Why Use an Authenticator App Instead of SMS?

Two-factor authentication (2FA) has become imperative in today’s digital world, as criminals have learned to compromise almost any password. While SMS-based 2FA is better than no 2FA at all, authenticator apps have the edge because they provide stronger safeguards against threat actors looking to hack into your online accounts.
Twitter’s shift from SMS-based 2FA stirred up quite a bit of controversy and opened a window of opportunity to flood the app stores with scammy 2FA apps.
Twitter said in February that scammers were abusing phone-number-based 2FA. CEO Elon Musk himself argued at the time that SMS-based 2FA was not just insecure, but also a waste of money.
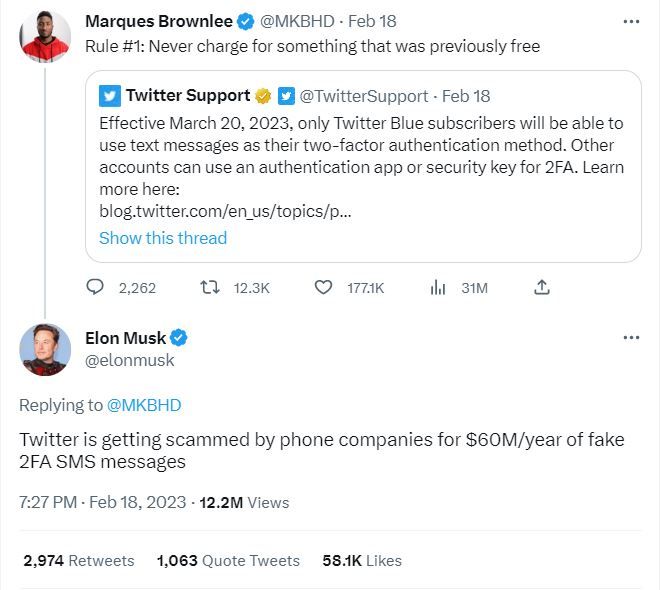
Whatever side of the fence you’re on, the truth is that SMS-based multi-factor authentication has quite a few weaknesses that criminals are exploiting.
Weaknesses of SMS 2FA
SIM swapping is one of the best examples of how a thief can defeat 2FA and, say, empty someone’s bank account or crypto wallet. In 2018, crypto investor Michael Terpin – the founder and CEO of Transform Group – got swindled out of almost $24 million by a teenager who intercepted the 2FA codes sent to his number.
Threat actors will use data leaks, public records or social engineering to get your phone number, then bribe or trick a carrier employee to port your number to a duplicate SIM card they control. This enables them to receive your SMS verification codes and break into your various online accounts.
SMS phishing, or smishing, is another popular method fraudsters use to steal verification codes and gain access to a person’s account.
The technique can also facilitate extortion, as was the case of 20-year-old Dennis Su who used stolen records that hackers posted online to send text messages to people threatening to compromise their identity unless they transferred $2,000 to his bank account.
It’s also important to know that SMS messages are transmitted over unencrypted channels, which means they can be intercepted and read by anyone motivated to intercept the message.
And of course, SMS messages can be easily read by anyone with physical access to the victim's phone. Also, there is no way to prevent or control where the SMS is delivered, and SMS 2FA can sometimes be laggy or too indulgent with the code’s expiration time, giving attackers ample opportunity to exploit any weakness.
Pros of using a dedicated authenticator app

Authenticator apps are not only faster and more reliable than SMS 2FA, they also enforce an additional layer of security, such as a passcode, a password or biometrics (i.e. fingerprint).
Authenticator apps work locally, meaning there’s no way for an attacker to intercept your codes – unless they’ve infected you with data-stealing malware, but that’s a different discussion.
An authenticator app will show a clear countdown timer for your codes and will generate new ones when the time expires, making it hard for anyone to intercept those codes without access to your phone.
Most importantly, authenticator apps exhibit none of the weaknesses of SMS 2FA.
As mentioned above, scammy 2FA apps can be a problem, so only use a trusted authenticator app from the likes of Google or Microsoft. Apple users can also opt for iOS’s built-in authenticator. Apple’s tool may not be as intuitive as standalone authenticator apps, but it’s still reliable and secure.
Note that multi-factor authentication doesn’t protect against malware, so consider using a dedicated security solution on your personal devices, including your phone.
tags
Author
Filip has 15 years of experience in technology journalism. In recent years, he has turned his focus to cybersecurity in his role as Information Security Analyst at Bitdefender.
View all postsRight now Top posts
How to Protect Your WhatsApp from Hackers and Scammers – 8 Key Settings and Best Practices
April 03, 2025
Outpacing Cyberthreats: Bitdefender Together with Scuderia Ferrari HP in 2025
March 12, 2025
Streamjacking Scams On YouTube Leverage CS2 Pro Player Championships to Defraud Gamers
February 20, 2025
How to Identify and Protect Yourself from Gaming Laptop Scams
February 11, 2025
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks