SMS Scams Exposed: A Look at Ongoing Campaigns Worldwide

SMS phishing might not sound like much of a threat. People could think that, after all, who still uses SMS nowadays? In reality, though, SMS remains a vital channel of communication for many businesses and even some institutions. Criminals often try to spread their fraudulent campaigns using SMS and messages relevant to our times.
Scam Alert, one of the many features available in Bitdefender Mobile Security for Android, notifies users when they receive a message containing suspicious links that might attempt to steal financial data, credentials and other sensitive information.
All cross-platform products included in Bitdefender Total Security benefit from Scam Alert's detections as the information quickly disseminates to the entire user base as soon as a single URL is identified as dangerous.
Criminals tailor their messages to the region they're targeting. In some countries, they might try to trick people into thinking the message is related to energy prices. In others, they might write about tracking packages or send users to website hosting malware. The messages criminals use in every campaign change depending on the public's interest. For example, as we approach the holiday season, expect a plethora of SMS messages warning about lost packages.
Criminals build their campaigns knowing that any links they provide have a high chance of being detected, so they change the message wording and links in an attempt to remain anonymous. Bitdefender has been working on a security research technology that can identify and group messages that seemingly have nothing to do with one another but are, in fact, part of the same campaign from the same operators.
This technology is instrumental when criminals use the socio-political landscape to craft messages, exploiting the energy crisis and trick people into clicking on malicious links.
Attackers taking advantage of the current social and political state
We looked closely at all the major SMS phishing campaigns of the past 30 days worldwide that our Scam Alert telemetry caught in its net, including in the first weeks of November. The telemetry contains everything from energy bill scares to lost packages and everything else in between.
One common theme you'll notice is the URLs used in the attacks. Most of them have legitimate-sounding words in the link address to trick people into thinking they're accessing an official domain when, in fact, they're controlled by attackers who just want to steal information. Many of the domains shown in this research don't work anymore, but new ones pop up every day, which is why it's essential to find and group them as quickly as possible.
UK Energy Bills Phishing
In the UK, the most prevalent scam targets people's concerns around electricity bills. The government has already issued warnings, but the scams continue to spread. Criminals use the accurate information that the UK government is offering a £400 grant in some situations but pervert the message to fit their phishing campaign.
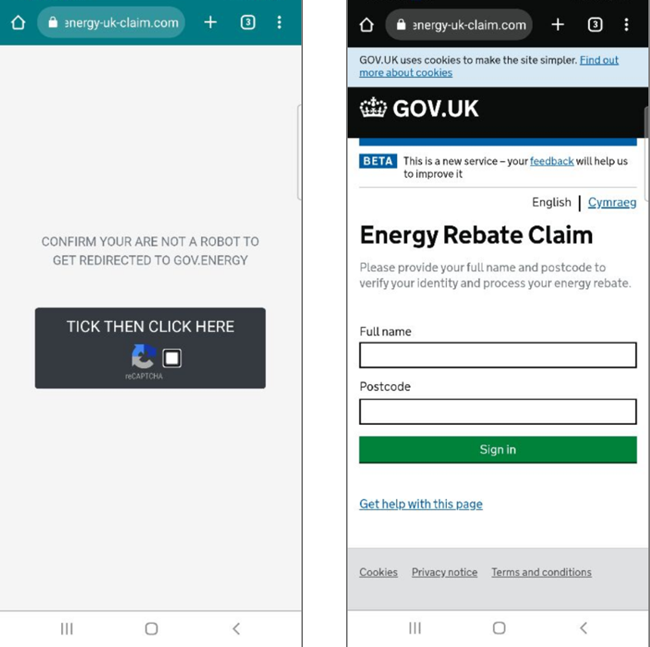
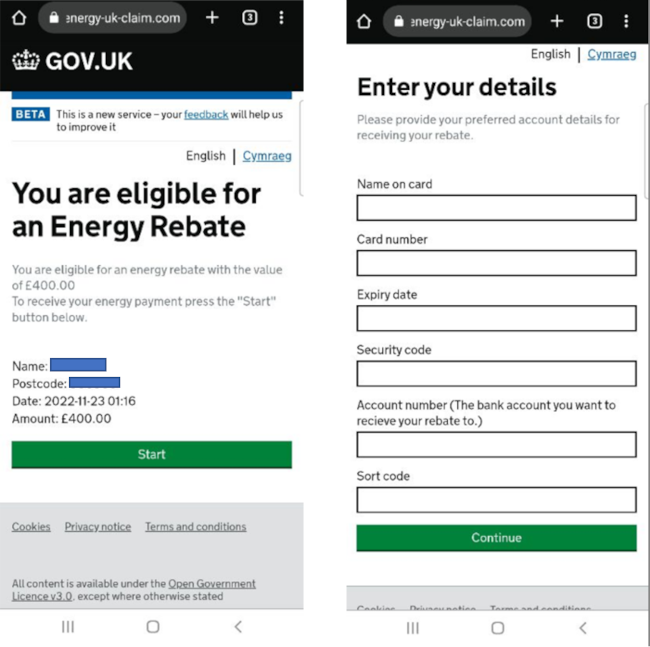
URL examples:
- hxxps://my-support-scheme.com
- hxxps://mysupport-scheme.com
- hxxps://my-energy-application.com
- hxxps://energy.support-rebate.com
- globaldirected.com
- rechargedservice.com
- hxxps://enterpriseglobaluk.com
- hxxps://support-scheme-help.com
- hxxps://reduceduk.com
- hxxps://gov-energy-uk.live-rebate.in
- hxxps://gov-energy-uk.claim-rebate.in
- hxxps://energyukgov-scheme-rebate.com
- hxxps://energy-bill-discount.com
- hxxps://energy-online-db21.com
- hxxps://gov-energy-gb.live-rebate.in
- hxxps://energybills-support.com
- myapply-bill-support.com
- hxxps://myenergy-support-id.com
- hxxps://personal-rebate-uk.web.app
- hxxps://rebate-energy-gov.web.app
- hxxps://gov-uk-bills.web.app
- hxxps://bill-rebate-uk.web.app
- hxxps://rebate.energy-uk-claim.com
Germany:
This phishing campaign in Germany also focuses on energy bills, but it's tailored to Germans, with scammers trying to impersonate the Federal Ministry of Finance. The messages say the user will receive a sum of money or a refund related to their energy bill if they click the link. When opened, the links redirect to a fake website purporting to be the Federal Ministry of Finance. There, users are asked to input their bank account data to receive the money. The officials have warned that no such payments exist and that users must not give out their data.
When the website is opened, the user must confirm they are not a robot and submit a captcha.

Then, the user enters the website and sees the logo of the Federal Ministry of Finance, along with a list of banks. From there, the user is prompted to log in to their bank account to receive the payment.
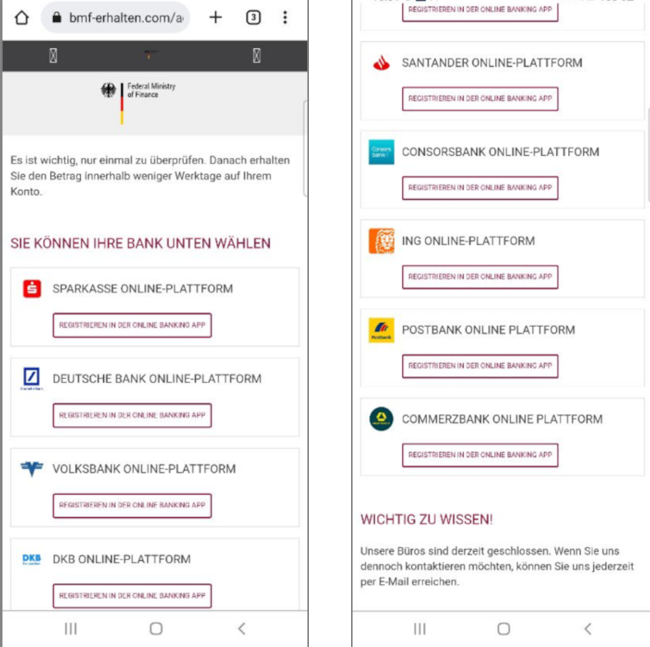
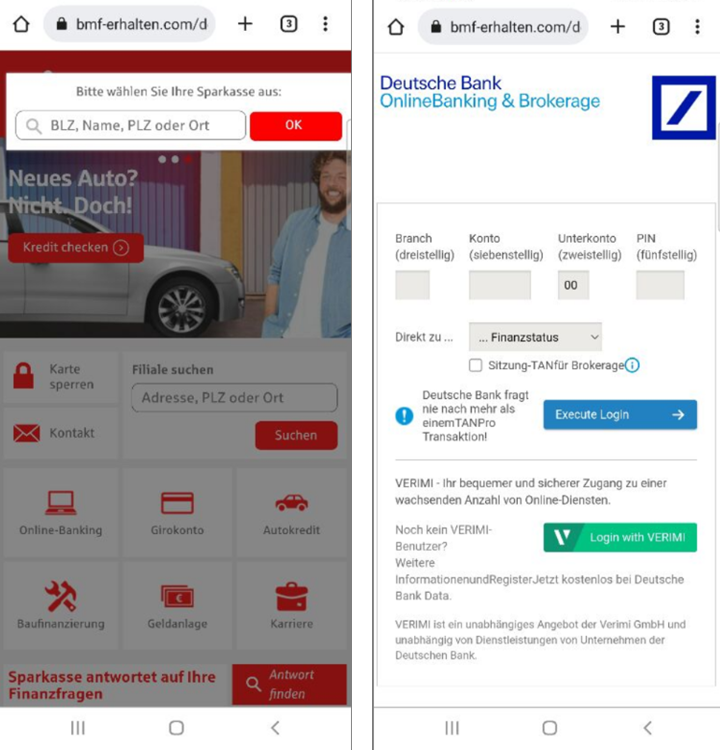
If the user clicks on a bank, a phishing page opens, imitating the real bank’s login pages. Even though the login forms resemble the official ones, the address bar shows that we are still on the first site, which imitates the Federal Ministry of Finance, and not on the banking one.
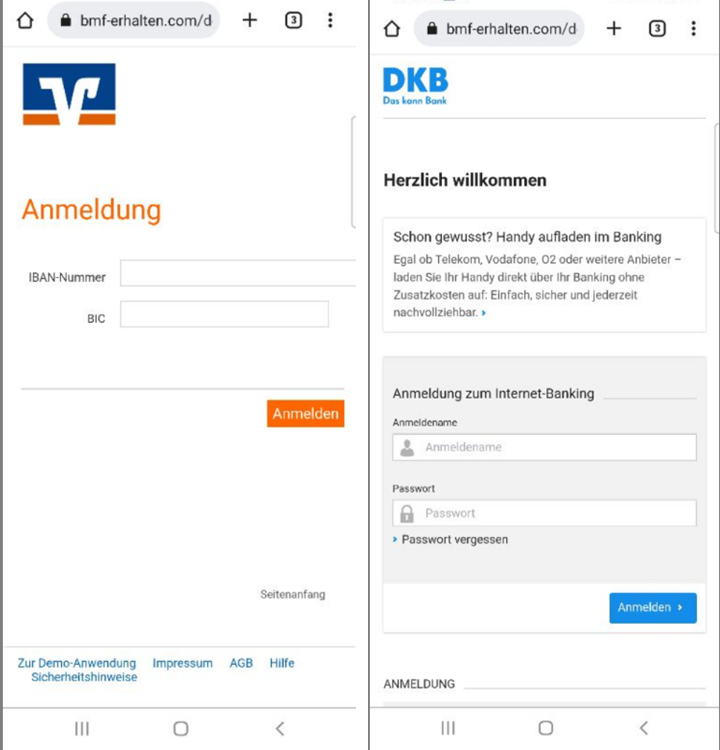
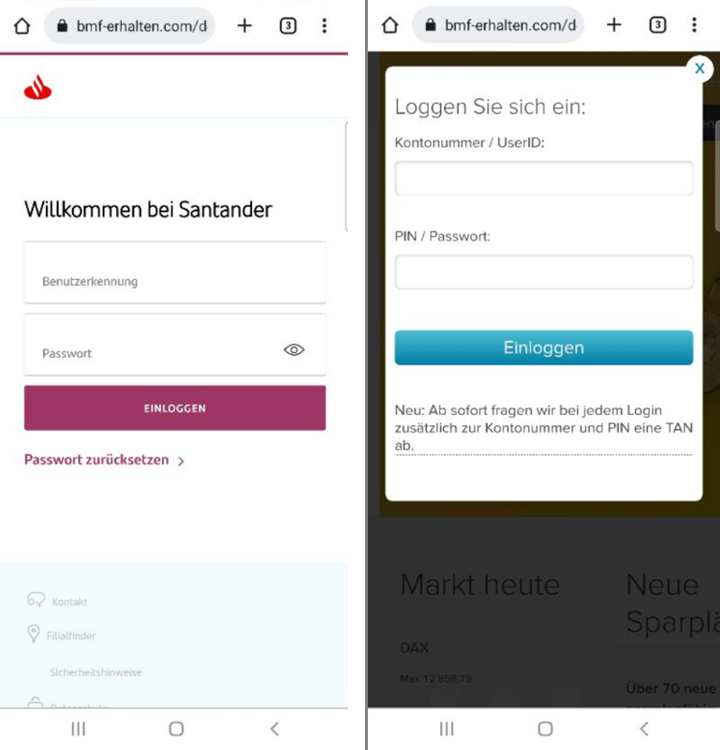
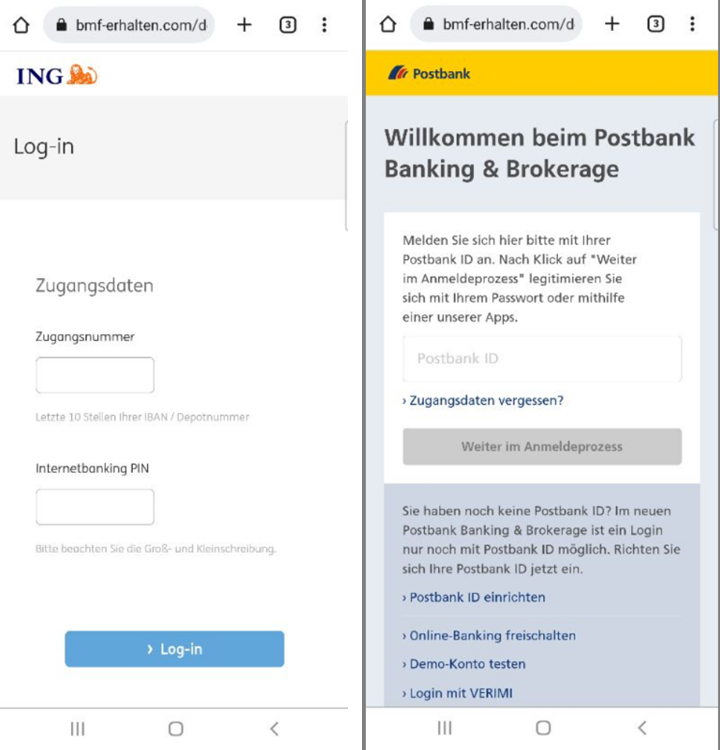
URL Examples:
• hxxps://bmf-unterschreiben.com
• bmf-ruckerstattung.com
• hxxps://de-zufugen.biz
• hxxps://bmf-ruckerstattung.info
• hxxps://de-einnahmen.biz
• hxxps://entschadigun-bmf.com
• hxxps://bmf-online-bewerbung.link
• hxxps://erstatungsantrag-bmf.online
• hxxps://bmf-erhalten.com
• hxxps://bmf-erinnerung.com
French Health Insurance Scam
Malware is not the only threat in France. An active phishing campaign mimics the Social Security Website, asking users for personal data to receive reimbursement or to renew their expiring insurance. Authorities have already issued a warning to users and given them examples of malicious SMS messages.
URL Examples:
• hxxps://ameliservice[.]net
• urlz[.]fr/jqEZ
• etape-ameli[.]fr
• masante-espace[.]com
• expedition-ameli[.]fr
• cut[.]ly/rBOgP1Y
• cut[.]ly/4NRN2Ze
• ameli-infoservice[.]fr
• espace-sante-publique[.]fr
• hxxps://ameli-maladie[.]info
• hxxps://amelifrance[.]site/ameli
• ameli-cpamclient[.]fr
• hxxp://ameli-secure-log[.]com
• hxxps://fr-droits-ameli[.]com
• cut[.]ly/iBnc6Fj
• hxxps://serviceameli[.]info
• hxxps://renouvellementcartevital[.]fr
• hxxps://amelisante[.]org
• hxxp://assurance-client[.]info
• hxxps://ma-cartevitalerenouvellement[.]fr
• assistance-mon-compte.awxcrt[.]com
• hxxps://amelifrance[.]info/ameli[.]php
• hxxp://secu-ameli[.]app
• vitalerenouvellementgv[.]com
• ass-vitale-gv[.]com
• ligne-ameli[.]com
• hxxp://moncompte-sante[.]info
• hxxps://renouvellement-en-ligne[.]fr
• hxxps://assurance-renouvellement-carte[.]fr/login[.]php
• cpam-recouvrement-vital[.]info
• hxxp://assurer-ameli[.]com
• hxxps://ameli[.]fr-renouvellements[.]com
• hxxp://acces-carte-vital[.]info
• redirectionclientsvitale[.]com
• ameli-renouv-espace[.]fr
• hxxp://assures-ameli[.]app
• assurance-maladies-gouv[.]com
• rubrique-clientsvitale[.]com
• sante-carte[.]com
• amelicartevitale2022[.]com
• hxxps://ameli-maladie[.]eu
• hxxps://renouv-assurance-maladie[.]fr
• espaceclient-ameli[.]fr
• service-client-information[.]com
• hxxps://renouvellements-carte[.]fr
UK Covid SMS
Despite reduced interest in Covid-related news, scammers continue to use the pandemic in phishing attempts. Users are tricked into thinking they will receive a free Covid-19 test kit if they just pay a small amount for delivery or are told that they have been in contact with an infected person and can take a free test. The real website is nhs.uk, whereas the links in the SMS messages lead to look-a-like pages. The NHS has issued warnings on its Twitter page about these ongoing scams.
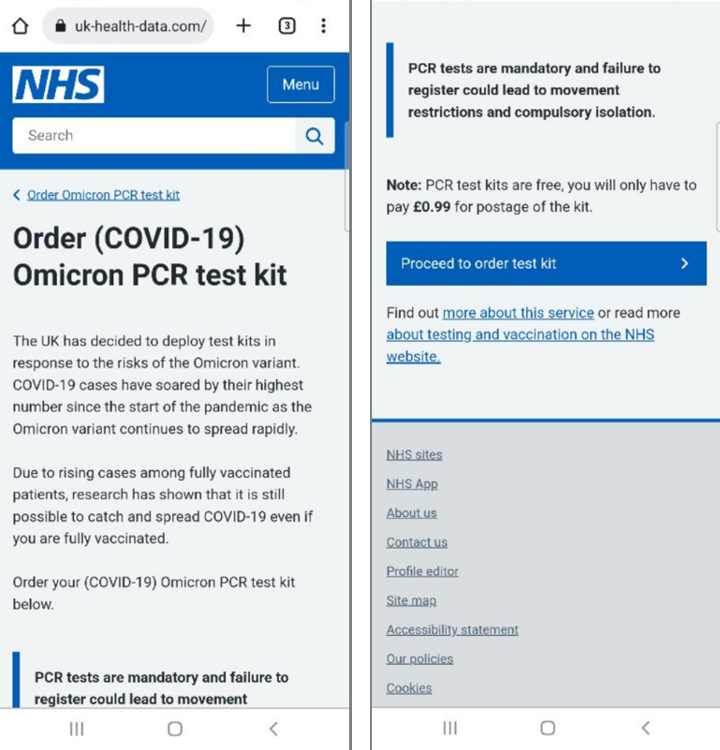
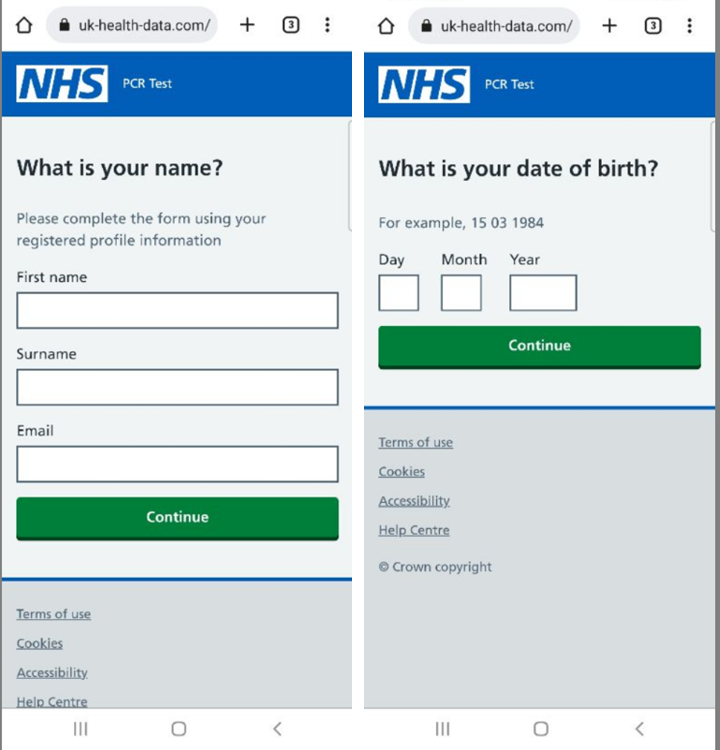
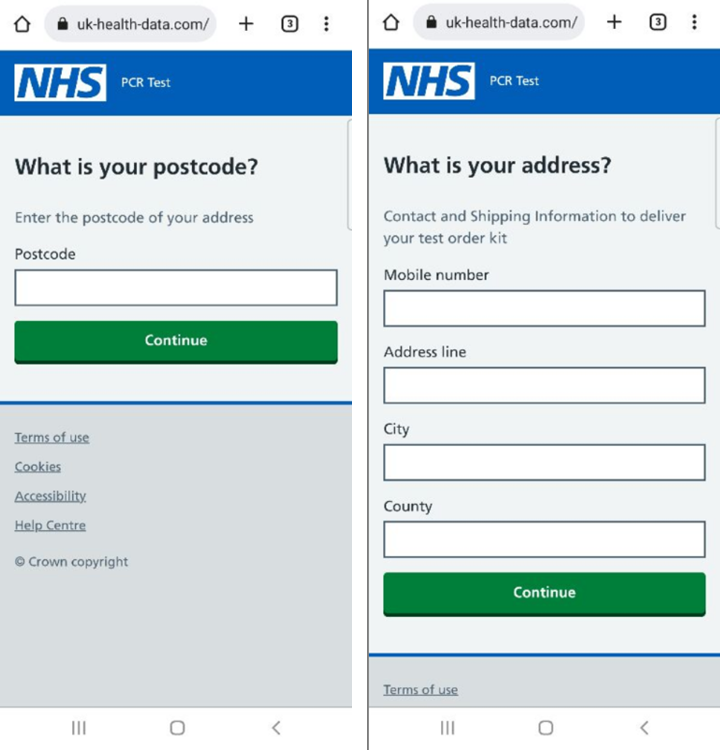
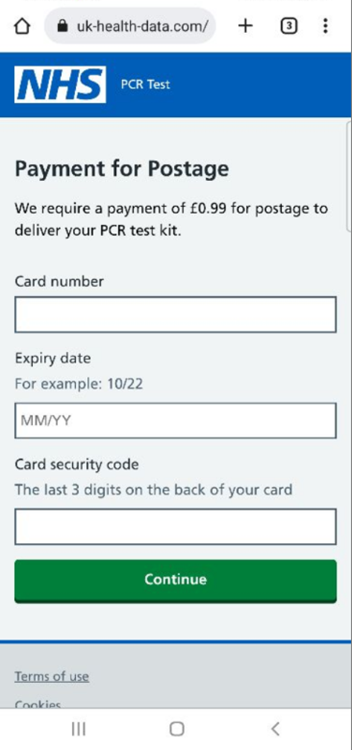
URL Examples:
• hxxps://uk-health-data[.]com
• hxxps://national-health-service[.]com
• hxxps://testkit-requestuk[.]com
• hxxps://nhs-pcrtestkit-orders[.]com
France Air Pollution Certificate Scam
A Crit'Air sticker (air quality certificate) is mandatory when driving through low-emissions zones in France. Drivers can be tricked into giving their data to scam websites through links received via SMS if they don't pay attention. The official website states, "You can be sure that you are on the official site if the ministry's logo is displayed and the site address ends in .gouv[.]fr."
URL Examples:
• hxxps://critair-france[.]org
• hxxps://critair-commande[.]org
• hxxps://critair-france[.]com
• hxxps://gouv-service-air[.]fr
• hxxps://gouv-crit-air[.]com
• hxxps://critair-dispositif[.]fr
• critairpourtous[.]com
• critairpourtous[.]info
• hxxps://critair-vignette-auto[.]fr
• hxxp://crit-airattestaion[.]fr
Spain Tax Agency Phishing
Spanish users have received text messages, purportedly from the Tax Agency, that claim they are eligible for tax reimbursement. A list of current phishing attempts involving the Tax Agency has been posted on its official website.
The phishing website displays the logo of the Tax Agency and states that the user is eligible for a €461 tax reimbursement. The links below in the blue box lead to the exact page where the user inputs their data.
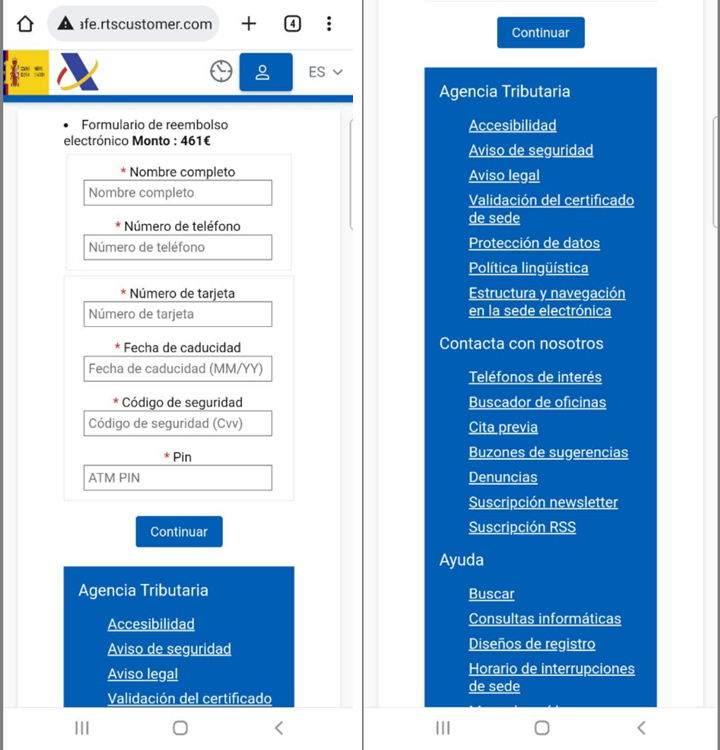
URL Examples:
• hxxps://tributariaagenciaweb.page[.]link/es
• hxxps://agenciaatributaria.page[.]link/es
• hxxps://tributariaagenciaa.page[.]link/es
• cutt[.]ly/3Bpihla
• hxxps://s[.]id/es-tributar
• hxxps://s[.]id/Es-tributar
• hxxps://v[.]ht/es-tributaria
• hxxps://3c5[.]com/ndrwj
• hxxps://agenciatributariainfoweb.page[.]link/esp
• hxxps://s[.]id/ES_tributaria
Australian Toll Road Scams
Drivers in Australia have been receiving messages claiming they've missed a deadline to pay toll road fees or that their account has been banned. The toll road authority has posted warnings of a series of ongoing scams.
Even though the page resembles the official one, when checking the links below, we can see that they do not point anywhere.
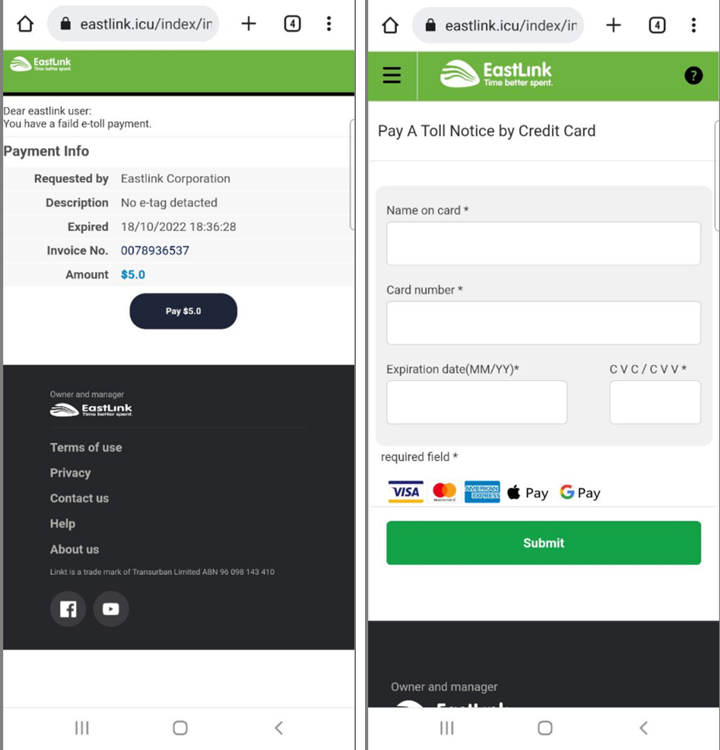
URL Examples:
• hxxps://au-linktin[.]com
• hxxp://betobes[.]com
• hxxps://shoplinkti[.]com
• hxxps://eastlint-my[.]com
• hxxps://au.psus[.]link
• hxxps://linkuserlong[.]link
• hxxps://au.tollts[.]link
Bank Scams
BNP Paribas Phishing in France
URL Examples:
• hxxps://bnpparibas-cle-digitale[.]com/?id=1
• cledigitale-bnp-paribas[.]fr
• service-cledigitale-bnpparibas[.]fr
• hxxps://bnp-support[.]fr
• mon-compte-bnpparibas[.]fr
Spain Banks Scam
The official site of BBVA sent a warning last year, but scams are still ongoing. The messages are entangled with the official messages that the bank sends to customers, making them very hard to detect.
Banks targeted with this scam:
• BBVA
• Imagin
• Kutxa Bank
• Unicaja Banco
• Santander
• Verse
• LaboralKutxa
• Evo Banco
• WiZink
• ING
• GrupaCaja Rural
• iberCaja
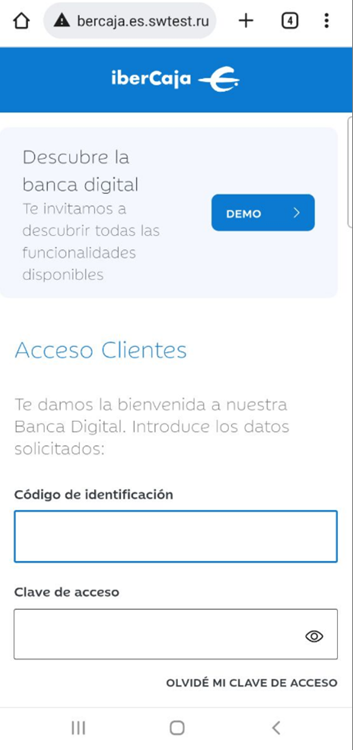
URL Examples:
• hxxp://imagin.incio-es[.]org
• hxxps://inicio.kutxa-app[.]com
• hxxps://unicaja.univia-lnicio[.]com
• hxxps://santander.logln-clientes[.]co
• hxxps://bbva[.]info-usuario-es[.]com
• hxxps://verse.incios-es[.]org
• hxxps://lkweb.movil-inicio[.]co
• hxxps://santander.firstotp[.]com/clientes/25-oct
• hxxps://seguridad-un.icaja-oniine[.]co
• hxxps://es.bbva-inicio[.]co
• hxxps://www.evobanco-inicio[.]co
• hxxps://unicaja[.]es-clientes-info[.]com
• hxxps://es.wizink[.]co
• hxxps://ing.direct-app[.]co
• hxxps://euro.cajarural-app[.]com
• hxxps://es.lbercaja-app[.]com
• hxxps://es.wizink-lnicio[.]com
• hxxps://unicaja.univia-login[.]co
• hxxps://bbva[.]es-info-usuario[.]com
• hxxps://t[.]co/bW5mtDwGcW
• hxxp://ibercaja[.]es.swtest.ru/18.11
• hxxps://kutxabank[.]es-soporte-net[.]com
Italy Bank Scams
URL Examples:
• hxxps://revisioneclientionline[.]com
• hxxps://localizza-bper[.]com
• hxxps://controllabper[.]com
• hxxps://s[.]id/VerificaClientiBCC
• hxxps://is[.]gd/ClientiBperAssistenza
• hxxps://is[.]gd/AccediBperOra
• hxxps://assistenzadispositivoconto[.]com
• hxxps://localizza-accessoweb[.]com
• hxxps://portale-restrizione-bper[.]com
• hxxps://cutt[.]ly/BperLogin
Canada Royal Bank Scam
URL Examples:
• hxxps://rbroyalsalert[.]com
• hxxps://rbroyalalert[.]com
• hxxps://rbroyal-alerts[.]com
• hxxps://rbroyal-alert[.]com
• hxxps://rbroyalsalerts[.]com
• hxxps://securerbcroyalalerts[.]com
• hxxps://securerbcroyalalert[.]com
• hxxps://rbroyalalert[.]com/@
• hxxps://securerbroyals[.]com
• hxxps://secureroyals[.]com
Germany scams
URL Examples:
• hxxps://meine.bestsing.net
• hxxps://dkb.services/de
• hxxps://postbank.m-eine.de
• hxxps://meine-postbank[.]info
• hxxps://dkb.services/mein
• hxxps://postbank.de.ihre-de[.]com
Locked User Accounts
Apple Pay Scam in the UK
Of course, phishing isn't the only threat circulating via SMS in the UK. Also common are scams focused on Apple Pay accounts, trying to trick users into giving out their personal information to log back in.
URL Examples:
• re-enable-appleid-online[.]com
• applepay-wallet-secure[.]com
• apple-recover-wallet[.]com
• apple-pay-activate[.]com
• restore-appleid-online[.]com
• hxxps://reactivate-my-wallet-id[.]com
• renew-apwallet-id[.]com
Amazon Scam in the UK
A scam focused on deactivated Amazon accounts, where users are tricked into giving out personal information to log back in, is very similar to the PayPal version.
URL Examples:
• hxxps://review-amazon-account[.]com
• hxxp://verify-my-accounts[.]com
• hxxps://review-amazonaccount[.]com
• hxxps://secure-amazon-account[.]com
• hxxps://amazon-activity-checker[.]com
• hxxp://review-account-amazon[.]com
• hxxp://my-amazon-login-review[.]com
Netflix Refund Scam in US
The scammers behind the messages use the allure of a refund to entice people into clicking on the link to the malicious website — where they could be tricked into entering their personal and financial information. Any information entered into the site will be available to scammers.URL Example:
URL Example:
• claimrefund[.]info
Netflix Scam in France
A similar scam is circulating in France, with criminals trying to persuade victims to re-enter their credit card details under the threat of deactivating their Netflix account.
URL Examples:
• activation-abonnement-netflix[.]com
• hxxps://netflix.portail-connexion[.]com
• hxxps://netflixfacturationsms[.]com
• hxxps://netfiix-aideclient[.]fr
• hxxps://netflix-espaceclient[.]com
• login.nelfiix[.]com
• netflixcompteclient[.]com
• netflixcompteclients[.]com
• hxxp://netflix-forfait[.]fr
• hxxps://netflix[.]infos-help[.]com
• netfiix-securefrdoc[.]com
• netfiix-help[.]com
• netflix[.]com-connexion[.]com
• netflixinfomation[.]com
• activation-abonnement-netflix[.]com
• hxxps://netflix.portail-connexion[.]com
• hxxps://netflixfacturationsms[.]com
• hxxps://netfiix-aideclient[.]fr
• hxxps://netflix-espaceclient[.]com
• login.nelfiix[.]com
• netflixcompteclient[.]com
• netflixcompteclients[.]com
• hxxp://netflix-forfait[.]fr
• hxxps://netflix[.]infos-help[.]com
• netfiix-securefrdoc[.]com
• netfiix-help[.]com
• netflix[.]com-connexion[.]com
• netflixinfomation[.]com
• hxxps://changementinfo[.]com
• hxxps://help-compte[.]click
• facturenetflix[.]com
• hxxps://client-facture[.]com
• hxxps://info-fr[.]click
• hxxps://netflix-paiement[.]com
• hxxps://netfiix.reactivation-espaces[.]fr
• hxxps://netfiix[.]espace-activations[.]fr
• hxxps://netfiix.activation-service[.]fr
• netflix.redirections-service[.]fr
• identifiant-membre[.]com
• services-membres[.]com
Fake Package Tracking Campaigns
Roaming Manties targeting France
While many phishing campaigns try to redirect people to fake websites that collect private information, criminals sometimes redirect people to malware. In this campaign, which started in Asia but reached Europe this year, the malware is called Roaming Manties.
Roaming Manties was observed in France in July this year and is still targeting French users. The attack is widespread, having been received over 90,000 times since September by users with Scam Alert.
Unlike the UK and Germany, most messages carrying these links mention package delivery issues or notifications.
URL Examples:
• hxxp://cdmkn.czpua[.]com
• hxxp://yrqhz.pdtdg[.]com
• hxxp://hiixh.etqph[.]com
• hxxp://rpsqb.xmgtr[.]com
• hxxp://rocnt.tqhvo[.]com
• hxxp://tusnl.czpua[.]com
• hxxp://mijdx.czpua[.]com
• hxxp://lwsik.etqph[.]com
EMAG/Altex scam in Romania
Romania is also an active target for phishing and similar threats. Fraudsters use the likeness of a couple of well-known online marketplaces to trick people. Users receive a personalized message about a prize they received that must claim, containing their name and phone number.
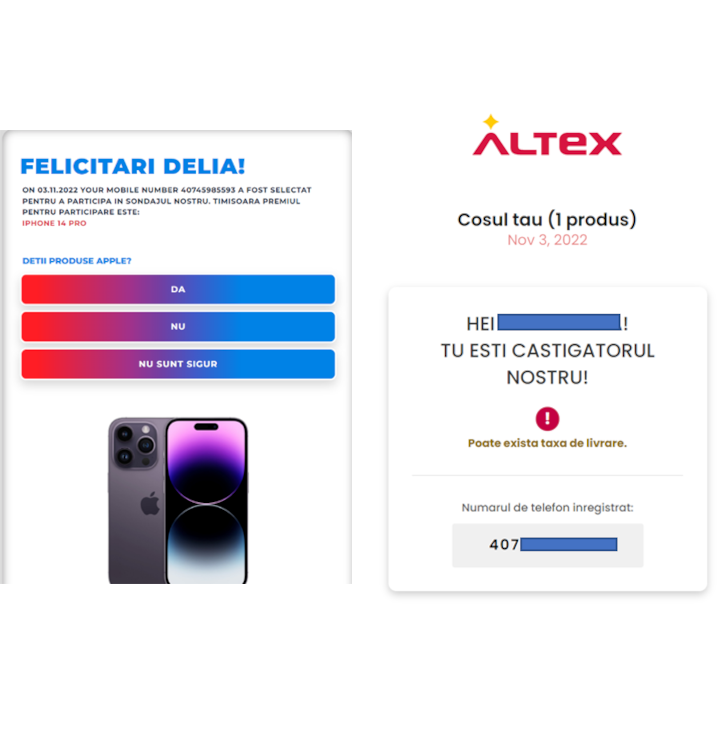
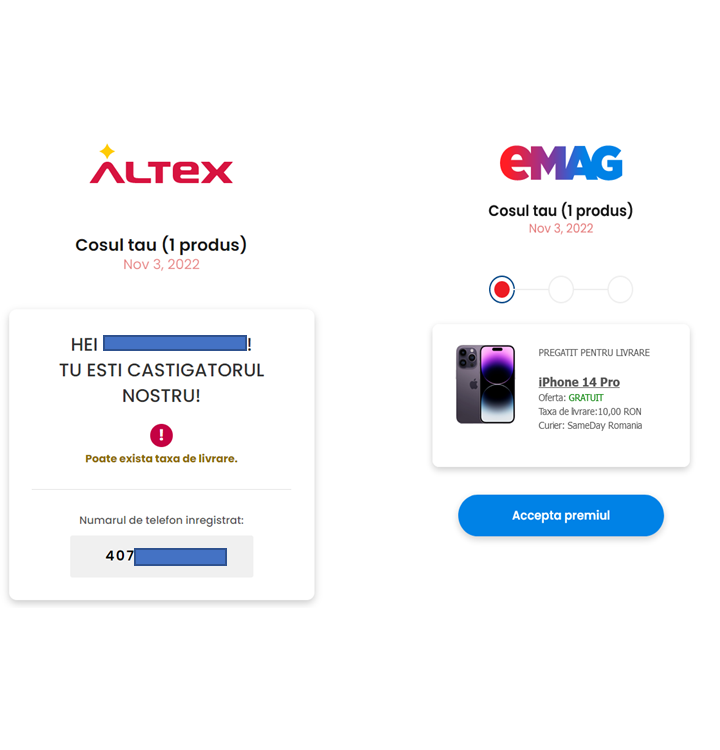
If the user accepts the prize, he is asked to choose the delivery option:

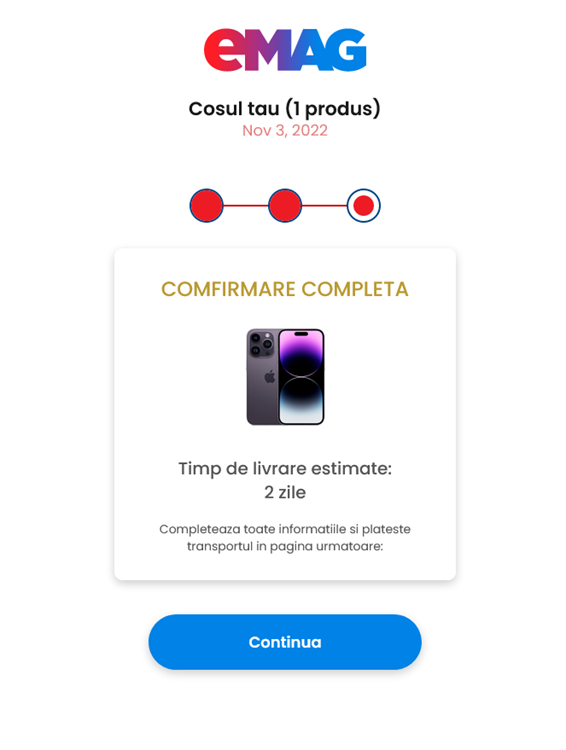
To complete the transaction, the victim has to fill in the address and offer other personal information.
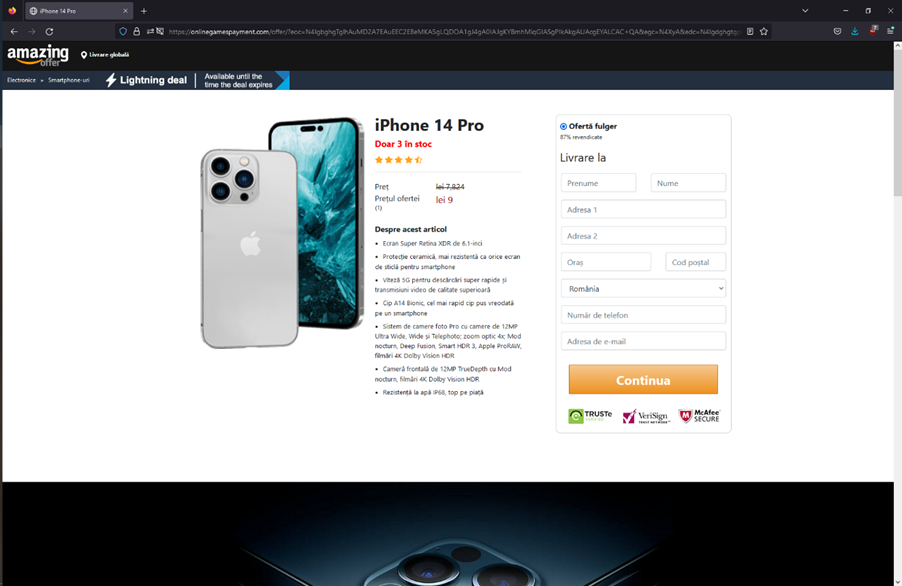
Finally, the user is asked for credit card information:
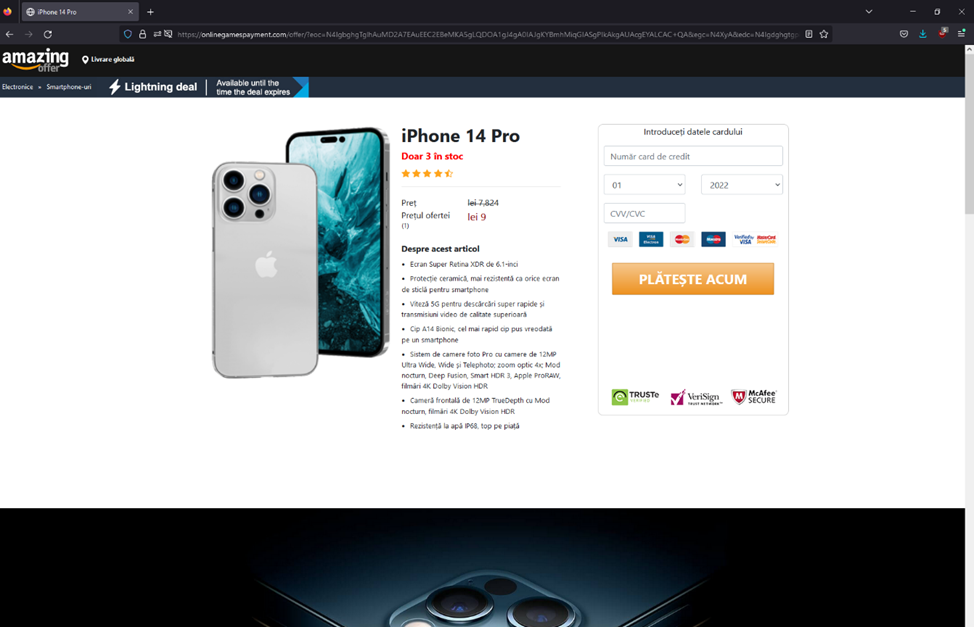
URL Examples:
• awuyoc[.]com/dFPjeO8
• utojamo[.]com/fOz6LNy
• uluwuy[.]com/olAJaUj
• ixunace[.]com/Gach9ki
• ajayuho[.]com/I2FidS4
• otohaza[.]com/Y8EDZ0r
• omiyuna[.]com/KGZI5hM
• ucufob[.]com/UnAIgbU
• ulefiv[.]com/AgKk6Xd
• onawan[.]com/QShrJ7j
• eyupono[.]com/uoNBoQa
• awelumi[.]com/upMSPUz
Phishing schemes in Italy and other countries
This fraud seems to be from the same group behind the Altex/Emag attack in Romania.
Fake GLS website:

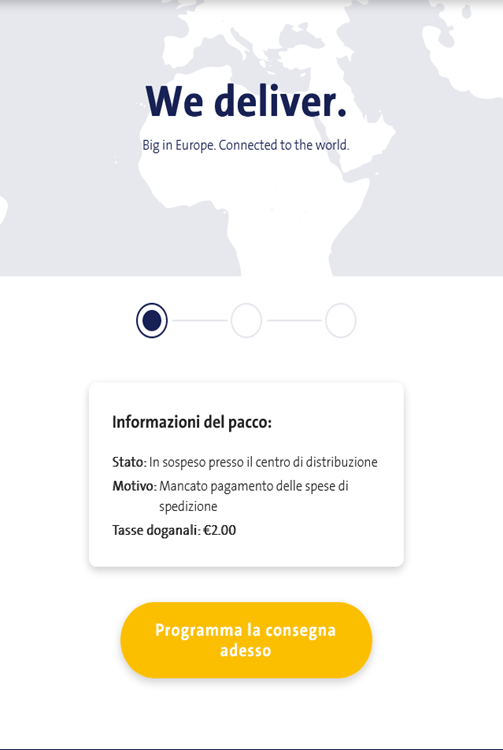
Information about a package delivery:

User must pay 2 euro delivery tax:
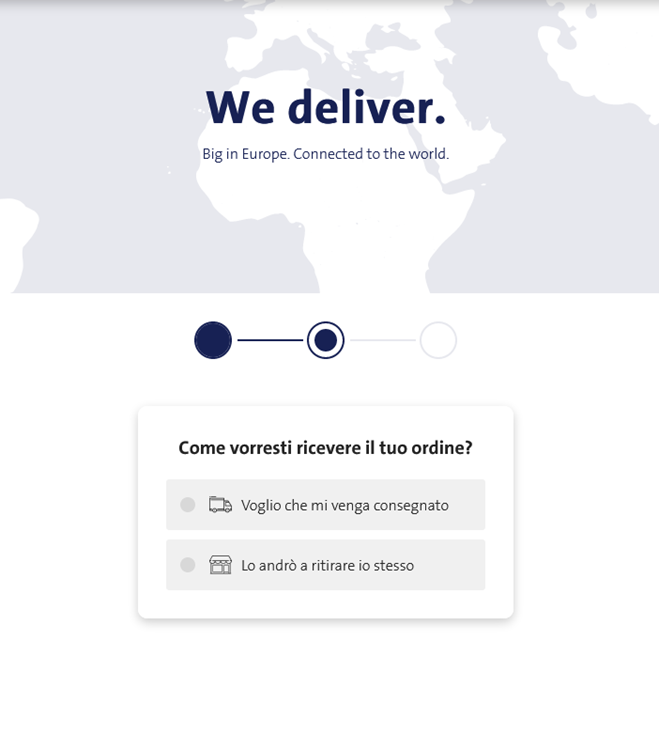
User can choose to receive the package at home or to pick it up:
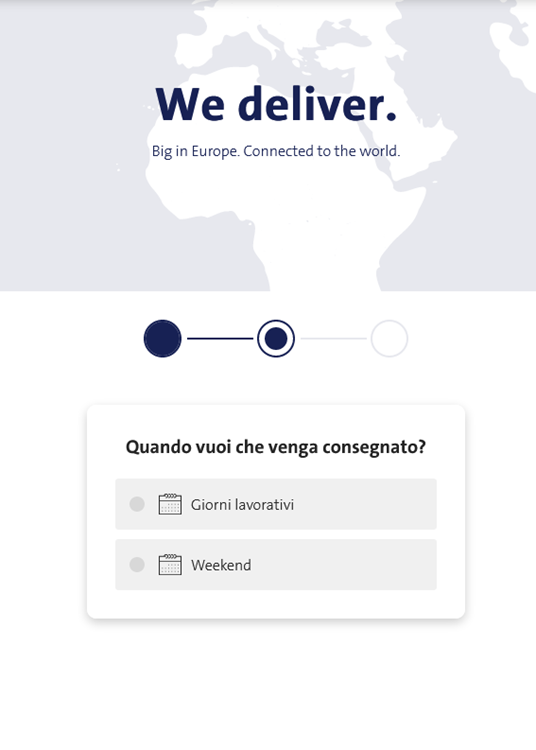
Delivery on the weekend or during work days:
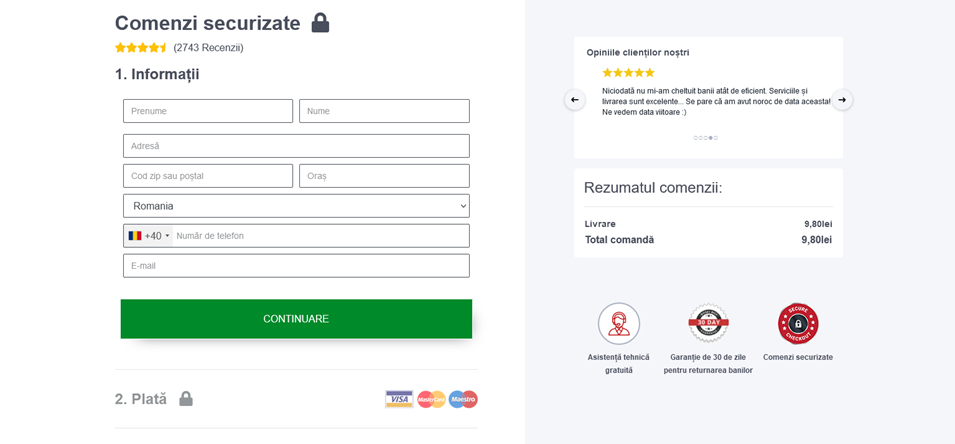
Last step, address and payment information:
Fake Delivery Mexico
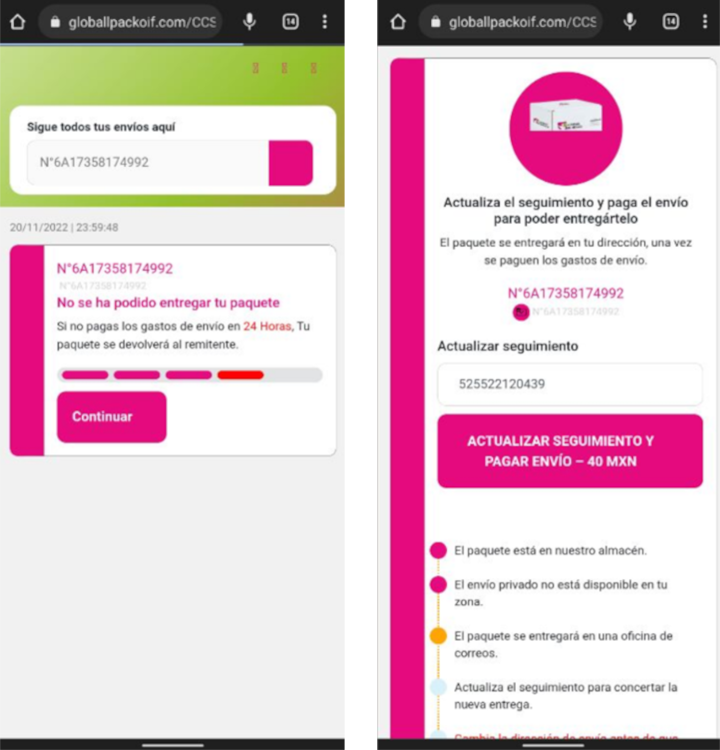
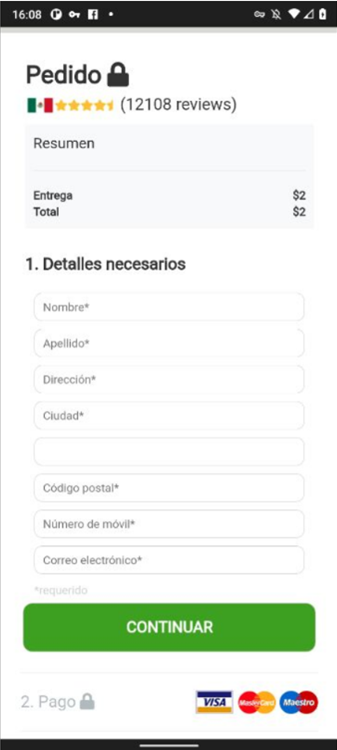
URL Examples:
• ebomoc[.]com/QEYFk7e
• atejobi[.]com/XxZu1F7
• ucezok[.]com/6KFbhQJ
• bxvr[.]me/9QdBAn
• ojupele[.]com/lIRF7lk
Fake Prizes Scam in South Africa
The promise of great prizes is an obvious tactic, but these phishing websites only work with a VPN, from South Africa. If the websites are accessed from another region, they redirect to Google.
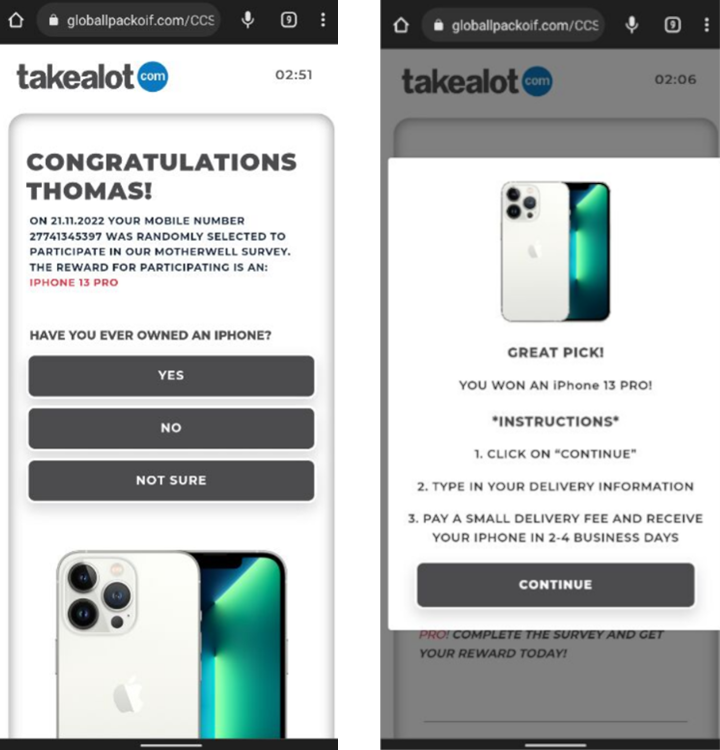
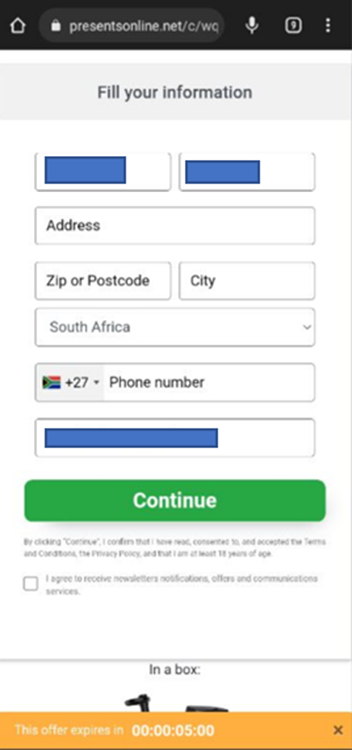
URL Examples:
• usehopi[.]com/Yea2m7S
• ekulaye[.]com/vDWx1FI
• ivifex[.]com/zbKZ08G
• uzokoc[.]com/4r2m21E
• izedup[.]com/CsD1YDg
Fake Prizes Scam in Poland
A similar campaign takes place in Poland. The same rule applies; it's only available from a Polish IP via VPN.
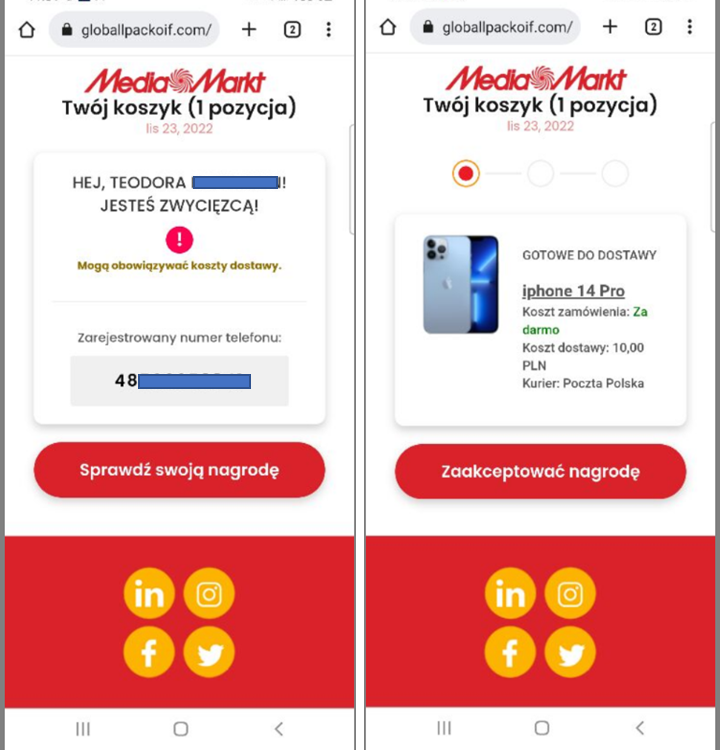
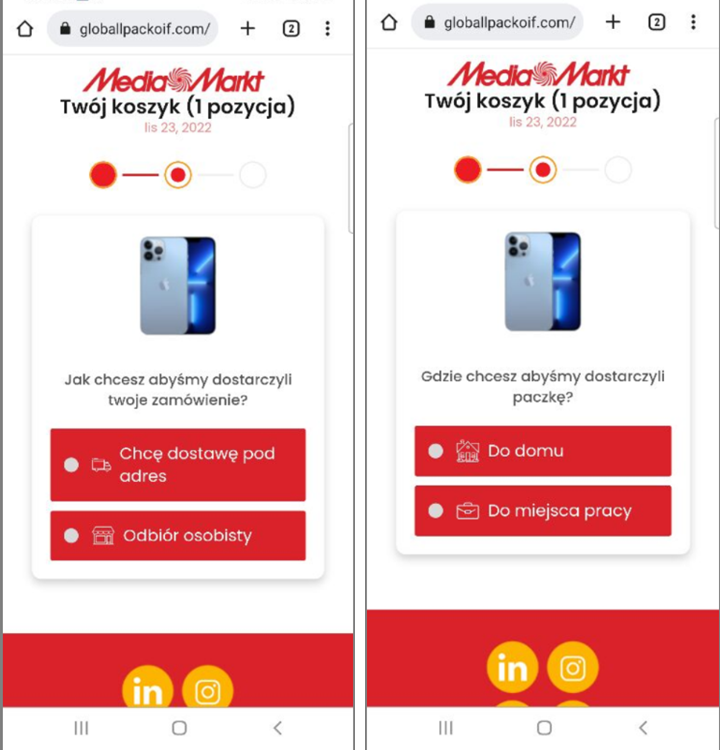
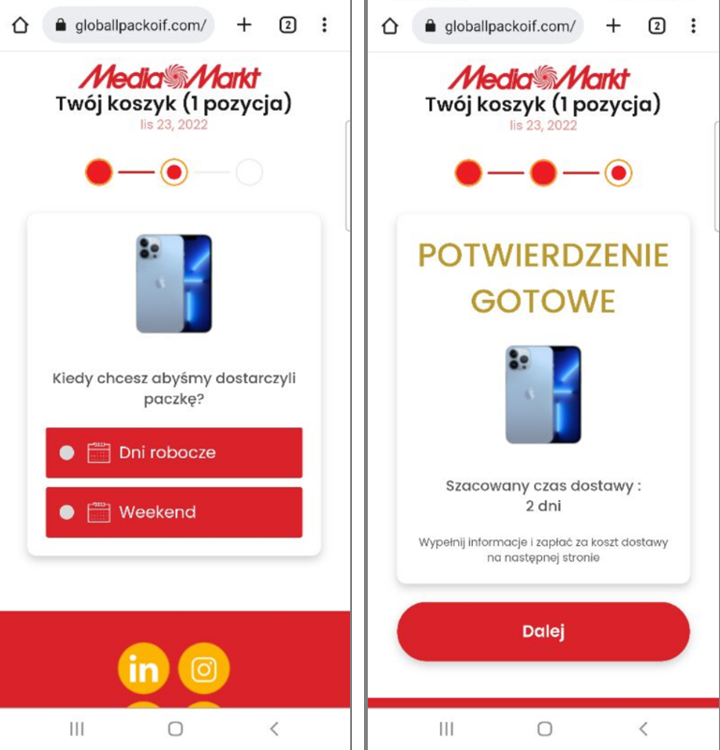
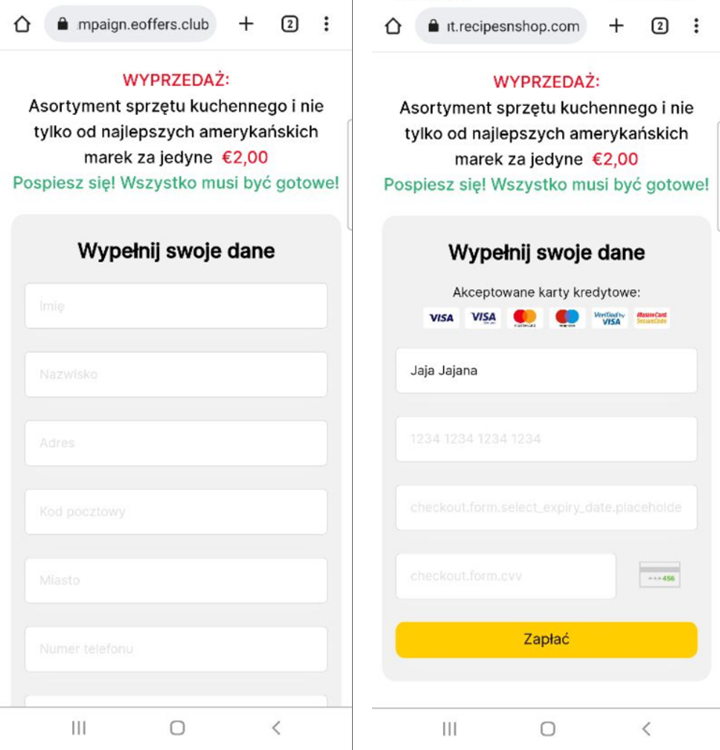
URL Examples:
• hxxps://ikowog[.]com/xQC5uih
• hxxps://oseyid[.]com/FuXBQQM
• hxxps://iwakute[.]com/TaDYiMK
• hxxps://exereni[.]com/xUxnjh9
• hxxps://epuzec[.]com/vCqQt41
A few of the phishing websites work without VPN.
Package Tracking Phishing in Spain
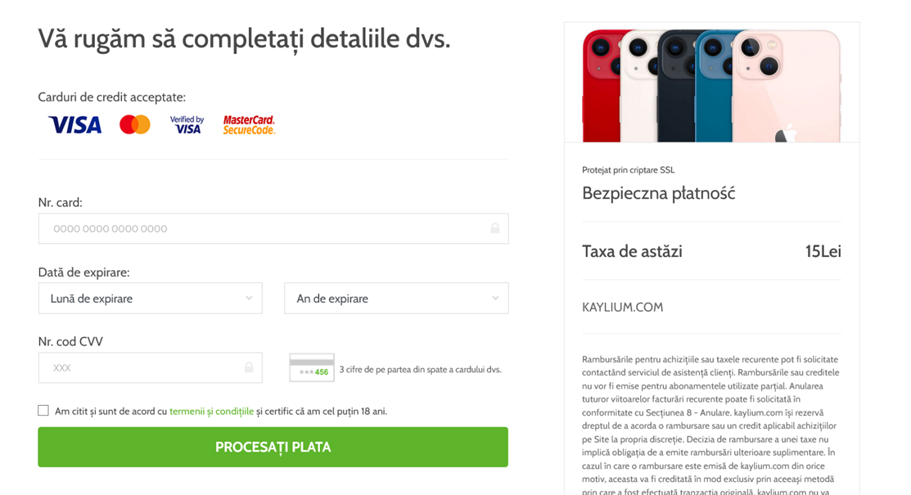
In this phishing scheme, criminals ask users to pay a delivery fee to receive a package and give out their credit card information. The phishing website also offers the option to download an app that takes you to the official Google Play Store.
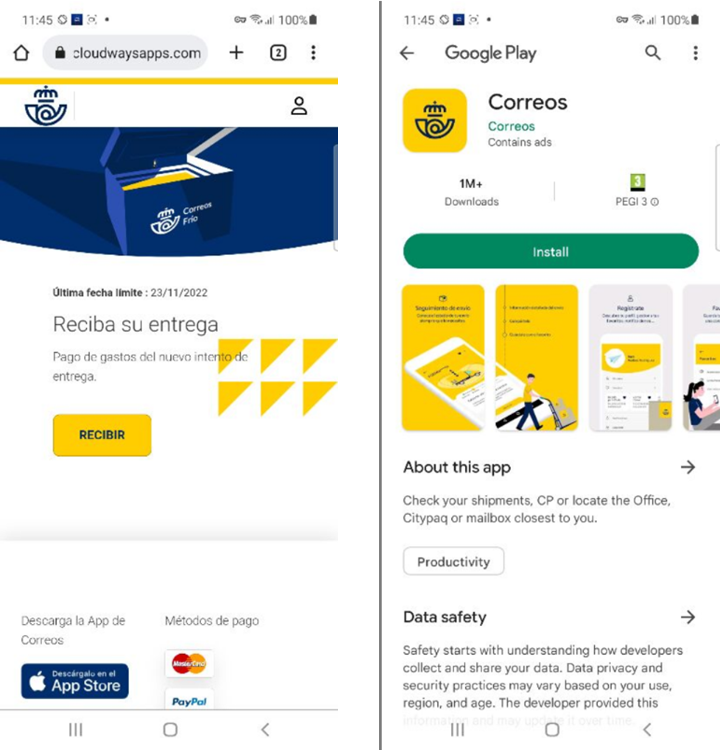
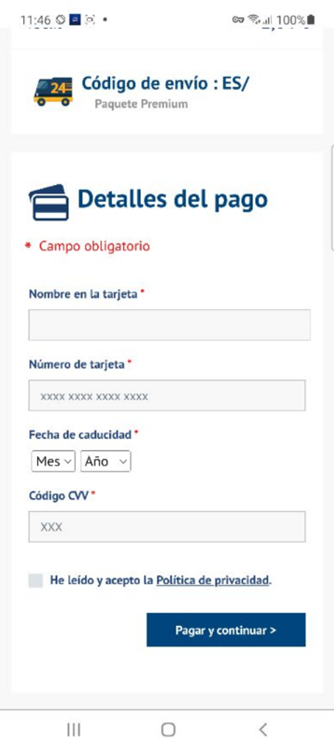
URL Examples:
• hxxps://s[.]id/eS-C0rreos
• hxxps://itsssl[.]com/I1jba
• paqcorreos[.]es
• hxxps://short[.]gy/BNsRmS
• hxxps://byrl[.]me/EquipoCorreos3
• hxxps://byrl[.]me/eu-espagos
• hxxps://byrl[.]me/ymmSRF6
• hxxps://correospaqueta.page[.]link/es
• hxxps://3c5[.]com/4h04i
• hxxps://u.to/2KJVHA
• correosenviosl.squarespace[.]com
• hxxps://correos.page[.]link/correos-express
• hxxps://bitly[.]ws/vfJ4
• hxxps://correos-ch.app[.]link/payment
• hxxps://correos-ch.app[.]link/e/info
• hxxps://pxlme[.]me/FPQ_FfpA
• hxxps://pxlme[.]me/fndS5fd8
• hxxps://epk[.]is/L_NF0
• hxxps://short[.]gy/Ksrwzl
• hxxps://bit[.]do/Correospago
• hxxps://crrs-cargo651[.]es.swtest.ru/es
• hxxps://byrl[.]me/CorreosFrio2
• hxxps://byrl[.]me/Correos-PAGO2
• hxxps://byrl[.]me/y6rISkl
• hxxps://3c5[.]com/adhum
• hxxps://v[.]ht/qquTx
• hxxps://s[.]id/Grupo-Correos
• hxxps://crrs-cargo6473[.]es.swtest.ru/in
• hxxps://correospaquetas.page[.]link/es
• hxxps://coreuc-s-site.thinkific[.]com
• hxxps://correos-verificacion-es[.]com/express
• hxxps://bit[.]ly/3DM1bNE
• hxxps://crrs-cargo-64[.]es.swtest.ru/2
Similar campaigns around the world
Slovakia
URL Examples:
• hxxps://bit[.]do/PostaSlovenska-sk
• hxxps://bit[.]do/Slovensk-post
• tinyurl[.]com/2e4cmv9m
• hxxps://dhwor.page[.]link/pckageready
• hxxps://slovenska-s-site-45a4.thinkific[.]com
• hxxps://sloven-s-site.thinkific[.]com
UK
URL Examples
• hxxps://parcel-tracking-link[.]com
• hxxps://evri[.]id-40[.]com
• hxxps://myevri-tracking-confirmation[.]com
• hxxps://myevri-missed-delivery[.]com
Canada
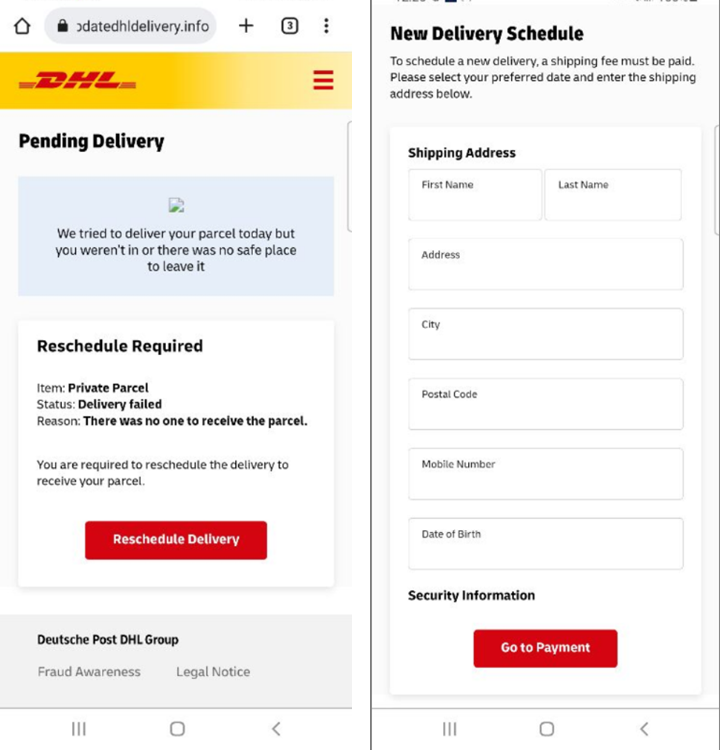
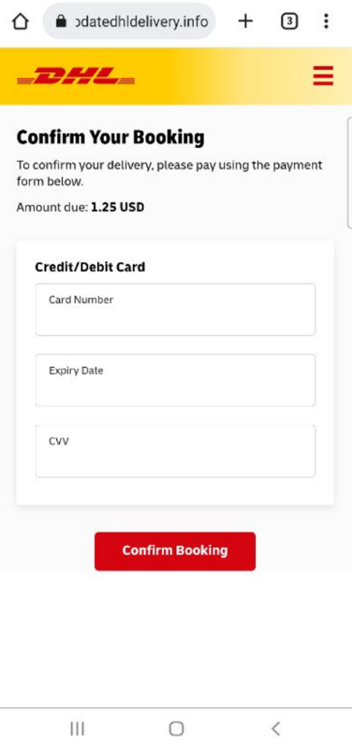
URL Examples:
• hxxps://dhltracking[.]ca/Scheduler
• hxxps://trackdhl[.]support/Scheduler
• hxxps://trackdhl[.]online/Scheduler
• hxxps://dhllogistics[.]ltd/scheduler
• hxxps://dhllogistics[.]delivery/scheuler
• hxxps://dhlparcelsexpress[.]com/Schedler
Romania postal scam
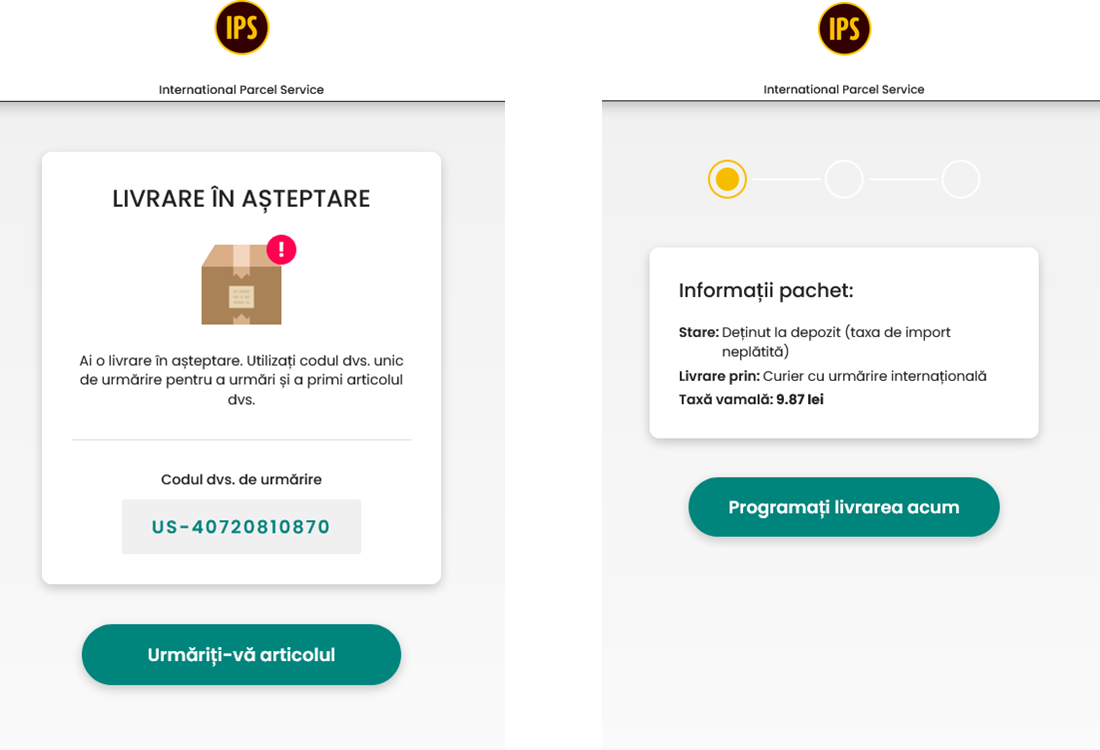
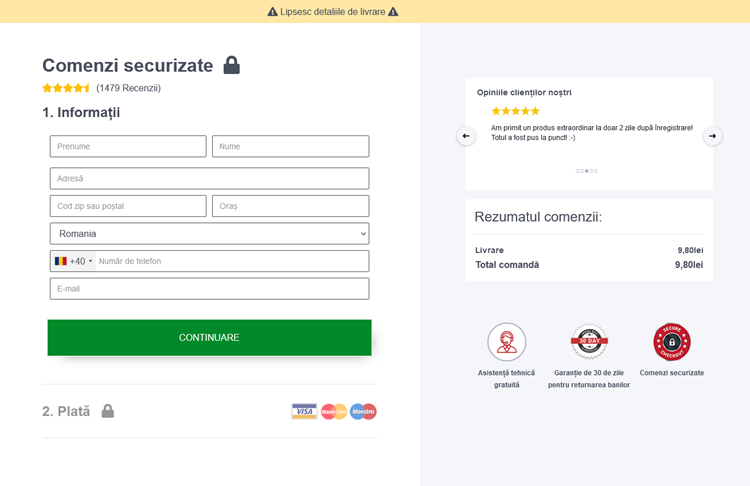
URL Examples:
• osociv[.]com/qjq9OQu
• aticow[.]com/w3No4uS
• otoxed[.]com/1zW6zzL
• isimuf[.]com/GJC3atD
US Packages
UPS scams are also widespread in the US and are very similar to the ones above.
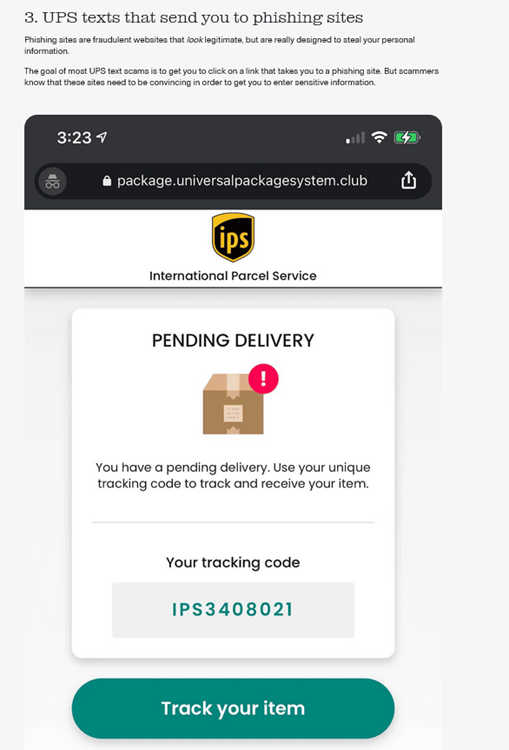
URL Examples:
• hxxps://www.us-ps[.]app
• uspotint[.]info/mktr
• hxxps://us-psovd[.]top
• bit[.]ly/3zE5AQn
• hxxps://us-psbdl[.]top
• hxxps://hvcga97-sp[.]com
• hxxps://us-psble[.]info
• usparonces[.]info/SR4W
• hxxps://usp-sckvz[.]cc
• hxxps://us-psgoc[.]info
• www.ups-nb9k3[.]us
• exrderbx[.]info/SP3U
• hxxps://us-pstxkn[.]top
• usptrcfes[.]info/FAQs
• hxxps://rebrand[.]ly/2utgcsg
• hxxps://us-psguv[.]top
• hxxps://us-pslbw[.]top
• hxxps://us-jkusp[.]com
• hxxps://us-psglz[.]top
• hxxps://us-psvkw[.]top
Singapore Post scam
The official Singapore postal service website has already issued a warning. SMS notifications are being replaced with push notifications from the official app.
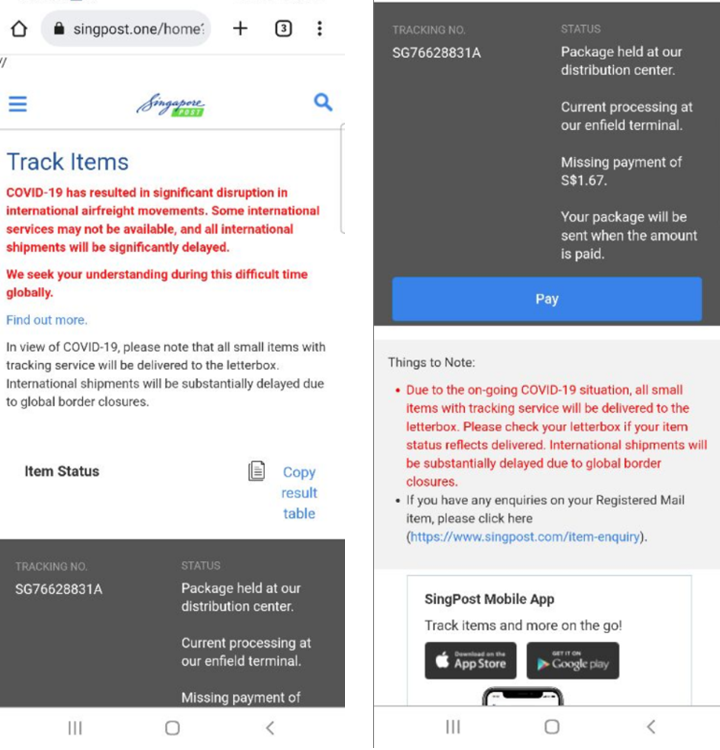
URL Examples:
• www.singposty[.]com
• hxxps://rb[.]gy/ytsbzs
• hxxps://rb[.]gy/oy5xan
• www.singpostin[.]com
• hxxps://sgpostnl[.]com
• www.sgapi.adse-elec[.]com
• www.postal.fnbrrd[.]com
• hxxps://singss[.]top
• hxxps://s[.]id/1oxeU
• hxxps://s[.]id/1oxGc
• www.sgpost[.]gddtd[.]com
• www.singlpost[.]com
• www.sgpostl[.]com
• www.sgpost.magichz[.]com
We find more examples in Australia and France
URL Examples:
• hxxps://id-4554portal[.]com
• hxxps://auspost.reschedule-consigment-online[.]com
• hxxps://auspost[.]consignmentsinfo[.]com
• hxxps://aus-postredelivery[.]com/2/AUSPOST_2023
• hxxps://courier-ref7638[.]com
• hxxps://courier-ref5674[.]com
• hxxps://auspost.requestconsignments[.]com
ChronoPost France
URL Examples:
• chronopostsupport[.]fr
• hxxps://acheminements-chronopost[.]fr
• chronopost-aide[.]info
• chronopostservice[.]fr
• hxxps://mon-suivi-chronopost[.]com/client
• chronopost-serviceclient[.]com
• chronopost-livraison-fr[.]com
• hxxps://interruption-chrono[.]com
• hxxps://suspension-colis[.]fr
• suivis-chronopost[.]fr
• livraison-acheminer[.]com
• colischronopost[.]com
• hxxps://chronopost[.]express
• chronopost-livraison-suivi[.]com
• hxxps://chronopost.suivi-informations[.]com
• chronopost.suivi-informations[.]com
• hxxps://helper-chronopost[.]com
• hxxps://csuivi-chronopost-colis[.]com
• hxxps://suivi-chronopost-colis-client[.]com
• bit[.]ly/3DJusIQ
• hxxps://chronopost-suividecommande[.]fr
tags
Author

I'm a Security Researcher at Bitdefender, and when I'm not looking at code, I spend my time enjoying a good book, traveling, and swimming.
View all posts
I'm a Junior Security Researcher at Bitdefender, and I usually spend my free time reading, playing the piano, solving chess puzzles, or learning a new language.
View all postsSilviu is a seasoned writer who's been following the technology world for more than two decades, covering topics ranging from software to hardware and everything in between.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks














