A GIF Image Could Have Let Hackers Hijack Microsoft Teams at Your Firm

A critical vulnerability has been patched in the Microsoft Teams work collaboration platform after security researchers discovered a way in which hackers could compromise accounts and steal data with something as seemingly harmless as an animated .GIF image.
With the Coronavirus pandemic crisis making companies force their employees to work from home, the use of collaboration platforms like Microsoft Teams - which has video chat, instant messaging, and file-sharing capabilities - has risen dramatically.
Unfortunately, As the threat researchers at CyberArk explain, a flaw in both the desktop and web browser editions of Microsoft Teams could have been exploited by malicious hackers to read users' messages, send messages pretending to be from users, create groups, and control Teams accounts in a variety of ways.
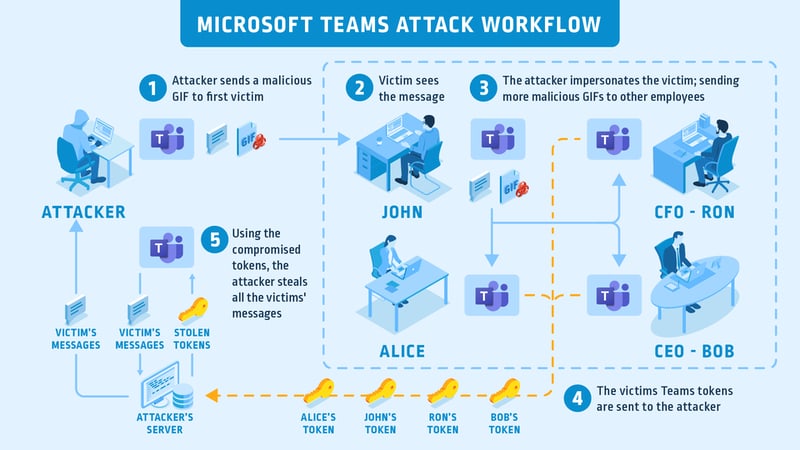
In fact, a single .GIF image sent to a Microsoft Teams user could have been enough to hijack multiple business accounts, traversing through an organisation like a worm.
Users wouldn't even have to share the dangerous .GIF to be impacted. All that would be needed was for other users to see the .GIF image via Microsoft Teams, each time stealing authentication tokens and dramatically increasing the attack's ability to spread through an organisation.
As Omer Tsarfati, a researcher at CyberArk explained, the impact of such an attack could be significant for any business:
"Eventually, the attacker could access all the data from your organisation Teams accounts – gathering confidential information, meetings and calendar information, competitive data, secrets, passwords, private information, business plans, etc."
Many businesses are currently struggling enough without the additional nightmare of cybercriminals stealing their sensitive corporate secrets and compromising their network.
Fortunately, for the attack to succeed hackers would have to have already compromised a subdomain belonging to the targeted organisation, on which to host the malicious image.
The need to leverage an attack off a vulnerable subdomain significantly reduces the ability of an attacker to successfully pull off an attack.
But it does underline the need for all organisations to properly audit what subdomains might exist - including those initially set up for test and development purposes or a short-lived marketing campaign - to make sure that they are not exploited at a later date.
The vulnerability was responsibly disclosed to Microsoft on March 23rd. Within a month, Microsoft had patched the security hole, which has only been made public now.
Microsoft says that it has not seen any evidence that the vulnerability was exploited in the wild by criminals.
tags
Author

Graham Cluley is an award-winning security blogger, researcher and public speaker. He has been working in the computer security industry since the early 1990s, having been employed by companies such as Sophos, McAfee and Dr Solomon's. He has given talks about computer security for some of the world's largest companies, worked with law enforcement agencies on investigations into hacking groups, and regularly appears on TV and radio explaining computer security threats. Graham Cluley was inducted into the InfoSecurity Europe Hall of Fame in 2011, and was given an honorary mention in the "10 Greatest Britons in IT History" for his contribution as a leading authority in internet security.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










