‘Security Service Installed Spyware on My Phone,’ says Programmer who Fled Russia

Security researchers have discovered spyware covertly implanted on the phone of a Russian programmer who’d been held in custody by Russian authorities for supplying monetary aid to war-stricken victims in Ukraine.
In June, The First Department, a legal assistance organization founded by exiled Russian human rights lawyer Ivan Pavlov, received a report from Kirill Parubets, a Russian programmer who’d been released from two weeks of administrative detention by the Russian Federal Security Service (FSB).
Masked police officers had knocked on his door in April with guns in their hands. They searched the place, confiscated his phone and laptop, and incarcerated him and his wife over charges of high treason. The reason? He’d been sending monetary aid to Ukrainian citizens.
Tortured and threatened
Police used various methods of coercion to get Parubets to unlock his phone, including beatings and some forms of torture. The beatings allegedly left him partially deaf.
His aggressors then tried to get him to become an informant, threatening him with two decades in prison if he refused. Parubets seemingly had people of interest to the FSB in his address book. He ultimately signed papers according to which he’d admitted his guilt and agreed to become an informant to avoid prison. According to his interviews with reporters, his motive was simple: buy some time to figure out how to flee Russia.
The FSB released him, reuniting him with his wife and their belongings – including his phone and computer.
Soon after, Parubets noticed strange activity on his phone: a notification reading Arm cortex vx3 synchronization. He immediately thought of spyware.
The two miraculously managed to leave the country. It is unclear where they reside at this point.
Using his programming skills, he extracted software logs from his device, contacted The First Department, and relayed his hunch to them. A quick technical analysis confirmed his suspicions.
The logs eventually reached the adept spyware hunters at The Citizen Lab in Canada, who’ve made a name for themselves over the years by contributing valuable insights about notorious spyware programs like Pegasus and Predator.
Their technical analysis again confirmed Parubets’ hunch, and followed with an in depth analysis of the malware.
A new brood of Monokle spyware
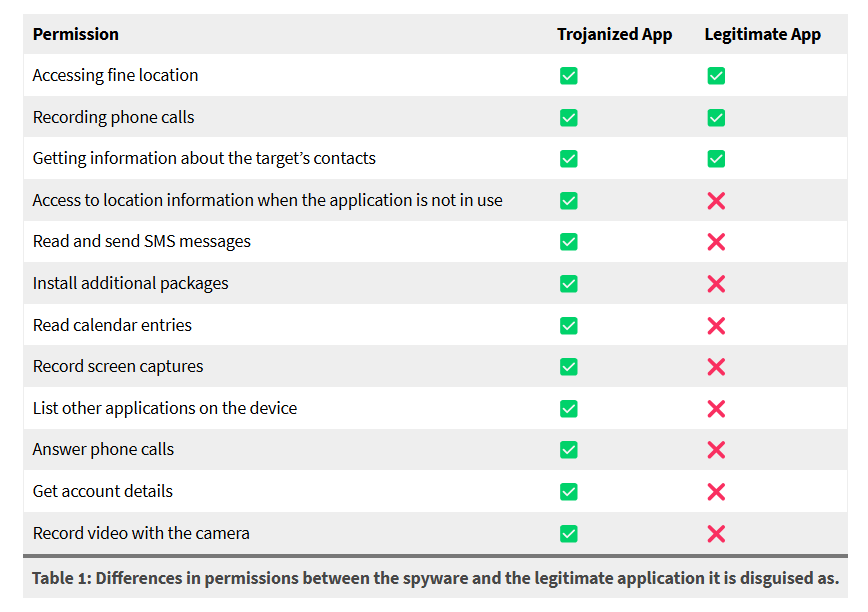
“Our analysis confirms that the application identified by The First Department is malicious, and that it appears to be a trojanized version of the genuine Cube Call Recorder application,” reads the Citizen Lab report.
The two-stage spyware is said to be an updated or remixed version of the Monokle spyware, originally discovered by Lookout researchers in 2019.
The tainted app on Parubets’ phone had been equipped with textbook spyware capabilities, including:
- Location tracking
- Screen capture
- Keylogging
- Recording calls
- Extracting files from the device
- Extracting stored passwords
- Reading messages from other messaging apps
- Adding a new device administrator
- Injection of Javascript
- Executing shell commands
- Extracting the device unlock password
While this particular version of the spyware was designed for Android phones, the analysis uncovered code references to an iOS version, indicating that whoever is developing this new spyware is also focused on Apple hardware.
There are currently no known iOS infections with Monokle spyware.
Credit: The Citizen Lab
The Citizen Lab report describes the malware in depth and offers a list of indicators of compromise (IOC), including the trojanized app’s SHA-256 Sum, commands sent by the C2 server, fields in data and settings files, and permissions requested by the spyware that are not present in the legitimate version of the application.
The fight against spyware continues
Tech giants Apple and Google have been waging war against mercenary spyware for years. The US government recently banned visas for anyone involved in spyware development or deployment, as it violates human rights.
Apple this year announced it was dropping its legal tussle with Pegasus maker NSO Group to avoid having to disclose the threat intelligence it has developed over the years to fight its malware.
It’s worth noting that, in the case of Parubets, authorities already had physical access to his phone after obtaining the passcode to unlock it. So it’s likely that, even with his software updated and security checks in place, they still could implant data monitoring software on the device.
However, since many spyware infections also occur remotely—sometimes with no input from the victim—Bitdefender recommends keeping your device up to date with the latest vendor-issued security patches as the first important step against a spyware infection—especially if you consider yourself a target.
Tech giants Google and Apple issue periodic security updates designed to close holes exploited in spyware attacks.
For peace of mind, run a dedicated security solution on all your personal devices.
On iOS and macOS, keep the trusty Lockdown Mode toggle handy whenever you believe hackers might be targeting you.
To learn more about the spyware threat and how to stay protected, check out our comprehensive guide:
“How Spyware Infects Smartphones and How to Defend Against It”
tags
Author
Filip has 17 years of experience in technology journalism. In recent years, he has focused on cybersecurity in his role as a Security Analyst at Bitdefender.
View all postsYou might also like
Bookmarks
