The Top Five Cyber Threats Windows Users Face Every Day

New sophisticated threats emerge to target the vast Windows user base every year. Yet, despite a growing diversity of malware types and strains, certain key categories are always in place.
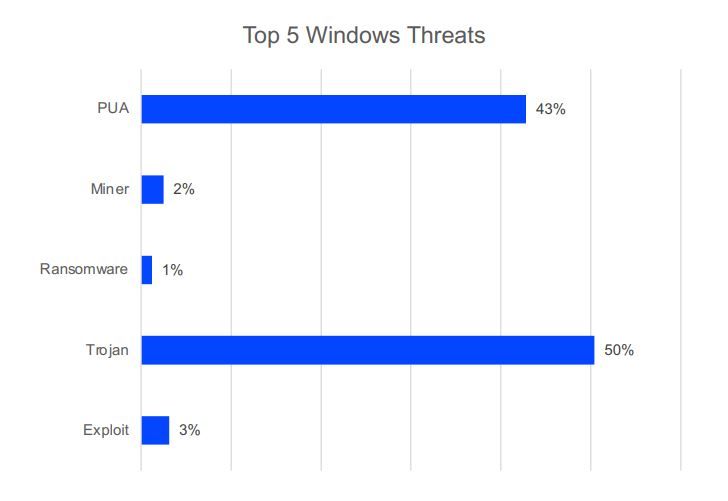
Of the many threats we saw target Windows systems in 2021, five of the usual suspects reared their ugly heads in our telemetry:
Trojans – designed to exfiltrate data from infected systems, spread laterally to compromise other endpoints, and/or download additional malware to expand the attack
Exploits – leveraging known, unknown (zero-day), or unpatched vulnerabilities
Ransomware – stealing and encrypting data; demanding ransom to restore systems and refrain from leaking data
Crypto-miners – stealthily hijacking CPU power to mine cryptocurrency for the bad guys
Potentially Unwanted Applications (PUA) – causing usability and performance issues by installing additional applications and displaying aggressive ads
Trojans
The most common threats detected on Windows platforms in 2021 were trojans, with a 50% share, including specific families like Trickbot, Emoted, Dridex, AgentTesla and many other generic detections.
As shown in our Consumer Threat Landscape Report, Trojans make up the bulk of the threat spectrum as they are often detected in the primary stages of a given attack. Trojans are extensively used to serve up secondary payloads to expand the attack, not least of which are ransomware, crypto miners and malware designed to exploit unpatched weaknesses.
Exploits
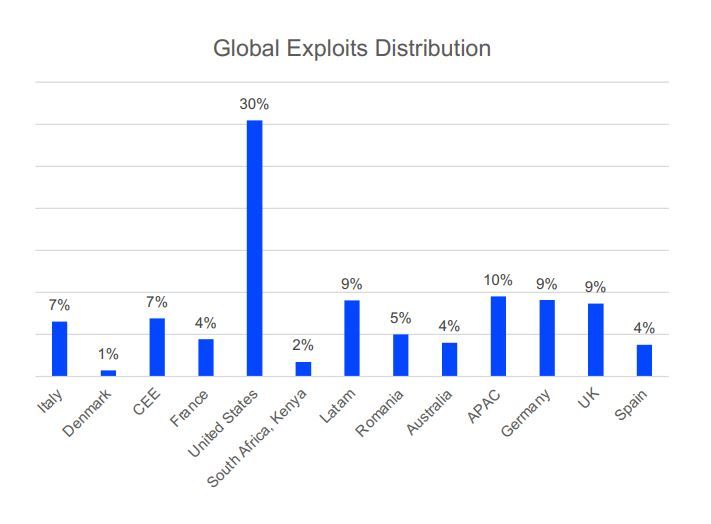
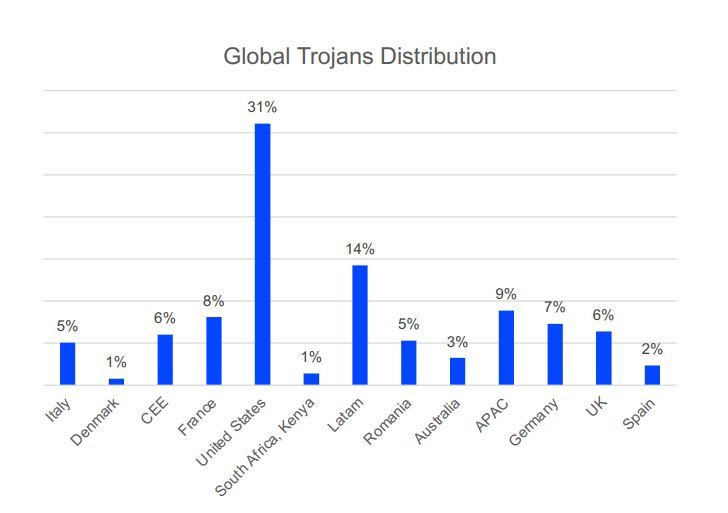
2021 saw a fairly even distribution of exploit-based attacks, with the US registering a notably higher number of attempted attacks – as is typically the case, year after year.
Second in line was the Asia-Pacific (APAC) region, with a 10% share, followed by Latin America, Germany and the UK with 9%, Romania at 5%, Central-Eastern Europe along with Italy at 7%, and France, Spain and Australia at 4%. South Africa and Denmark saw comparatively few attacks, but still enough to make our list.
Ransomware
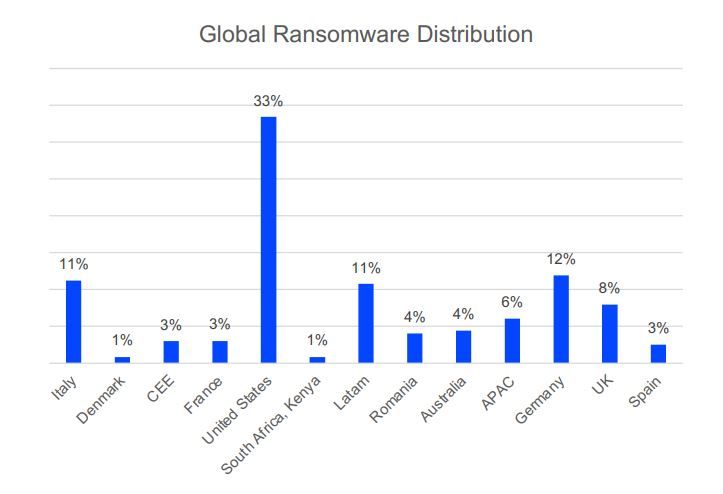
Ransomware reports are typically more common in high-yield geographies, and 2021 was no exception.
The US takes the lead of the pack, with 33% of attacks targeting the North American territory, followed by Germany with a significant 12% share, Latin America and Italy with 11%, UK and APAC with 8% and 6% respectively, Romania and Australia with 4% each, and CEE, France and Spain with 3% each.
The smaller numbers tell an interesting story as to how extortionists distribute their efforts around the globe, depending on what they believe is a high-yield or low-yield territory. In previous years, ransomware attacks were more evenly distributed around the world. In recent times, attacks seem to concentrate much more on profitable territories and industries.
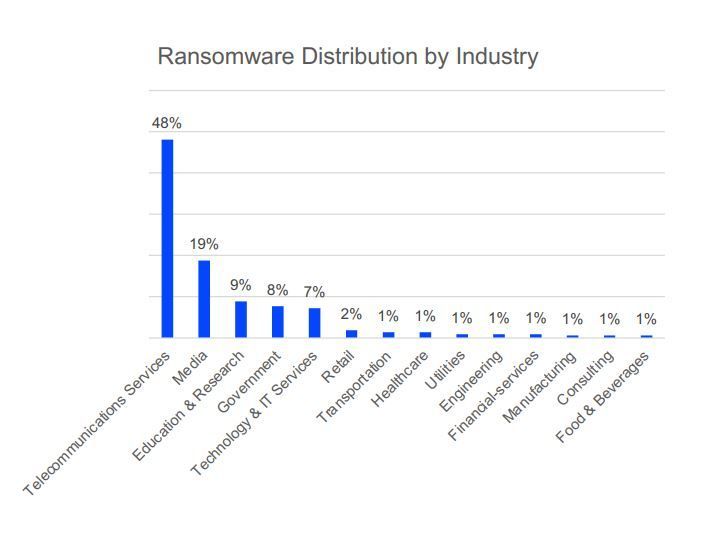
By far the most attacked sector is Telecoms. In 2021, Bitdefender solutions blocked 48% of global ransomware attacks in the telecommunications industry alone. Media takes second place at a distant 19%, followed by Education & Research at 9%, Government at 8%, Technology & Services at 7%, Retail at 2%, and several other verticals, each with 1% of the pie.
Coin miners
Crypto mining is not necessarily a hazard in and of itself. After all, one could engage in this activity on purpose, leveraging their computing power to generate crypto. But if hackers can hijack your computer and use it to mine crypto for themselves, that means they exploited a weakness on your behalf. These weaknesses could be exploited for more than just crypto mining.
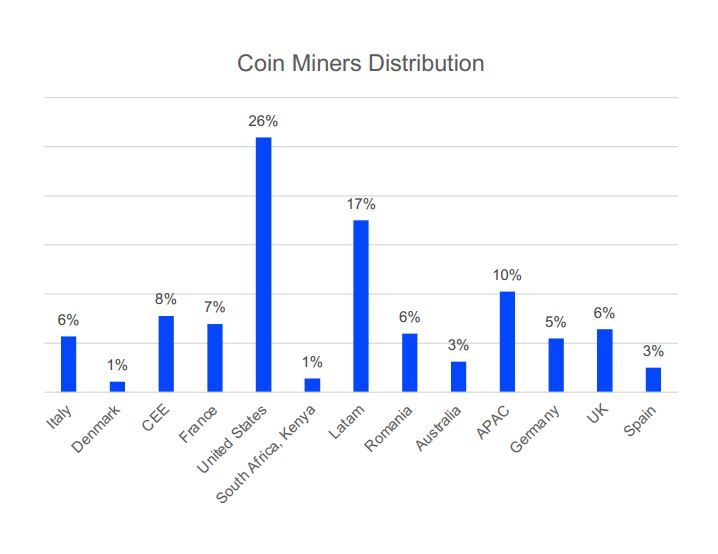
There’s no shortage of ways to get infected with a coin miner. From data breaches to PUAs to warez downloads, coin miners crop up all the time in our data, and 2021 was no exception. Like most threats analyzed in this report, coin mining is mostly prevalent in high-yield regions where computing power abounds. As such, the Americas again take the lion’s share, with a combined 33%, trailed by the Asia-Pacific region with 10%. Other areas analyzed here are seeing fairly even, single-digit distribution.
Potentially Unwanted Applications (PUA)
PUAs walk a thin line between nuisance and malware. Most simply hog system resources, but they often also display aggressive ads, collect data without your consent, and may even perform secondary downloads that might hide actual cyber threats, like crypto miners or data-stealing malware.
PUAs are most commonly found as freeware, repackaged applications, system cleaners or other utilities with hidden functionality. Others hijack the user’s browser, altering its functionality – like changing the default search engine and installing plugins – without consent.
Of the more dangerous PUAs are those that can modify third-party apps, download additional software behind the scenes, or alter system settings – which can mushroom into actual security and privacy issues.
And there’s also the scareware-type of PUA that displays exaggerated or bogus notifications claiming the system is exhibiting problems – like a malware infection – that requires immediate attention
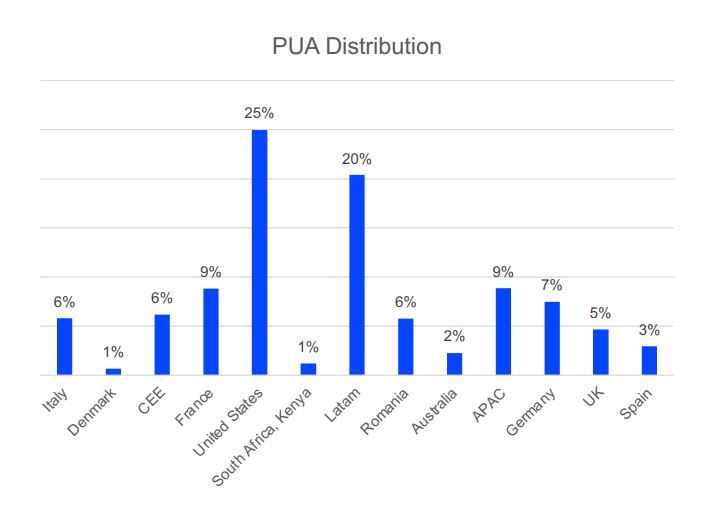
Accounting for a third of all threats directed at Windows systems, PUA operators prefer large territories with massive PC user bases. The US and Latin America again make up the bulk, with 25% and 20% of PUA reports, respectively. This high concentration of PUA activity on a single continent leaves all other areas in the single digits.
Windows users worldwide face these threats, and many others, on a daily basis. Security solutions like those offered by Bitdefender are specifically designed to detect and block these hazards, all while helping users steer clear of shady sites and online scams. Learn more at https://www.bitdefender.com/solutions/.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks







