Does Bitdefender Hypervisor Introspection Replace Traditional Security?
The term “traditional security” has gone through much transformation within the past couple of years, with next-gen security solutions arguing that security vendors with decades of experience have been doing security wrong. With machine learning heralded as the future of security, many businesses are left perplexed by a marketing conflict that solves none of their problems.
However, the hypervisor has emerged as a surprising answer to a security dilemma debated by security experts. Security through the hypervisor was not designed to fully replace traditional security. Instead, it adds a layer that’s hardware-enforced and offers the solution to the problem of isolation versus context that’s been plaguing businesses opting for increased cloud adoption. This implementation should not be regarded as a magic bullet to prevent every type of attack, but as a unique technology that can detect and prevent advanced attacks and zero-day vulnerabilities.
Complex Threats Designed to Evade Traditional Security
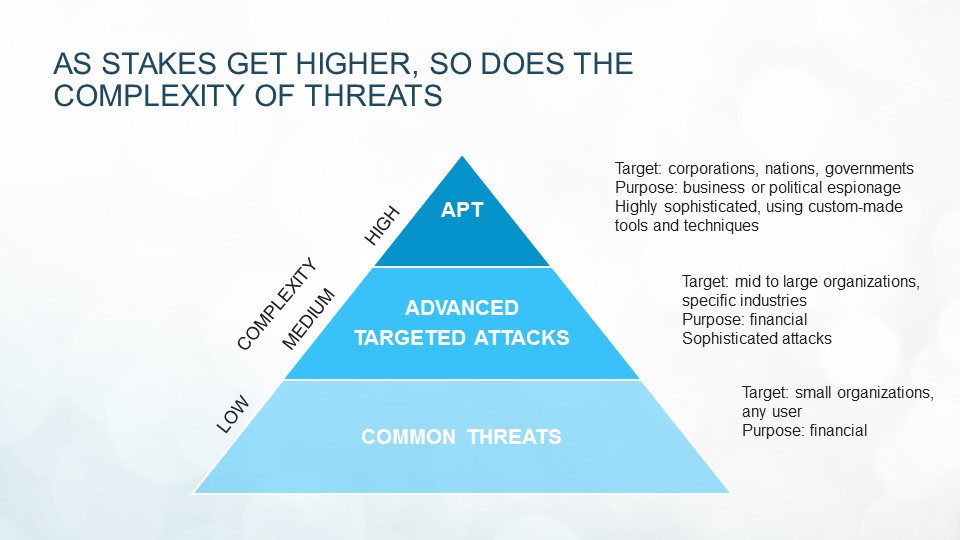
Malware and advanced attacks can basically be organized by their complexity and their targets. If common malware - such as file infectors, Trojans, key loggers, etc. – are low in complexity and usually target the average user or small organizations, advanced targeted malware is usually more complex and targets mid-sized to large organizations.
Traditional security solutions have focused mostly on detecting these two main threats, as they’re more widespread and they’re built for mass infection or to affect specific industry verticals. They’re great at spotting simple or moderately complex malware but, when it comes to highly advanced threats built to evade an organization’s defenses, they’re sometimes in the dark. The average detection time of a breach caused by a highly sophisticated threat is estimated at around 5 months. During this time, companies could suffer irreversible damage.
Some of the most complex threats to date are known as APTs (Advanced Persistent Threats) and their purpose is to specifically target a specific corporation, nation, government or business for political espionage. Unlike previous threats, APTs are made using custom tools and are designed to evade traditional security solutions.
They’re built to remain undetected for long periods of time, to exfiltrate data, and persist for years within the target network. The whole point of these attacks is not to damage the infrastructure, but the business. Months after infiltration, a company could realize that they’re losing customers because of an APT that’s silently and covertly sending critical business data to their competition. Whether these attacks run on physical or virtual endpoints, the end result is always the same.
Hypervisor Introspection in a Nutshell
The cloud and virtualization have opened up new opportunities, as Bitdefender’s Hypervisor Introspection focuses on adding a new security layer by doing live memory introspection and PREVENTING attacks.
Traditionally, security involves having an agent within virtualized environments and optimizing that security agent so as not to affect the overall performance of the guest operating system, or the data center for that matter. Of course, inside the guest you play by the rules of the OS, as everything the endpoint security knows relies on what the OS allows it to know. For instance, consider a 0-day vulnerability of the kernel where an attacker patches the OS. In this case, the information retrieved by the security solution from the OS cannot be trusted.
Hypervisor introspection relies on hardware registers, CPU and hypervisor events that come directly from the hypervisor that manages every physical resource requested by the guest VM. Because it’s completely outside the guest VM’s operating system, hypervisor introspection can even protect the integrity of traditional solutions, keeping security events trustworthy
Think of hypervisor introspection as something that complements and protects in-guest traditional security solutions, because they all look and act just like any other application.
Even if an attacker tries to compromise the in-guest security solution, hypervisor introspection will prevent that tampering while also guaranteeing the integrity of any other application running inside the guest VM, something that no other security technology can claim to do.
What Hypervisor Introspection Can’t Do
We often make the mistake of saying that security means protection from malware. If we look at HIPAA or PCI compliance we understand that security has a broader range. Just think about encryption. If your storage gets stolen, you need something different than Hypervisor Introspection, as this technology focuses on attacks.
Advanced attacks focused on a single organization are generally created to exfiltrate data or carry out industrial espionage. Of course, other control mechanisms are in-guest, such as device control or web access control that can at some point detect the process of data exfiltration, but only after a breach has already occurred.
How Can Hypervisor Introspection Help Your Business?
By reducing advanced attacks to a handful of memory-based attack techniques – or evasion techniques – that exploit known or unknown kernel or application vulnerabilities, Bitdefender’s Hypervisor Introspection can guarantee the integrity of the data reaching SIEM and security analytics solutions that reside within guest OSs. That means that your data center’s IT security department will receive events from both traditional security solutions and Bitdefender’s Hypervisor Introspection that are guaranteed to be trusted.
Traditional solutions still play a major role in a business’s security, but it is increasingly clear that they are not able to fend off advanced attacks. Hypervisor Introspection can become an essential security layer in uncovering your security blind spots. It can complement existing security solutions, it can guarantee the integrity of in-guest VM applications, and it can PREVENT advanced attacks before data exfiltration ever begins.
tags
Author

Laurentiu Odoleanu is a Product Manager for Business Solutions, that’s responsible for product planning and execution of strategic business security technologies at Bitdefender. With a strong background in engineering and security, Laurentiu has a keen eye for identifying customer needs and translating them into clear product / feature plans. With close to a decade of experience in building and defining B2B solutions, he’s equally comfortable leading customer conversations or reviewing technology architectural designs.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










