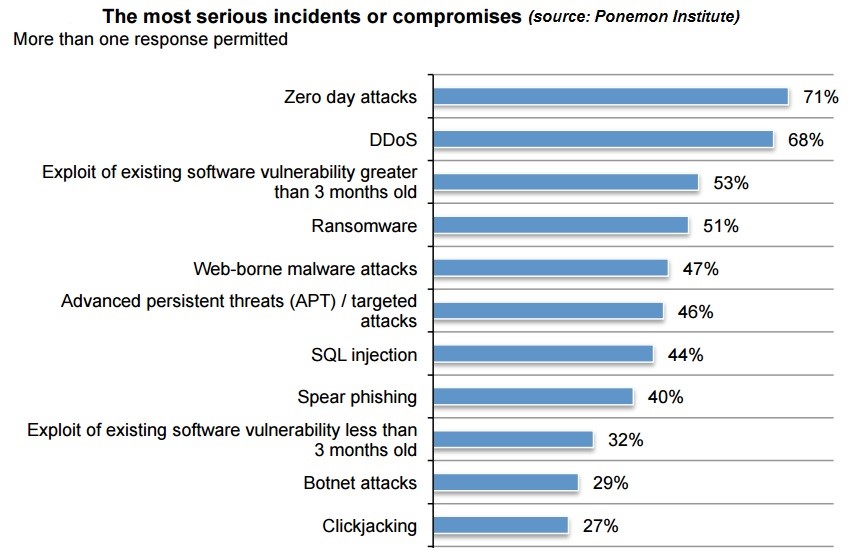
Blitzkrieg Attacks and Employees, Companies’ Top Security Concerns, Confirming Bitdefender's 2016 Predictions

Cyber attacks involving destructive malware will become a bigger problem for organizations. A growing trend in cyber attacks has been the unleashing of destructive malware such as Cryptolocker and Shamoon. Only 38 percent of respondents in a recent survey by Ponemon Institute they have a strategy to deal with destructive software.
Zero-day attacks are the most serious type of incidents and compromises for companies, according to 71 percent of respondents. DDoS was second, mentioned by 68 percent of respondents.
Most respondents also say the consequences of an exploit of an existing software vulnerability greater than 3 months old (53 percent) and ransomware (51 percent) can be severe.
Companies still struggle to have the necessary resources to minimize IT endpoint risk: only a third agree that they have ample budget and staff. As a consequence, 69 percent of respondents say their IT department cannot keep up with employee demand for greater support and better mobile device connectivity and 71 percent say their endpoint security policies are difficult to enforce.
How will organizations deal with increased endpoint risk?
- Ninety-five percent of respondents said that their organization will evolve toward a “detect and respond” orientation from one focused on prevention.
- Seventy-seven percent say they have added or plan to add a threat intelligence component to their security stack.
- Another popular trend is the notion of the endpoint as a security sensor. In other words, one where state or context data collected at the endpoint is used to determine if it has been or is being compromised. Fifty-six percent of respondents say their organizations are doing this now or plan to start.
- Also important is the need to develop an offensive security capability (i.e., discover who is behind an attack and then counterattack). Sixty-four percent of respondents are pursuing this now or plan to pursue it in the near future.
- A virtualization technology with embedded, real-time endpoint sensor is considered a positive investment to improve security posture. Sixty-four percent of respondents say ity would have a significant impact or impact on an organization’s approach to achieve enhanced endpoint security.
Careless employees remain the biggest security threat in 2016
Negligent or careless employees who don’t follow security policies are the biggest threat to endpoint security in organizations.
81 percent of respondents say the biggest challenge is minimizing the threat of negligent or careless employees, from 78 percent in 2015. Since 2013, the percentage of respondents who say threats caused by malware infections that are stealthier and difficult to detect increased from 32 percent to 56 percent. The threat caused by the growing number of insecure mobile devices in the workplace increased from 33 percent to 50 percent.
Employees’ use of mobile devices and commercial cloud applications continues to increase endpoint risk significantly. Similar to last year’s findings, respondents report the use of commercial cloud applications (72 percent), BYOD (69 percent), and employees who operate from home offices and offsite locations (62 percent) have significantly increased endpoint risk.
Mobile devices, vulnerabilities in third-party applications and malicious insider risks have increased significantly since the study was first conducted in 2011. Despite the risk of mobile devices, 56 percent of respondents say their employees are allowed to use personal devices to connect to the network, survey shows.
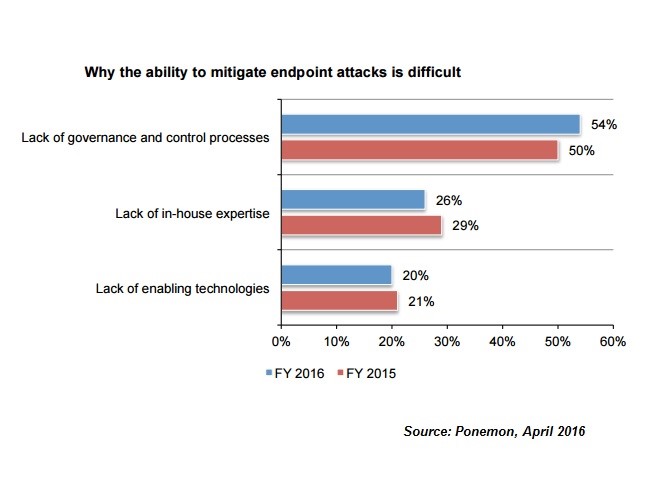
Most companies lack processes, governance, required to stop cyber attacks
More than half of companies (54%) perceive the lack of governance and control processes as the biggest gaps in stopping attacks on endpoints.
On average, respondents believe 49 percent of attacks on an organization’s endpoints can be realistically stopped with enabling technologies, processes and in-house expertise.
The main obstacle to mitigating these attacks is a lack of governance and control processes, which would include training and awareness programs for employees and enforcement of endpoint security policies.
Lack of in-house expertise was mentioned by 26% of respondents while lack of enabling technologies is a concern for 20% of IT professionals.
The inability to identify critical assets or data and to properly react to security breaches is a major deficit of all companies, from small to large, as we previously noted. Attackers targeting non-critical systems could gain access to confidential business information that should be stored on a segregated network or infrastructure. The disclosure of classified information could have devastating consequences for a company’s financial health.
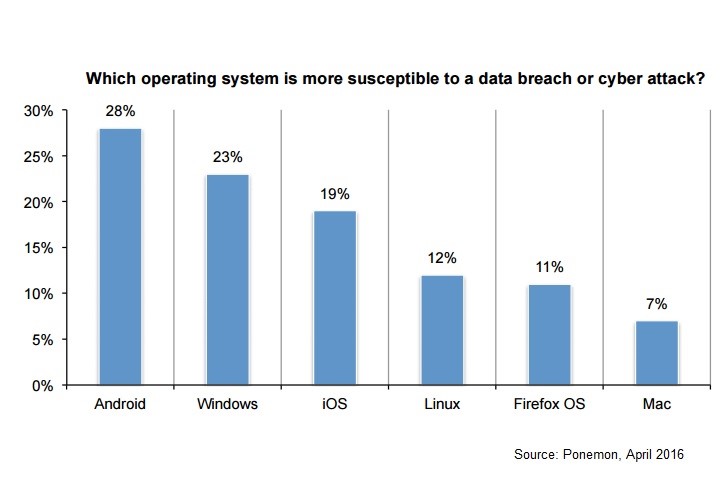
IT pros see Mac as safest OS; Windows, Android seen more vulnerable
Some 28 percent of IT and IT security practitioners say Android is the operating system most vulnerable to a data breach or cyberattack while 23 percent cite Windows, according to a survey by Ponemon Institute.
The least vulnerable is the Mac, which was picked by 7 percent of respondents.
However, recent developments show Mac users have become targets for cyber attacks. This March, Palo Alto Networks researchers revealed KeRanger ransomware targeted Mac users for the first time, realizing Bitdefender’s predictions about ransomware’s expansion to new operating systems in 2016.
Ransomware for Mac was seen as a major threat in the top predictions list in cybersecurity for 2016 by Bitdefender CTO Bogdan Dumitru:
“We’ve already seen ransomware for Linux, Windows and Android. Mac OS is just around the corner,” he said in December 2015. “It targets both consumers and companies, and the 2016 versions not only will encrypt files and ask for ransom, but will also make all documents available on the internet if ransom is not paid. In an ironic twist, the victim will be able to recover encrypted files – when they are uploaded on the internet for public shaming.”
"On the business side we will see an increase of targeted attacks and strongly obfuscated bots, with a short lifespan and frequent updates. Most of these attacks will specialize in information theft", Bogdan Dumitru predicted. "Attackers will be in and out of an organisation in a few days, maybe even hours. APT, which currently stands for Advanced Persistent Threats, should change to Advanced Penetration Threats, or even BA for Blitzkrieg Attacks. Lateral movement in the infrastructure of cloud service providers will increase with the advent of tools that allow hackers to compromise the hypervisor from a virtual instance and jump to a different virtual machine. This scenario is particularly dangerous in “bad neighbourhood” environments where an ill-intended party could get to share a physical system with a legitimate service provider or business."
At the same time, half of Mac OS users complain that ads and unwanted apps (PUA) are disrupting their browsing experience and endangering online safety, as Bitdefender researchers found this winter. Almost nine in 10 iOS and OS X apps using resource-sharing mechanisms and IPC channels are completely exposed to unauthorized cross-app resource access and password theft, or XARA, attacks, according to a report by university researchers from Indiana University, Georgia Tech and Peking University.
Ponemon Institute surveyed 694 US IT and IT security practitioners involved in endpoint security in a variety of organizations.
tags
Author

Former business journalist, Razvan is passionate about supporting SMEs into building communities and exchanging knowledge on entrepreneurship. He enjoys having innovative approaches on hot topics and thinks that the massive amount of information that attacks us on a daily basis via TV and internet makes us less informed than we even think. The lack of relevance is the main issue in nowadays environment so he plans to emphasize real news on Bitdefender blogs.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks