Newest Windows Version Runs Oldest Malware Still in Wildcore

Ever since the release of Windows 8, one of the key marketing points of the new OS made in Redmond was built-in safety. Given that we’re a curious bunch of people here in the Labs, we decided to take an Enterprise version of Win 8 for a spin and see for ourselves how it performs in the vanilla state.
So, we took samples of the most frequently-encountered 100 families of malware as we’ve seen them in the past six months and tried to see how many of them can actually run on the Windows 8 system successfully, despite the default presence of UAC, Windows Defender and the rest of security enhancements snuck into the OS (ELAM and Safe Boot, for instance).
Testing methodology
Step 1: In order to carry the test, we used two identical machines running stock configurations of Windows 7 and Windows 8 respectively.
Step 2: After running a malicious sample and assessing whether the computer has been compromised or not, the system is rebooted to a clean operating system and testing resumes. It is assumed that the piece of malware has successfully infected the PC when it has spawned its own process and kept that process running until reboot.
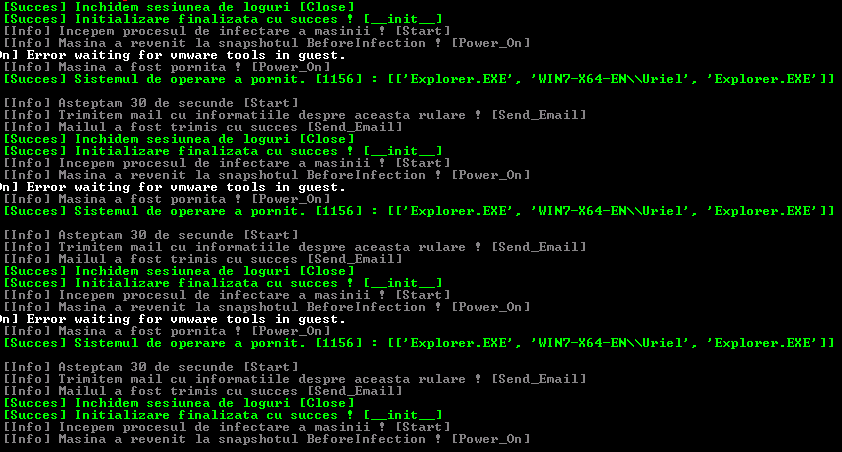
Controlling the machines with one script
Step 3 – Testing on Windows 7, Windows 8 and Windows 8 with Windows Defender: The malware test on Windows 8 was carried in two steps, as follows:
a) In order to ensure that both Windows 7 and Windows 8 environments are on par, we disabled the anti-malware solution that ships by default with Windows 8 in the first test.
b) The second test was a real-life scenario, with Windows 7 versus Windows 8 + Windows Defender.
Step 3: The malicious sample set was built of 380 samples of the most popular 100 families of malware in the past six months, as reported by the Bitdefender Real-Time Virus Reporting System. These samples were hosted on an internal FTP repository and copied to the machine after booting it up.
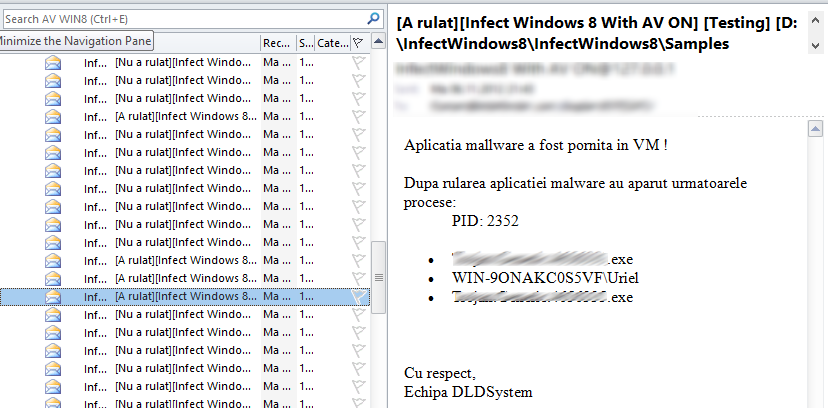
Step 4: After running the sample in the selected environment, the python script emails a detailed report with the process differences between the original system and the infected one.
Reports on spawned processes sent via e-mail
Imagine our surprise when, among reports of failed executions triggered by malware that either tripped Windows Defender detections or got blocked by UAC, we saw 7-year old malware such as the Zlob Trojan, a couple AutoIT worms and two generic mass-mailer worms run without any “compatibility” issues.
Shortly put, if the piece of malware to be run does not require UAC elevation, does not try to install a rootkit driver and if it’s not intercepted by Windows Defender, it gets executed.
It is true that Windows 8 comes with great innovations in terms of security, such as protection against rootkits when an antivirus runs atop of the OS, but last time we checked, rootkits accounted for roughly 5 percent of the global production of malware. UAC, another feature that is supposed to help mitigate the impact of malware, has been long enough on the market to force malware creators redesign their creations not to require extra privileges, so we didn’t expect it to be a great differentiator.
Bottom line, if you’re an early Windows 8 adopter or if you’re planning to deploy it anytime soon, you should keep in mind that most of the innovations on security built into the new OS are meant to assist the antivirus in the fight against malware, and not to replace it.
[Python magic and test machine setup courtesy of Alex Coman, Malware Researcher]
tags
Author
Right now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks