Real-Time Behavior-Based Detection on Android Reveals Dozens of Malicious Apps on Google Play Store

Note: all applications mentioned in this research have been taken down and are no longer accessible.
For the past few years, cyber-criminals have strengthened their efforts to have malicious applications listed on Google Play Store – the world's most trafficked Android app source. While the platform's security checks have improved through the years, our research still uncovers malicious apps that use a vast array of tricks to bypass these checks.
This is the case of a new malware campaign on the Google Play Store where numerous apps use false pretexts to lure victims into installing them, only to change their name and aggressively serve ads afterward.
Attack at a glance
- Bitdefender has identified 35 applications that have snuck into the Play Store, totaling over two million downloads if we consider the available public data.
- These apps hide their presence on the device by renaming themselves and changing their icon, then start serving aggressive ads
- To confuse the user and conceal their presence, the applications are changing their name and icon after installation
One of the ways cyber-criminals monetize their presence on Google Play is to serve ads to their victims. While this may sound diminutive, these ads served to victims are disrupting the usage experience and can link directly to malware.
Many legitimate apps offer ads to their users, but these ones show ads through their own framework, which means they can also serve other types of malware to their victims. Most of the time, users can choose to delete the application if they don't like it. But these new malicious apps trick victims into installing them, only to change their name and icons and even take some extra steps to conceal their presence on the device. Users can still delete them at will, but the developers make it more difficult to find them on the affected devices.
While all of the detected apps are clearly malicious, the developers were able to upload them to the Google Play Store, offer them to users and even push updates that made the apps better at hiding on devices. Bitdefender identified the malicious apps using a new real-time behavioral technology designed to detect precisely these dangerous practices, among many others. This new technology is already producing results as new detections are instantly shared with all Bitdefender Mobile Security users.
We looked at the 'GPS Location Maps' app as the first example. With over 100k downloads, it's one of the more popular, but we noticed it doesn't have any reviews. Immediately after installation, the app changes its label from 'GPS Location Maps' to 'Settings' and then shows additional websites in WebViews and an advertisement.
WebViews is part of the Android operating system that allows apps to load content like web pages, ads, and more.
The 'GPS Locations Maps' app makes it difficult for users to find and uninstall it by changing its icon. Also, on some devices, a few malicious apps even request permission to bypass the battery optimization feature and start foreground services notifications to stay alive and not get killed by the system.
Many of the detected apps also request permission to display over other apps, which means that they are likely also simulating user clicks to rake on profits.
Code Obfuscation Used to Remain Hidden
The developers who created the 'GPS Location Maps' added heavy code obfuscation and encryption in order to make reverse engineering difficult. The main Java malicious payload hides inside two encrypted DEX files, and the decryption occurs inside obfuscated native code. Even after decryption, the resulting Java code strings remain obfuscated.
Malicious behavior like changing the icon also happens in a different native 'so' file than the one used for decryption and remains obfuscated.
Encrypted DEX files inside the assets of the application:

Obfuscated strings (base64 into XOR):

Native functions declared:
Hiding the Icon To Stay Covert
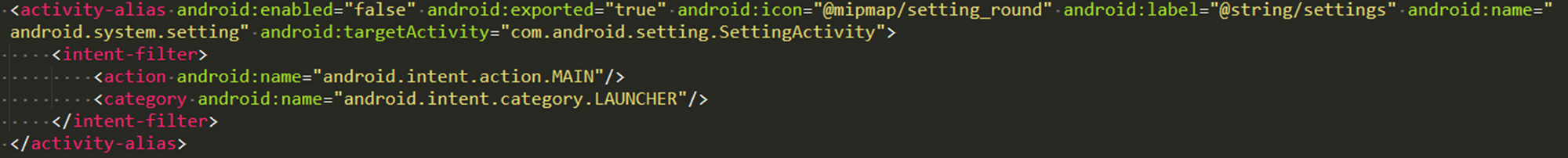
One way to stay hidden from a user bent on uninstalling the app is to change the icon into something innocuous, like the 'Settings' app. It does that by declaring an alias launcher. After installing another icon and label, it changes the main launcher, replacing it with the alias one with the label and icon for 'Settings.'
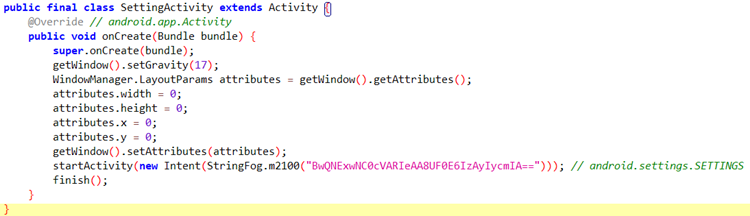
The alias launcher corresponds to another activity, hidden inside the `com.android.setting` package, probably to look more legit. When launched, this activity renders itself with '0' size in a corner, then launches the setting page for the phone, tricking the user into thinking that the real settings button was pressed.
Alias:
Fake settings activity:
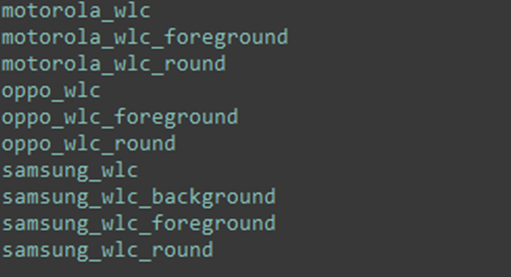
Some apps also contain different icon launchers for the settings app, depending on the device:
Hiding from recent apps
Another interesting technique developers use to obscure apps is to ensure they don't show in the list of the most recently used apps on Android. These apps also have the flag android:excludeFromRecents="true" set in their manifest, meaning that when a user looks at recent apps opened on the device, the adware app is not present among them.
'GPS Location Maps' is just one of the many that we have identified to manifest similar malicious behavior. We noticed that the initial versions of some of the detected apps didn't contain the "Settings" icons. The developers added the icons in subsequent app updates on the Play store.
When we look closer at the developers of the packed and obfuscated apps, a pattern emerges, showing a similar naming style. All the malicious app developers have just one application uploaded to the store. Also, the emails and websites related to the developers look similar to each other, which likely leads us to believe that all of these apps are the work of a single group or even developer.
The malicious behavior doesn't trigger on all devices, as there are some checks embedded in the apps likely related to the device location, language or other factors.
|
Developer Name |
Email |
Website |
|
Qasim.Llc |
https://personalitycharginshow[.]xyz |
|
|
ALCANTARA.Lab |
https://smartqrscanner1[.]xyz |
|
|
Baig.Corp |
https://animatesstickermaster[.]xyz |
|
|
Hamid.Apps |
https://gps1ocationfinder[.]xyz |
|
|
Emmanuel.Llc |
https://mygps123123[.]xyz |
|
|
Jamie.Lab |
https://artgirlswallpaperhd[.]xyz |
|
|
Bennington.Llc |
https://catsimulator1[.]xyz |
|
|
Josh.Lnc |
http://smartwifii123[.]xyz |
|
|
Vern.Apps |
https://imagewarpcamera[.]xyz |
|
|
VILORIA.Corp |
https://smartqrcreator1[.]xyz |
|
|
Abid.Studio |
https://colorizeoldphoto[.]xyz |
|
|
Adeel.Studio |
https://smartaps1ocation[.]xyz |
|
|
Haq.Corp |
https://secrethoroscope1[.]xyz |
|
|
Nadeem.Apps |
https://volumecontroll[.]xyz |
|
|
Cedrick.Corp |
https://gps1ocationmaps[.]xyz |
|
|
RICHARD.Lnc |
https://girlsartwallpaper[.]xyz |
|
|
Sushil.Dev |
https://mediavolumeslider[.]xyz |
|
|
Haider.Studio |
https://sleepsoundss[.]xyz |
|
|
Kumar.Apps |
https://qrcreatorr12[.]xyz |
|
|
Waseem.Llc |
https://secretastrology[.]xyz/ |
|
|
Butt.Corp |
https://colorizephotos[.]xyz/ |
|
|
Vledern Studio |
- |
Other Apps on Google Play With Similar Behavior
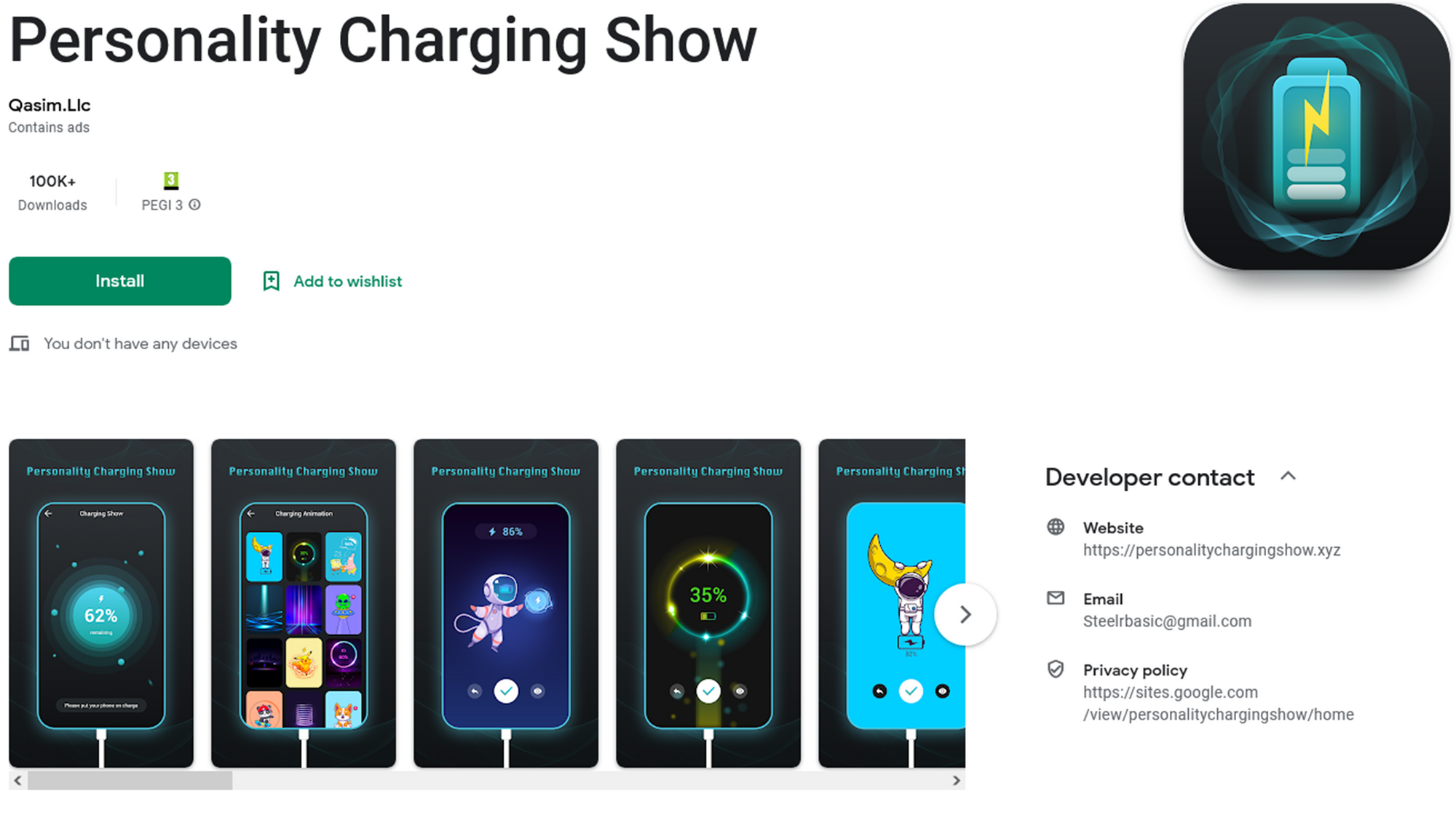
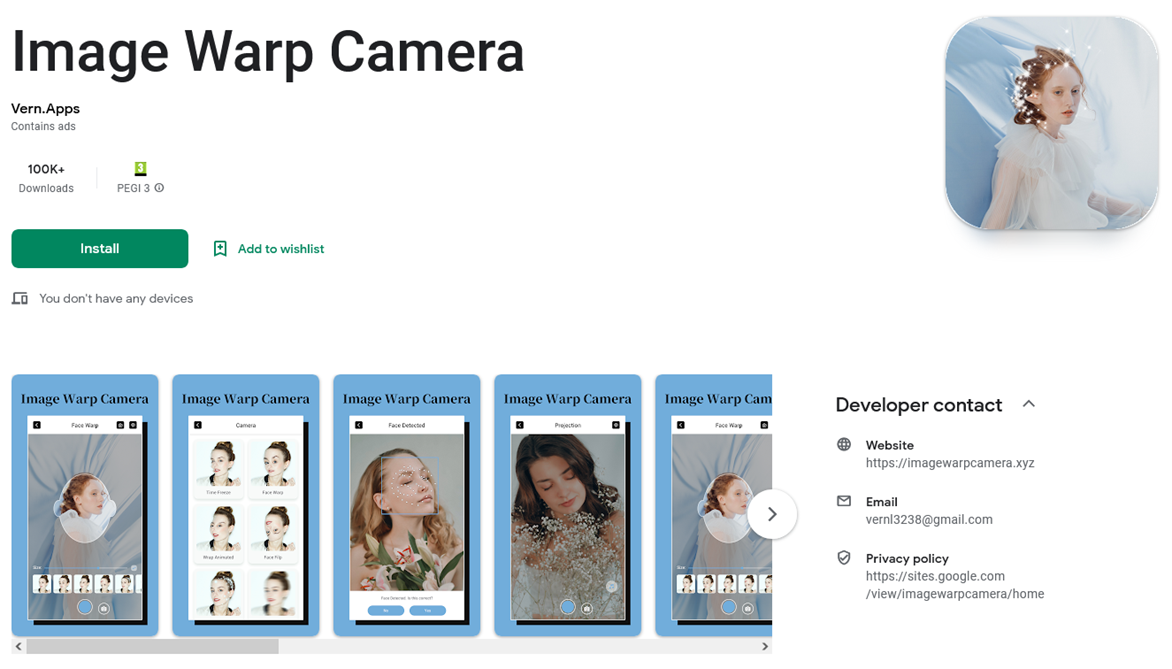
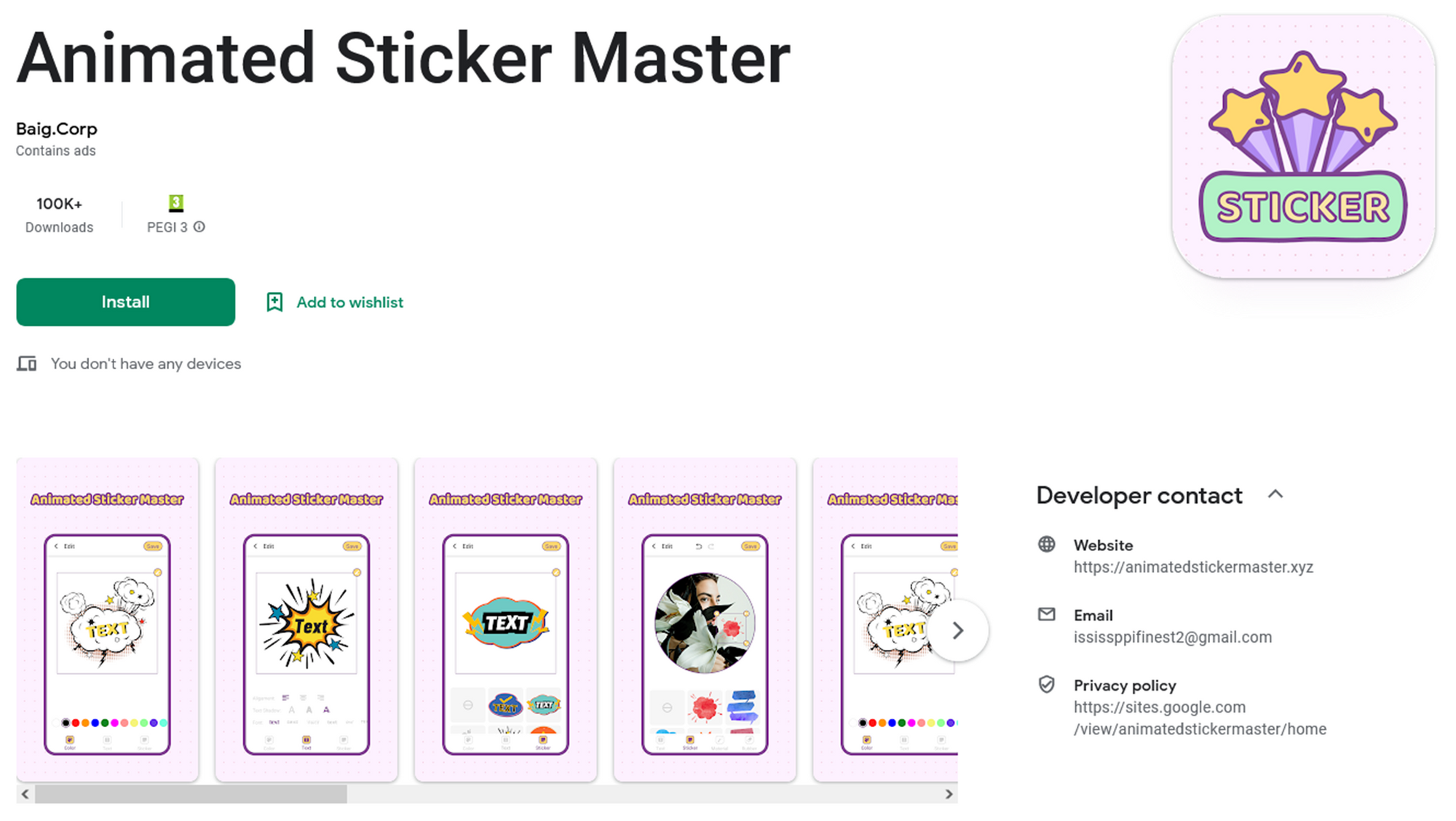
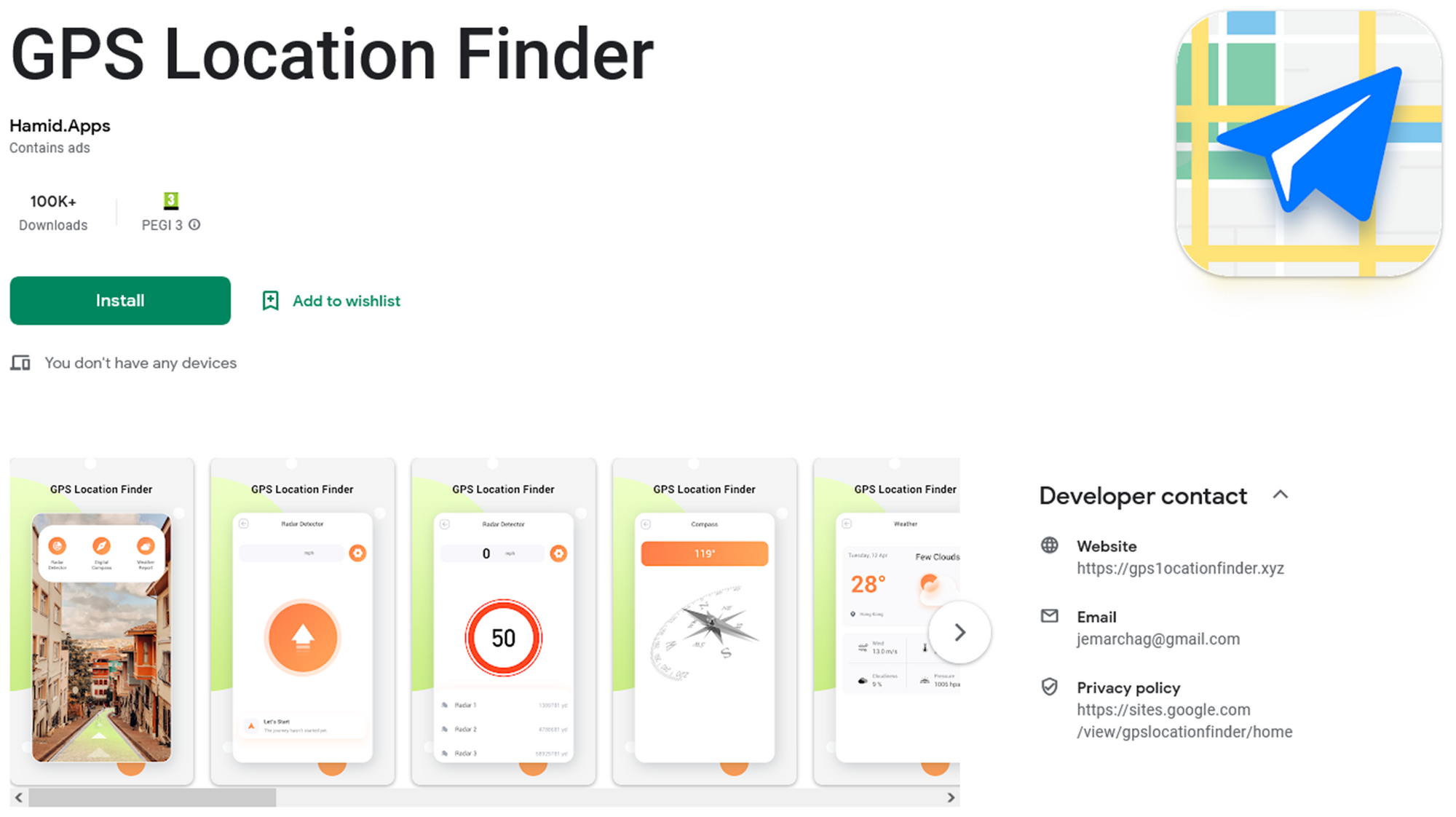
Conclusions
While official stores are usually very good at weeding malicious or dangerous applications out, some history shows that a small number of bad apps manage to get through and make victims until they get reported. Just because we download an app from the official store doesn't mean it will be safe. We continue to build new detection capabilities in Bitdefender Mobile Security to help users identify bad applications and have them removed from the system.
You can also follow a few simple rules that can keep you safer:
- Don't install apps that you don't really need
- Remember to delete apps you no longer user
- Be wary of apps with a large number of downloads and few or no reviews
- Be wary of apps that request special permissions, like Drawing over apps or access to Accessibility
- Be wary of apps that request access to permissions that have nothing to do with the advertised functionality
- Always run a security solution in the background that can detect malicious behavior. Just because an app is downloaded from an official store doesn't mean it's safe.
Indicators of Compromise
APK hashes
Package name | Hash | Downloads |
gb.packlivewalls.fournatewren | 83fc9c22697d23126105bef2ac956c83a9b5cc700a3635ba93ccf999d15be5cc | 100K+ |
gb.blindthirty.funkeyfour | 5df41117cfb8fdf4549c0cad570c30411770857783b40d7a0eb5cee5c9a01623 | 100K+ |
gb.convenientsoftfiftyreal.threeborder | 1dc46e16a7e477b9cd04a9a29c881254512d0ad5e89be6b120f30b06d4f5991b | 100K+ |
gb.helectronsoftforty.comlivefour | 92dcedc7054adde430407f430ee444ba6c0d70d5787eb92295360fc015b1f029 | 100K+ |
gb.fiftysubstantiated.wallsfour | beb0e689572650355ad39165cfee0f3695507a39213913a54718631cb5d17b6b | 100K+ |
gb.actualfifty.sevenelegantvideo | 1ccd7ac60d2caa3ffb56648ba5dfbd942f9ad0416de0c215f3d11457a5a36d55 | 100K+ |
gb.crediblefifty.editconvincingeight | 123a589ee242ee8ab1b072cbed287b4a20793e02f81a0cbe866ed346d68e0cb4 | 100K+ |
de.eightylamocenko.editioneight | 46141428f4c5d878b2644aa76cf96ad277e5038443698e4232fd3d9c0eb2ed1c | 100K+ |
gb.convincingmomentumeightyverified.realgamequicksix | 731a6d533edbedf5944f6d3660c3984ff41950d4b748e1e1c41b8457ccef0a4a | 100K+ |
gb.labcamerathirty.mathcamera | 9453085d60429987598c44c81693d733c38468bc233feefef46f84769c24fd15 | 100K+ |
gb.mega.sixtyeffectcameravideo | b40cca66d13d28745098fce90ac71d451ce28853ed81a7ff9f8bd908d91512db | 100K+ |
gb.theme.twentythreetheme | 0a366901588120665560c1e5dd0f7394ab6fedd4563c4c2951822b4194a8a42b | 100k+ |
gb.tolltwentytwo.ikey | d9bb7bf435c9af3e736bcc16626cf33e3b6e675a5f0a8fd1acd7e8c48e1bcd51 | 50K+ |
com.smart.tools.wifi | 0e4f1b1a22b059b95a828215739298335b1fff7f54cf85c1c75fc30ca5ca6cd6 | 10K+ |
jkdf.gds.gds.g | 4e5ea73770c5bee7fb8cbaeb188d2d7258ba8879cfdb4d459dfbdd7dd9a3e650 | 10K+ |
com.newsoft.camera | 9102fd2b2a6c38a36e344db0c836c05172aff9169ff4389195ade3cc47cd086b | 100K+ |
com.xmas.artgirlswallpaperhd | 985600862b5fc4de0ec62322bf9eee4b6c0cc3fc5db6f23cb65cbe81088a3c8d | 100k+ |
hj.jk.jikj.jkj | 0cf16f21330acfb9006e8fa1d67d5f6d48e0623390482ce4835d1064e38c58d6 | 50K+ |
com.creator.smartqrcreator | 4cd13ce239f6567744a2b4e9819cb420c3e311e05c1afab9d784eb344c8d4868 | 10K+ |
finze.lockgti.dae.cag | 1b1d7e825c2299a17309074a2d411ee3480501e417482331f020d93a21c08e95 | 500+ |
kk.f.ea.tew.t | 45cc6ac4b52492291bc572fa253dcc8db53b167080dd08490d16f8218b8ebfc3 | 100K+ |
com.xmas.girlsartwallpaper | 3b6639df04f9745ff74d9fe58dcd529d58208248358291d06e65e04aa2481d97 | 10K+ |
sc.qs.vak | e51585871b56d9c7707f8b41ab045dc26e11f976b519cc8e2fdc7a8cf79875e0 | 50K+ |
zzhse.ge.ge.ge.e | 16d5fd1ab5cb0bea28dfb7333b7b419b5de00024d391a3cd8dce9a0823e09cfc | 100K+ |
ice.ccylice.volume | cb9fc87ff97e398a4375062d5d5ab8d29706d830cd2ef6fcde5aea30f6f4a45d | 50K+ |
ck.lad.secret | 4240ca3ea6eba010ee3b169cda066d8beeb7b8bf7a065abfeac9b75a301a1706 | 10K+ |
smart.ggps.lockakt | b720175c57ed84fe7fec73554dcf12e71c33e6a322a23b0663dc132edc7203ee | 10K+ |
am.asm.master | a00e1b5ca10efdf11fbd3c45349c4e3994134e3100a23f50df62a9398529b176 | 100K+ |
com.charging.show | c519c9b63ce046c737fe9c222436f4138acfe9de277cc4da6019b8c3533e9aa9 | 100K+ |
com.voice.sleep.sounds | 9885ef4f3dfff7962c8f2e319957d07755c192e68978962962492e60c73ac222 | 100K+ |
joao.de.def.e.aew | 0ecaee04b59c137760b7aafa46772a3be7e3581b36d79b5c61ea713ccfe5a386 | 10K+ |
ifa.nod.vys | 69f94ac8d1ce85d0904a3cafb7828b84e18ecd858a2d56aa4c2fdd1fd7afc02e | 10K+ |
qu.motor.astrology | 134aeabf2c66be6af458d5d51c22d237c1f260f1ab10dcb99b714eba5d8bff73 | 10K+ |
ice.ccylice.colorize | 449328469b38378ca1214c421305d0706dca6cc79a68ea2e5e2904a519968c03 | 10K+ |
gb.sixtycreativecyber.magiceleganttwo | 054f8bfa280654b0a5cc9b3a8652e438fb77dc63d66ffb10c06743ccf290342b | 50K+ |
tags
Author

I'm a Security Researcher at Bitdefender, and when I'm not looking at code, I spend my time enjoying a good book, traveling, and swimming.
View all posts
As part of Bitdefender’s Android team, Razvan’s focus is malware threat research, but he also likes to mingle with statistics and machine learning. In his free time he's either hiking or gaming
View all posts
Junior Security Researcher at Bitdefender, eager to learn anything about computer works. In his free time, he likes to take motorcycle rides and travel.
View all posts
Junior Security Researcher at Bitdefender, I am passionate about cybersecurity, and I love mountain trips.
View all postsSilviu is a seasoned writer who's been following the technology world for more than two decades, covering topics ranging from software to hardware and everything in between.
View all postsRight now Top posts
Infected Minecraft Mods Lead to Multi-Stage, Multi-Platform Infostealer Malware
June 08, 2023
Vulnerabilities identified in Amazon Fire TV Stick, Insignia FireOS TV Series
May 02, 2023
EyeSpy - Iranian Spyware Delivered in VPN Installers
January 11, 2023
Bitdefender Partnership with Law Enforcement Yields MegaCortex Decryptor
January 05, 2023
FOLLOW US ON SOCIAL MEDIA
You might also like
Bookmarks
















