Bitdefender Threat Debrief | January 2025

As ransomware continues to play a significant role in the cybercrime ecosystem, understanding current incidents and patterns that emerge in ransomware group activities, TTPs, and victim trends is important. Examining the latest events and identifying the top threats in the ransomware landscape helps to prioritize and share information to improve security awareness, cyber defense, and incident handling strategies. We analyzed data from ransomware group websites from December 1 to December 31, identifying a total of 530 claimed victims.
Now, let’s explore the notable news and findings since our last Threat Debrief release.
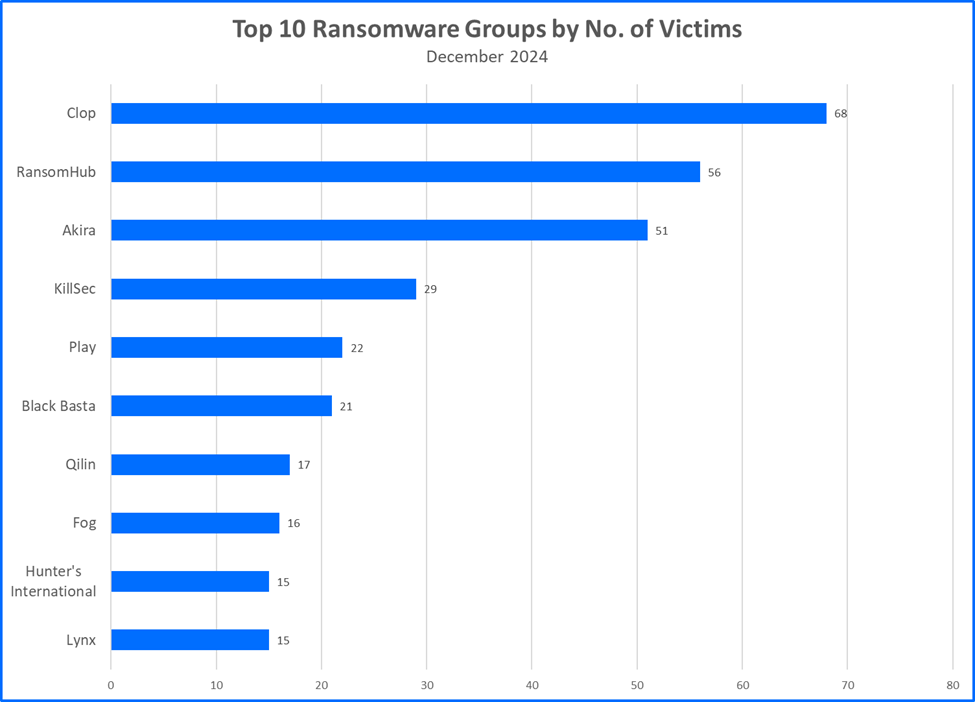
- Clop resurgence propels the group into the Top 10: The Clop ransomware group (also shown as Cl0p) claimed the greatest number of victims in December of 2024, surpassing RansomHub and Akira. While Clop gained notoriety in 2023 for breaches that leveraged several MOVEIT vulnerabilities, including CVE-2023-34362 and a $10 million bounty offered by the U.S. government, the group now targets a different set of vulnerabilities.
- CVEs exploited by Clop affect the Cleo product line: Clop has established initial access to victim systems in recent months by exploiting vulnerabilities in software from Cleo’s file transfer product line: Harmony, LexiCom, and VLTransfer products. CVE-2024-50623 is a vulnerability that allows the upload and download of files to occur on affected systems without restrictions. The exploitation of this vulnerability allows a threat actor to perform remote code execution with elevated privileges. CVE-2024-50623 affects Cleo Harmony, LexiCom, and VLTransfer versions that are older than 5.8.0.21. Organizations that manage the affected products are advised to implement the latest patches. CVE-2024-55956 is another vulnerability that Clop exploits to establish initial access. After exploiting it, an unauthenticated user can execute commands such as those found in bash or PowerShell scripts, by abusing the default settings of the Autorun directory. CVE-2024-55956 affects Cleo Harmony, LexiCom, and VLTransfer versions that are older than 5.8.0.24. Organizations that manage the affected products are advised to patch them to version 5.8.0.24.
- Rostislav Panev is indicted on more than 40 charges for his involvement in LockBit operations: The United States Justice Department unveiled the charges accrued by Panev, an Israeli-Russian developer who created several iterations of LockBit between 2018 and 2024. Panev was arrested in Israel this past August; and, there is evidence of his correspondence with Dmitry Yuryevich Khoroshev to write LockBit’s builder. Khoroshev is a Russian national and the lead administrator in LockBit’s RaaS operations; he used the LockBitSupp handle. The indictment of both suspects this year comes about as the U.S. continues with its joint operations to investigate and takedown LockBit.
- LockBit announces what’s to come: LockBit 4.0: A recent post on LockBit’s data leak site titled LockBit 4.0 announces a release slated for February 2025. Site visitors interested in getting involved are encouraged to join the affiliate program. To get started, a user can “sign up and start (your) pentest billionare journey…” Whether this 4.0 release will involve a new data leak site alongside additional improvements to the LockBit ransomware code concerning customization, encryption functionality, defense evasion, and other components remains unknown.
- NetWalker ransomware operator receives prison sentence: Daniel Cristian Hulea, a notorious cybercriminal who supported NetWalker’s ransomware operations, now faces a 20-year prison sentence. Hulea’s role in exploiting vulnerabilities and issuing ransom demands against victim organizations, including those from critical sectors in the U.S. resulted in NetWalker accruing more than $21 million. NetWalker is a ransomware group with a restrictive affiliate program so this sentencing of another key group member, more than two years after the sentencing of operator Sebastian Vachon-Desjardins, is highly significant.
- Black Basta and Fog rank among Top 10 Ransomware Groups: Black Basta and Fog have reached the sixth and eighth positions Top 10 Ransomware Groups. This follows a pattern of campaigns, including attacks that involved social engineering tactics including the use of Teams to masquerade as IT Support.
- ZLoader malware is updated to hamper detection and mitigation efforts: ZLoader is a type of malware used to deliver multi-stage payloads to victim systems while providing coverage to counter against common incident discovery and malware analysis tactics. ZLoader’s recent iteration, version 2.9.4.0, offers a customized DNS tunneling capability. The DNS tunneling capability is a valuable resource for attackers; it is a protocol that offers a workaround to interact with a C2 server and elude detection systems that may not identify the DNS packets or their contents if the traffic is encrypted. An attacker can use the tunneling capability combined with the interactive shell to exfiltrate data or transfer other tools. The ransomware group Black Basta has deployed ZLoader in their targeted social engineering campaigns; the malware is dropped after the GhostSocks payload is added to a victim system.
- FunkSec is on the move: The ransomware group FunkSec has been identified in recent reports of victims affected by data theft and ransomware. While information is still developing on more than eighty incidents associated with FunkSec and the nature of their operations, the group boasts a data leak site and a growing number of posts, including various breaches they have claimed in the past month. Several sources note that FunkSec uses AI in their ransomware and hacktivist campaigns, including those affiliated with the hacktivist groups DesertStorm, El_farado, and Bjorka.
Top 10 Ransomware Families
Bitdefender's Threat Debrief analyzes data from ransomware leak sites, where attacker groups publicize their claimed number of compromised companies. This approach provides valuable insights into the overall activity of the RaaS market. However, there is a trade-off: while it reflects attackers' self-proclaimed success, the information comes directly from criminals and might be unreliable. Additionally, this method only captures the number of claimed victims, not the actual financial impact of these attacks.
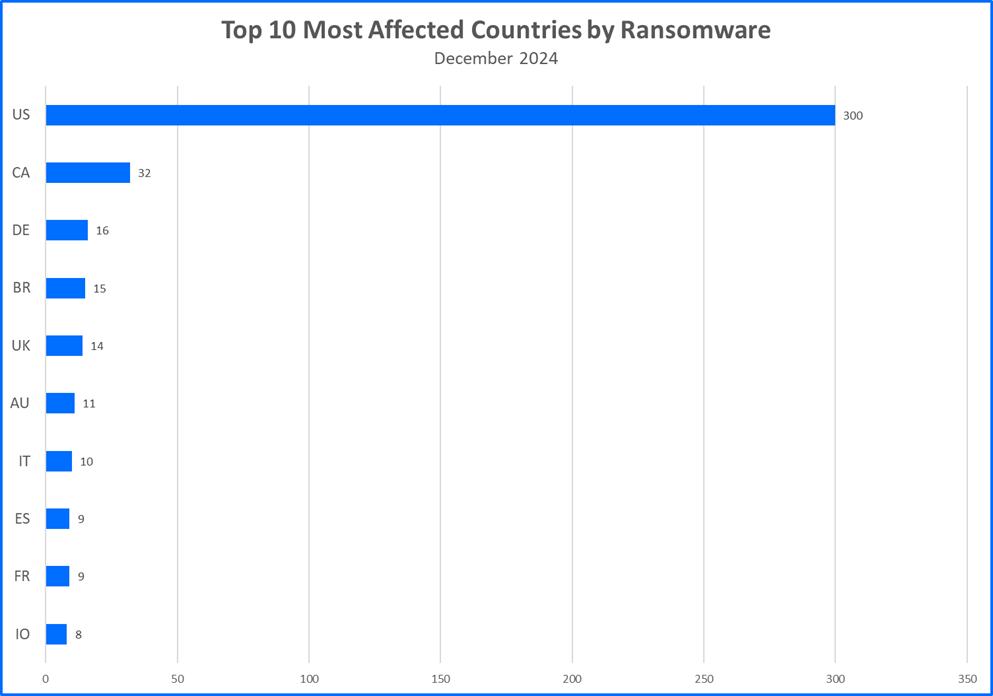
Top 10 Countries
Ransomware gangs prioritize targets where they can potentially squeeze the most money out of their victims. This often means focusing on developed countries. Now, let’s see the top 10 countries that took the biggest hit from these attacks.
About Bitdefender Threat Debrief
The Bitdefender Threat Debrief (BDTD) is a monthly series analyzing threat news, trends, and research from the previous month. Don’t miss the next BDTD release, subscribe to the Business Insights blog, and follow us on Twitter. You can find all previous debriefs here.
Bitdefender provides cybersecurity solutions and advanced threat protection to hundreds of millions of endpoints worldwide. More than 180 technology brands have licensed and added Bitdefender technology to their product or service offerings. This vast OEM ecosystem complements telemetry data already collected from our business and consumer solutions. To give you some idea of the scale, Bitdefender Labs discover 400+ new threats each minute and validate 30 billion threat queries daily. This gives us one of the industry’s most extensive real-time views of the evolving threat landscape.
We would like to thank Bitdefenders Vlad Craciun, Mihai Leonte, Andrei Mogage, and Rares Radu (sorted alphabetically) for their help with putting this report together.
tags
Author

Jade Brown is a threat researcher at Bitdefender. A cybersecurity thought leader who is passionate about contributing to operations that involve cybersecurity strategy and threat research, she also has extensive experience in intelligence analysis and investigation.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










