Attackers Pose as Account Owners via Facebook Login Flaw

Facebook vulnerability breaks down the convenience of social login authentication. Insufficient security validation allows attackers to impersonate Internet users and gain password-less access to any of their online accounts.
Social logins are an alternative to traditional authentication. They offer users a convenient way to sign in to their web accounts without entering their username and password. Most websites offer social login through Facebook, LinkedIn, Twitter or Google Plus. Bitdefender researchers found a way to steal a user’s identity and gain access to his web accounts using Facebook’s Login plugin.
“This is a serious vulnerability – it allows attackers to login on most websites that feature Facebook Login,” Ionut Cernica, Bitdefender vulnerability researcher says. “This means an attacker can make payments on the user’s behalf on an e-commerce site, for instance.”
For the attack to succeed, the email address of the victim must not be registered on Facebook. As we know, most internet users have more than one e-mail address published on different websites and thus, publicly available. It’s simple enough for the attacker to get one of these addresses and register a Facebook account with it.
To verify the identity of a user without exposing his credentials, Login with Facebook uses the OAuth protocol. Through OAuth, Facebook is authorized to share some user information with the third-party website.
How the spoofing is done
The researcher managed to bypass the confirmation step typically required when registering a new Facebook email address.
He created a Facebook account with the victim’s email address.
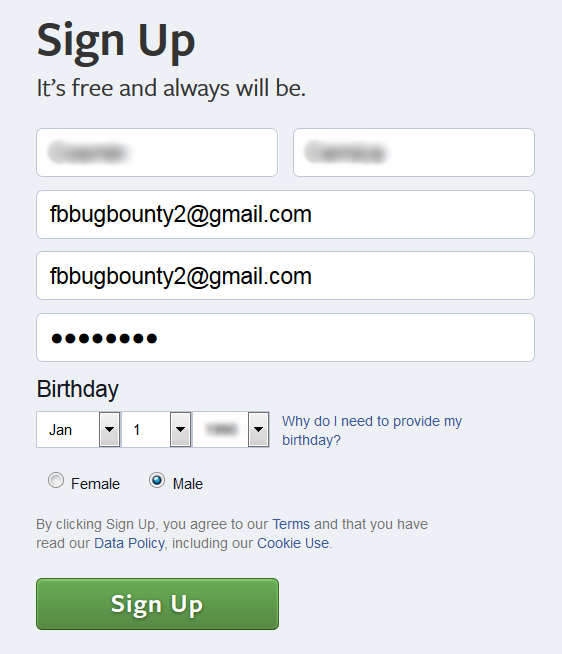
Fig. 1 Attacker creates new Facebook account with victim email address
During registration, he swapped the email address for one he controlled.
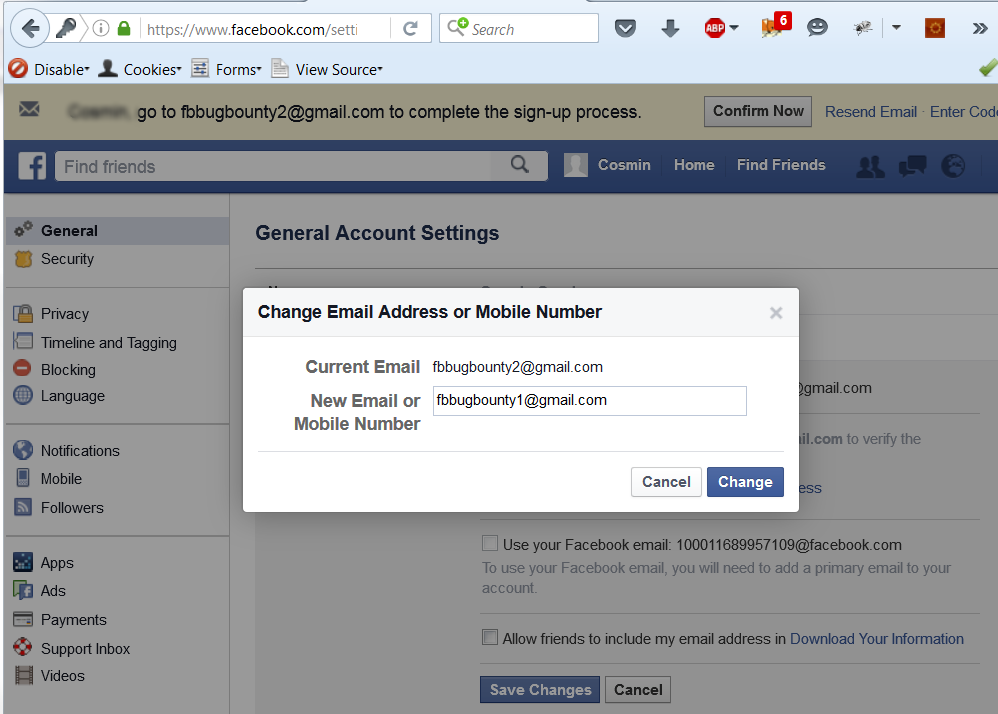
Fig. 2 Attacker changes victim email address with his own
After refreshing the page, it looked like the victim’s email address had also been validated.
