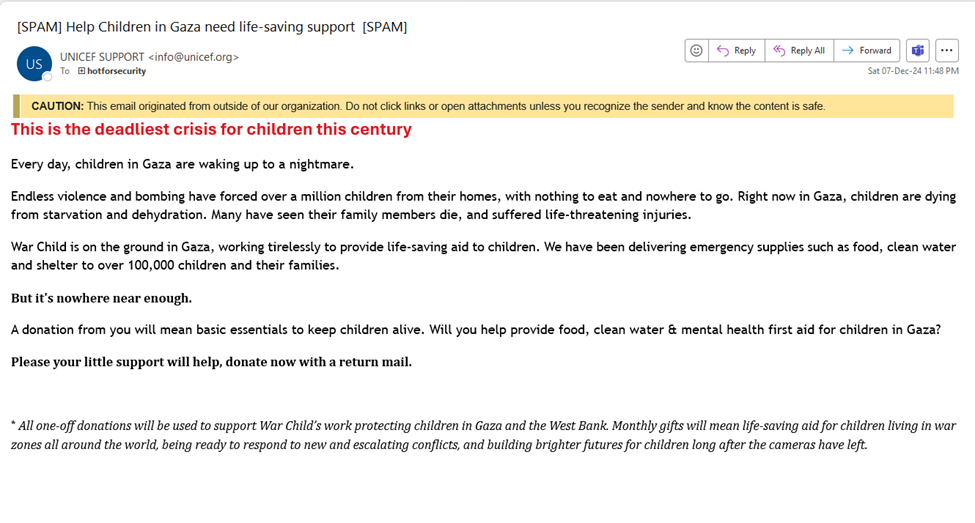
Thirdly, the user can also rely on skepticism as a powerful identification tool. But that feeling that something is not right needs clues to work. One crucial clue is when an attacker straight-up provides direct contact information or banking details or asks for a specific sum of money. Better yet, in some emails, the scammer even tries to persuade the user to pay in cryptocurrency, which is an even redder flag.
But in this email, the attacker doesn’t ask for anything specific, just to respond to the message.
Lastly, Bitdefender offers a free tool named Scamio that allows users to detect if it’s indeed a scam. It works as a standalone chatbot or is integrated into WhatsApp, Messenger, or Discord.
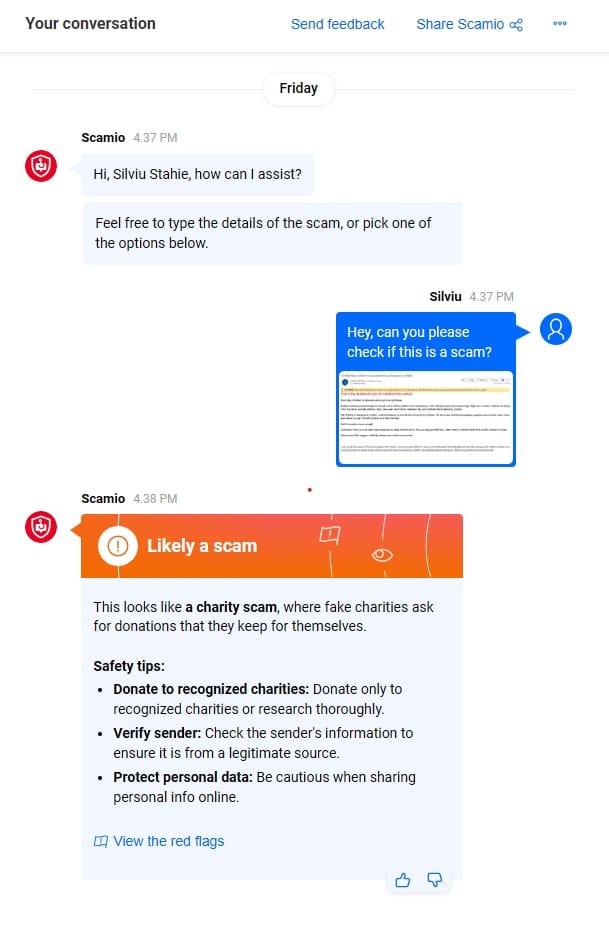
Scamio works intuitively, and the user only has to describe the scam or upload an image, send a link, or send a text. This personal scam-detecting assistant answers immediately.
Read receipts should also make people suspicious
One thing that makes this email stand out is that when you open the message, it asks the user to send back a read receipt. In a normal situation, this tool ensures that the recipient has read the message.
However, the criminal uses the same tool to gather valuable information about the potential victim. For example, if the user confirms the read receipt, it tells the scammer that the email address is active and that the user is not a person who carefully reads emails.
Also, if the user replies, wanting to know how to help, the scammer already knows that the chances of tricking a victim into sending money dramatically increase. In some situations, the victims will be asked to access a link, provide various credentials, or move to another, more “secure” platform.
How to stay safe
- Be wary of emails that claim to come from humanitarian organizations.
- If you want to help, contact the organization directly and not via links or phone numbers provided in emails or other messages.
- Don’t click on links, don’t offer any kind of credentials, and do not agree to move to another platform.
- Do not confirm that you’ve read the message. It only offers precious information to the attackers.
- Use a comprehensive security solution such as Bitdefender Ultimate Security to protect against all types of threats, including email scams.
tags
Author
Silviu is a seasoned writer who followed the technology world for almost two decades, covering topics ranging from software to hardware and everything in between.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks







