Unpatched D-Link routers targeted in malicious DNS hijacking campaign

Cybercriminals have been hacking into home routers for the last three months, meddling with DNS settings to redirect users surfing the web towards malicious websites.
DNS records work rather like a telephone book, converting human-readable URLs like google.com into numbers understandable by the internet. Problems occur, however, if someone succeeds in changing the lookup – pointing users’ browsers that are trying to reach google.com to different websites which may be deliberately mimicking the site they have replaced.
The attack, known as DNS hijacking (or DNS redirection), can be used by online criminals to direct traffic to a malicious website which may try to infect a visiting computer with malware, display revenue-generating ads, or phish for usernames and passwords.
A user may be unaware that anything is amiss, because their browser continues to tell them that they are on “google.com” or the login page of their online bank.
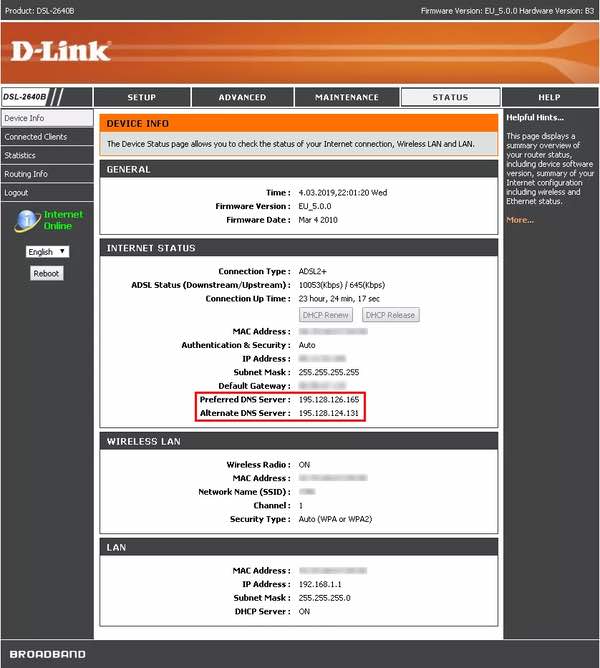
In a blog post, security researcher Troy Mursch says that he first saw evidence of the attacks on December 29, 2018, when multiple models of D-Link DSL modems were targeted. These included the D-Link DSL-2640B, D-Link DSL-2740R, D-Link DSL-2780B, and D-Link DSL-526B routers.
In this attack, the DNS settings of hijacked devices were altered to point to a rogue DNS server at an IP address hosted by OVH Canada.
In February 2019 a new attack wave began, again targeting vulnerable D-Link routers, and again pointing hacked devices to a rogue DNS server hosted by OVH Canada.
Last month, on March 26, the latest wave of attacks struck – broadening out the range of consumer routers being targeted to include the ARG-W4, SSLink 260E, Secutech, and TOTOLINK models.
These most recent attacks redirected DNS requests to rogue DNS servers hosted in Russia by Inoventica Services.
While we don’t know yet precisely which websites the attackers were redirecting traffic from through their DNS hijacking, a likely scenario is probably that it was for the purposes of phishing passwords on fake banking sites.
Attacks like these underline the importance of maintaining good hygiene on your internet-enabled devices. The D-Link vulnerabilities exploited in the attacks were patched years ago, but many users have still not installed the fixes – probably due to a lack of awareness about the issue.
Needless to say it has proven difficult to alert the average consumer of the threat of DNS hijacking because of a general lack of knowledge about what a DNS server is, or what it does.
It is essential that home routers are kept up-to-date with the latest security patches. Routers still running out-of-date versions of their firmware may suffer from vulnerabilities or security holes that allow an attacker to meddle with its settings.
tags
Author
Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks








