Top 10 3Q E-Threats: Newer Threats Dominate
While the international malware top has barely changed for more than three years, with AutorunInf and Downadup easily dominating the e-threat landscape, malicious operations have reached a turning point in the last three months – older families of e-threats are fading away in the face of newer, more aggressive adware applications.
Research in the past three months confirmed an old supposition that malware as we know is about to change. Old threats such as Downadup don’t scare people anymore. At least not computer users who stick to the minimum safety guidelines: up-to-date operating system and antivirus solution.
Today’s most important two categories of e-threats are much more subtle, and may be somewhat related to each other. On one side, there is the on-going cyber-warfare – a malicious business that is highly-targeted, but which is somehow inflicting collateral damage as source code for these e-threats get open-sourced and re-used by small-time cyber-crooks.
On the other side it’s the commercial aspect of malware: the extremely-subtle families of adware that stay on the grey line, making huge amounts of money for its operators. Funnily enough, few see in adware a serious threat. For most people adware is annoying advertising and nothing more. But there’s more to it than that.
Modern adware is harder to track, converts more and can be delivered to broader audiences thanks to the multitude of applications that ship with an adware installer. It is way harder to block because of its position on the thin line between legal and illegal and, well, it’s made it into the tops. The international top, that is.
Users hardly fear adware and almost never see it as a money making source for someone else.
Moreover, the security community hesitates to speak about adware to avoid confusion regarding legitimate companies or freelancer programmers that use a form of adware to monetize their services or products. The fact that these revenue services are being used by cyber-criminals and legit companies alike makes it even more confusing to the end-users and deforms their perception of how free, ad-supported software should look like.
Modern adware not only provides a living for crooks through banners in products or pay-per-1k-installations of third party applications such as video players, PDF readers and other utilities that one may – or may not – want on their machines. Just like any business that involves advertising, these applications involve data gathering and take more data than the regular metrics: they collect extensive reliable databases of users, along with information about their identity and habits that could lead to money. Since malware is about making money. Or not?
One of the wildest suppositions about the importance of funds from advertising was launched during the Search Engines Strategies Conference in Chicago in 2006, when Webmaster Radio’s Jim Hedger published an investigative report about the way terrorist cells such as Al Qaeda, Hezbollah and others were using Google Adsense and advanced click-jacking technologies to make money online, and funnel it through charities only to redirect it to Jihadi operations.
Adware keeps pouring billions of dollars to organizations in the revenue sharing program. The nature of the business makes it extremely difficult to evaluate the exact revenue, but illegal adware was estimated at around $1.6bn a year in 2005. And that was way before adware became visible on the e-threat map. Back in the wild speculation area, the money could have a variety of destinations, including funding the engineering of extremely-expensive e-threats such as Stuxnet, Duqu, Flamer or Gauss whose development costs alone range in the million-dollar mark per item. Of course, these are just suppositions. But cybercrime is a complex ecosystem that can squeeze enough revenue for funding complex e-threats or enlarging the portfolio of infected computers with no questions asked.
The in-depth malware top follows
This quarterly malware report unveils a diverse collection of e-threats that have bothered users worldwide for the past three months. From old threats going steady – Downadup, Sality or Autorun – to readapted versions of unauthorized key generating scripts or code pushing commercials, this top has it all.
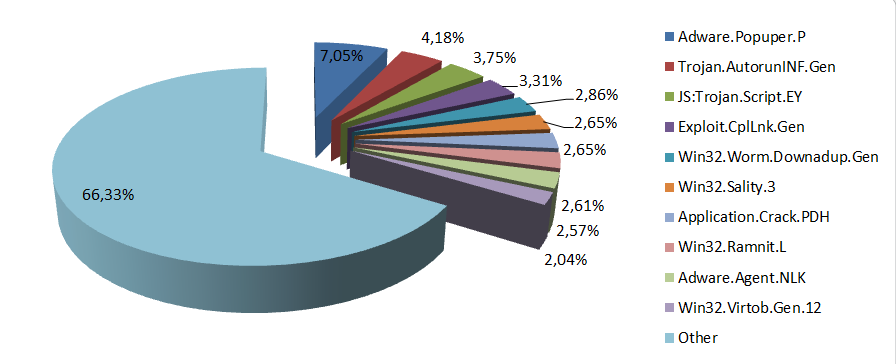
Malware distribution for July – September 2012:
The top ranking e-threat in the quarter is Adware.Popuper.P an adware-related installer that spies on user behavior to offer target-oriented advertisements. It first searches for users’ habits and likings, collects relevant data for preferences to download and install related add pages. Sometimes it downloads clean applications as well.