When he tried to sign in via the “Facebook Login” button – with the victim’s email address – on another website, he was asked to confirm his own email address, not the victim’s.
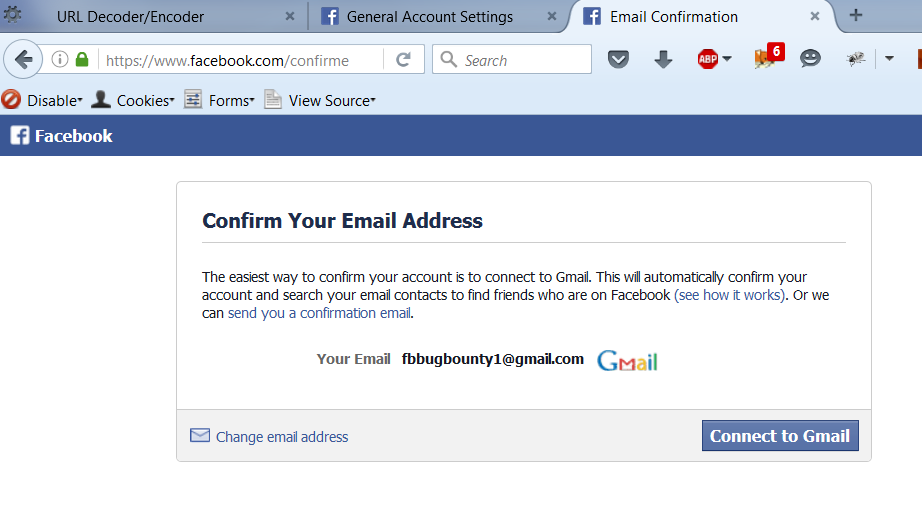
Fig. 3 Attacker is asked to confirm own email address
Under account settings in Facebook, the victim’s address was the primary contact, even though the researcher only confirmed his personal account.
“I used Facebook Login again and decided to switch the primary contact from the victim’s address to mine, then switch them again to make the victim account as the primary account. This is an important step to reproduce the issue,” Ionut added.
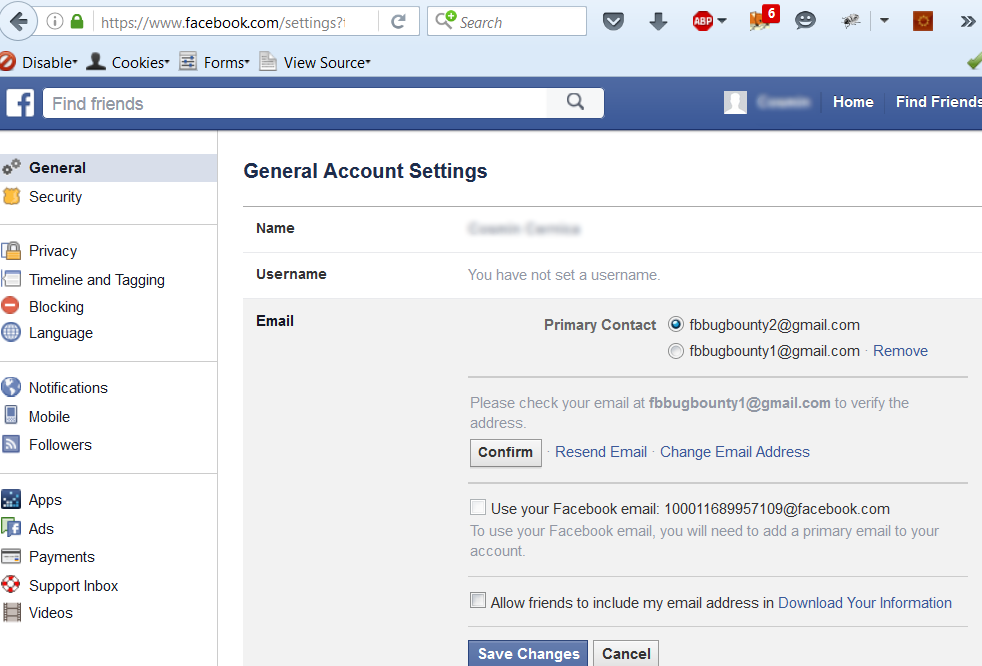
Fig. 4 Attackers sets victim’s email address as primary contact
On another website, he used “Facebook Login” to successfully authenticate as the victim. The site matched the email address of the victim – passed to it by Facebook – to the existing account and allowed the attacker to control the account.
“The identity provider – in this case, Facebook – should wait until the email address has been verified,” Ionut says.
Facebook fixed the vulnerability after notification from the Bitdefender security researcher.
tags
Author
Alexandra started writing about IT at the dawn of the decade - when an iPad was an eye-injury patch, we were minus Google+ and we all had Jobs.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks













