Bandwidth Security Is Critical in Wake of Rogue IoT Botnets Targeting Telecom Sector

Bandwidth security against rogue IoT botnets could be the next critical investment priority for the telecommunications sector after a report from NOKIA found that 78 percent of network-based malware detection in CSP networks in 2018 is attributed to IoT botnet activity used in DDoS and crypto-mining activity. This is up a staggering 33 percent from two years ago, confirming that malware is here to stay and growing in complexity.
IoT devices have IP addresses to connect to the internet so they can gather and swap data. Once these devices are infected with malware, hackers turn them into IoT botnets that will actively keep scanning the internet for more vulnerable devices with open ports or weak credentials to grow the botnet. The goal is for the IoT botnet to keep on expanding, most likely for use in launching large-scale DDoS attacks to cripple critical infrastructures.
Other investigations have revealed that the telecom industry is actively targeted by a new type of Trojan malware, especially in the Middle East, Europe and North America, as part of a major cyber espionage operation. NOKIA further warns that, unlike in previous years when smartphones and web-browsers were in the spotlight for cryptocurrency miners, IoT botnets are now a top target. This is the case especially for Monero mining algorithms that don’t need special conditions or equipment and can be easily and efficiently set up on regular computer hardware and vulnerable connected devices turned into botnets.
Communications service providers play in the major leagues, so they are a strategic target for cybercriminals due to the high volume of sensitive information they operate with. Falling under critical infrastructure attacks, the loss of confidential or regulated data following IoT-malware exploits or advanced malware attacks could be a critical issue not only for the companies involved, but also for their customers. NOKIA found strong “evidence of malware infections in consumer and enterprise endpoint devices, including mobile phones, laptops, personal computers, notepads and the new generation of Internet of Things devices.”
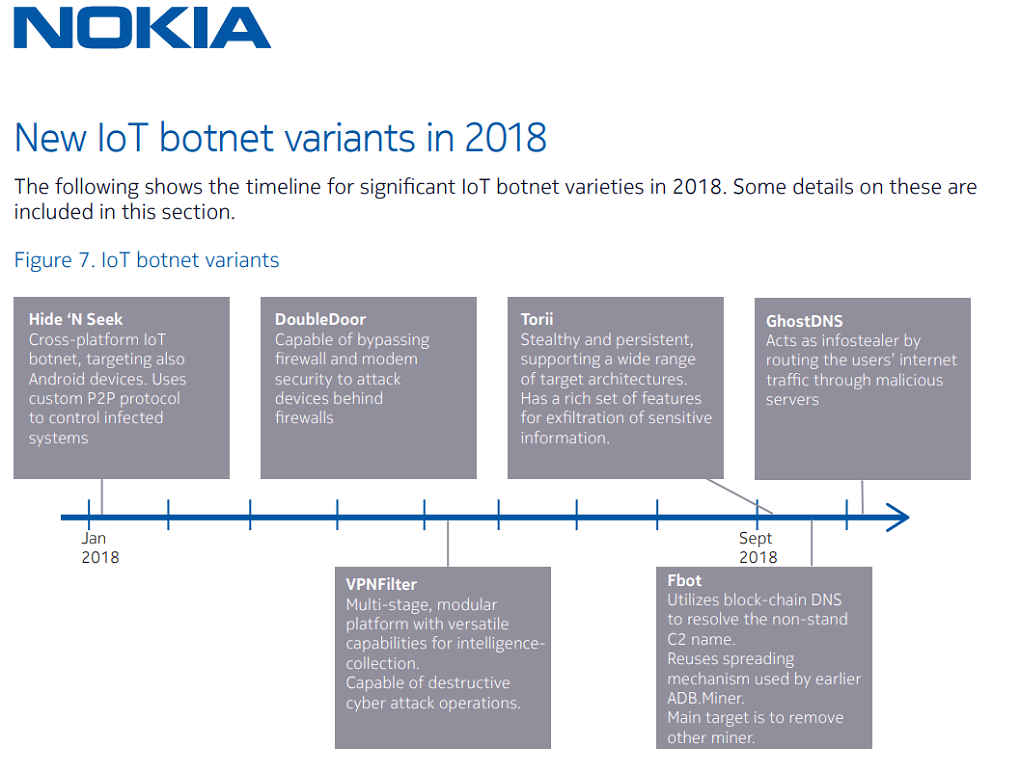
The new IoT botnet variants reported by NOKIA in its monitored infrastructures in 2018, possibly malignant for CSP networks, include Mirai-based HideNSeek, DoubleDoor, VPNFilter - allegedly authored by Russian group “Fancy Bear” to destroy Linux/Busybox based routers and industrial control infrastructure, Torii responsible for telnet attacks from Tor exit nodes, Fbot that targets Android-operating IoT devices by scanning for an open port to get shell access over the infrastructure, and GhostDNS, which is used on home routers to steal banking credentials via fake banking servers.
Integrating knowingly vulnerable, open-to-attack IoT devices with mobile and fixed networks will compromise the company networks and reputation, among others. Although client-based anti-malware software is critical to ensure network security, CSPs need a strong mitigation and containment strategy to prevent the proliferation of IoT-malware exploits.
tags
Author

From a young age, Luana knew she wanted to become a writer. After having addressed topics such as NFC, startups, and tech innovation, she has now shifted focus to internet security, with a keen interest in smart homes and IoT threats. Luana is a supporter of women in tech and has a passion for entrepreneurship, technology, and startup culture.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