Trojan.AutorunInf.Gen counts a 4.18% infection rate of global malware. Compromised external devices, such as USB sticks, hard disks and memory cards, facilitate installation of a malicious piece of code on them or transfer e-threats on other devices they come in contact with. Users should scan removable devices regularly, especially if they plug them into library computers, copy shops and other public locations known as sources of infection.
As of 2011, Bitdefender released a free USB Immunizer tool to protect against prominent Autorun-based malware threats – the USB Immunizer -available on the product’s page at the BitDefender Labs.
Third is JS:Trojan.Script.EY a malformed JavaScript content injected into clean html and JavaScript files to redirect users towards malware-laden websites and execute malicious code on the compromised system. A few months back we saw a news portal redirecting users towards websites containing malware.
Accounting for 3.31% and ranking fourth is Exploit.CplLnk.Gen a detection for shortcut files that uses a vulnerability in the Windows OSs to execute arbitrary code. The vulnerability was also exploited by the infamous Rootkit.Stuxnet.
Win32.Worm.Downadup.Gen sees a slight downward movement since the beginning of the year. This threat is nonetheless constant among malware compromising computers all over the world. Ranking fifth, with 2.87 percent, this worm exploits a vulnerability in older Microsoft operating systems. A simple OS update should save users of this menace.
Sixth is Win32.Sality.3 a virus that infects all executable files on the system. With a code that changes constantly, Sality is hard to detect and annihilate while the rootkit component kills antivirus applications it finds on the infected system.
Application.Crack.PDH is the application, ranking seventh, that generates unauthorized registration keys to defeat the commercial protection of shareware software products making piracy an industrious factor of infection by exposing computer users to other online threats.
Next e-threat in the top is the resourceful Trojan.HTML.Ramnit.L, with 2.61% of all malware triggered worldwide. Polymorphic file-infector at its core, Win32.Ramnit spreads via infected EXE, DLL and HTML files or via physical storage media such as flash drives, external hard-drives and CF cards. The virus infects all EXE, DLL and HTML files on the computer with its own malicious code. Whenever an infected file is run, the virus attempts to connect to and download other files from the Internet.
Ramnit recently changed its behavior and was used for financial fraud. Once installed, Ramnit continuously communicates with the Command and Control (C&C) server, reporting on its status and receiving configuration updates. The latest version of the Ramnit worm was caught stealing Facebook log-in credentials and spamming friends on the social-networking site to spread itself, replacing the old e-mail spreading technique.
Adware.Agent.NLK (placed 9th with 2.57%) is the second adware-type e-threat in this quarter. Adware.Agent.NLK hijacks the browser and redirects searches toward certain commercial webpages and online shops. Apart from being annoying, these threats gather data and create online shopping profiles of its victims.
Win32.Virtob.Gen is one of the most famous polymorphic file infectors. Written in assembly language, it infects exe and SCR files by appending its encrypted body to the end of these files. After infection, the virus tries to connect to an IRC server where it gets in touch with its attacker and awaits further instructions. We’ve seen this virus infecting a worm by mistake and talked about it here.
Bitdefender July – September 2012 Top 10 E-Threat list includes:
| 1. | Adware.Popuper.P |
7,05% |
| 2. | Trojan.AutorunINF.Gen |
4,18% |
| 3. | JS:Trojan.Script.EY |
3,75% |
| 4. | Exploit.CplLnk.Gen |
3,31% |
| 5. | Win32.Worm.Downadup.Gen |
2,86% |
| 6. | Win32.Sality.3 |
2,65% |
| 7. | Application.Crack.PDH |
2,65% |
| 8. | Win32.Ramnit.L |
2,61% |
| 9. | Adware.Agent.NLK |
2,57% |
| 10. | Win32.Virtob.Gen.12 |
2,04% |
| Other |
66,33% |
All product and company names mentioned herein are for identification purposes only and are the property of, and may be trademarks of, their respective owners.
tags
Author
A blend of product manager and journalist with a pinch of e-threat analysis, Loredana writes mostly about malware and spam. She believes that most errors happen between the keyboard and the chair.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks









