FunkSec: An AI-Centric and Affiliate-Powered Ransomware Group

FunkSec is a ransomware group that has become more recognized in the past month due to their growing victim count and presence amongst other threat groups. Their victims, totaling more than 120 affected organizations, include those in government and defense, technology, finance, and education. FunkSec has claimed victims from several countries, notably those based in the United States, India, Spain, and Mongolia. Initial reports of FunkSec incidents emerged in November of 2024, and the group added a data leak site in December.
Numerous reports claim that FunkSec’s spike in activity since late 2024, along with their use of AI, makes them a highly dangerous and complex threat. In reality, the opposite holds true. FunkSec’s use of AI on its own does not make them remarkable or a threat worth monitoring. Understanding the implications of AI, the group’s entry into RaaS (ransomware as a service), and reports identifying iterations of their code can offer some insights. However, FunkSec’s tactics, such as strategic improvements to their data leak site combined with their revictimization approach and collaborations with other threat groups, position them as a threat actor that may see rapid advancements to elevate their capabilities and expand their opportunities to execute campaigns with continued support.
Entering the RaaS Ecosystem with the Help of AI
Artificial intelligence is used in ransomware operations for several reasons. It is important to understand the opportunities that exist to enter the RaaS ecosystem with AI and how FunkSec has leveraged it in their own operations.
An established ransomware group that has demonstrated a mastery of the coding elements and frameworks to implement, can use AI to bolster their exploitation development efforts and save time and resources as they make improvements to existing code.
However, developing the initial malware that is designed to steal data, render data and/or systems inaccessible, and fund a criminal enterprise is a daunting task for a newly formed group. This is why some emerging threat groups deploy ransomware that comes from the leaked code of common variants. Other groups model and refine their code based on elements that are available on GitHub and various open-source repositories.
Another option for the less established and experienced threat group that wants to develop and execute ransomware involves using AI to create the code itself. This eases the burden of the group’s workload and lowers the barriers to entering the RaaS ecosystem. FunkSec uses GenAI to create their ransomware code; the primary purpose of the ransomware is to perform encryption. It also modifies system settings and conducts system reconnaissance and defense evasion activities.
FunkSec’s Use of AI, the Behaviors Affiliated With It, and Limitations
FunkSec has used AI to develop code for an encryptor, which is an essential capability for a ransomware group. While FunkSec’s use of AI may appear clever on the surface, it underscores the group’s limited understanding of code development. FunkSec has also demonstrated a pattern of behavior that leans towards a reliance on AI, likely to compensate for gaps in their knowledge.
One behavior that establishes a connection to FunkSec’s consistent use of AI is the group’s implementation and retention of code that has comments in concise English. The language represented in the code differs greatly from the disfluent language that is featured across the FunkSec site and in posts on their forum.
FunkSec’s use of AI is also revealed by comparing the comments found in their ransomware code with other scripts that the group has released. Tools that FunkSec has used in the past include the Python script ddos1.py which executes a DDoS attack and FunkGenerator or funkgenerate.zip. In addition, FunkSec posted updates concerning the early iterations of the FunkSec ransomware alongside references to ReactGPT.
The behaviors illustrated thus far are not the only means available to demonstrate that FunkSec is a threat actor that is reliant on AI. A trail of inquiries on forums about how to hack systems also exists, showing that the group needs great operational and technical support due to their lack of knowledge. In November of 2024, one user named El_Farado posted on BreachForums; the user expressed an interest in learning how to hack systems and databases. They were looking for guidance because they did not know where to start. This theme of needing support due to a lack of know-how is explored further in the section detailing FunkSec’s current data leak site and forum. While FunkSec’s online correspondence paints a picture of a group in an early, novice stage, it is also important to identify the origins of the group’s code.
Code Origins and Releases
The initial iterations of FunkSec’s code shares properties that are found in the malware used by the threat actor named GhostAlgeria. FunkSec’s code is written in Rust, and it is understood that one of their tools, dev.exe, also originated from an Algerian-based threat.
FunkSec’s ransomware has undergone multiple updates with version 1, an intermediary version between version 1 and 1.5, version 1.5, and now version 2.0.
Elements of the original FunkSec code that have faced scrutiny include the code’s lack of customization options and redundant references in the binary. This means that rather than performing a controlled execution, the ransomware calls back to functions repeatedly rather than referring back to one instance. This is one aspect that supports the group’s use of AI to create code without thoroughly testing it or having a team of developers to improve upon it.
FunkSec’s Data Leak Site
FunkSec has gradually updated the code they use as well as their data leak site, which has allowed them to maintain a strategic presence online. A user accesses the FunkSec data leak site via an onion link. FunkSec created the site in late November of 2024 and is comprised of four sections: Listing, Auctions (this replaced the former section named Marketplace), Forum, and Ticket.
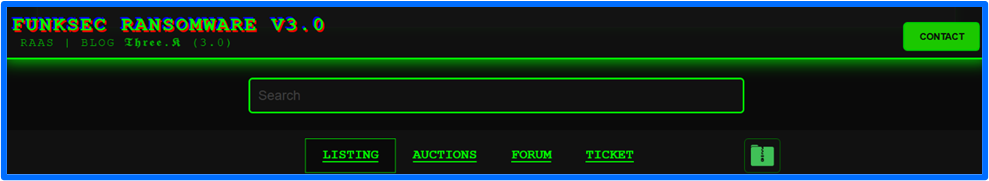
Figure 1: FunkSec DLS Main Page
FunkSec’s Breach Page and a Cryptic Post Announcing Changes
The Listing section on FunkSec’s site highlights exposed victims and the type of data that is exfiltrated from each organization. Active breaches include a countdown timer and closed ransoms have the text breach has ended. FunkSec recently removed Breach posts dating back to December 2024. And, based on the group’s post titled New routes, FunkSec will start new attacks soon.
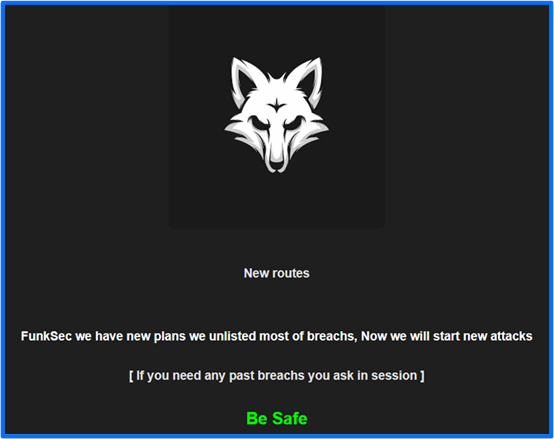
Figure 2: The FunkSec New routes Announcement
FunkSec’s cleanup of the Listing page is not the only change that has occurred. They have also changed their profit strategy. In January of 2025, FunkSec’s operations involved three parts. First, they conduct an attack or acquire victim data. Next, they post about the victims and victim data on their Breach page. Lastly, they add the stolen data to their internal marketplace for interested buyers to purchase it.
FunkSec’s marketplace area is no longer active. The elements that make up their operations now include encryption and data exfiltration, a ransom demand, and data auctioning rather than marketing. They have swapped out their marketplace in favor of an auction site named FunkBID. This gives FunkSec the means to not only exchange data with other parties but also cash in on bids from external sellers and create opportunities to receive sensitive data at variable price points.

Figure 3: FunkBID Logo
Going. Going...Still Going: FunkSec Rolls Out
FunkSec’s FunkBID Official Auction Market is a project that emerged in early February. It allows FunkSec to market data and other services and create a space for potential sellers. A user on FunkSec’s main page clicks Auctions to access the FunkBID site.
A FunkSec user navigates to Databases to browse current auctions or add a bid. Only users who have premium level access can do so. Bids for stolen data are time limited and awarded to the highest bidder. The data featured on the Databases page has prices that range from $100 to $1000. While FunkSec collects a portion of the bids accepted by external sellers, the percentage of earnings FunkSec receives is unknown.
FunkSec lists other pages on the FunkBID site such as Blackhat Tools, Source code, Malwares, and Access. At the time of this release, Blackhat Tools, Source code, and Malwares do not have any content featured on their pages. Access is a section that includes bids for sites or networks that hackers have already compromised.
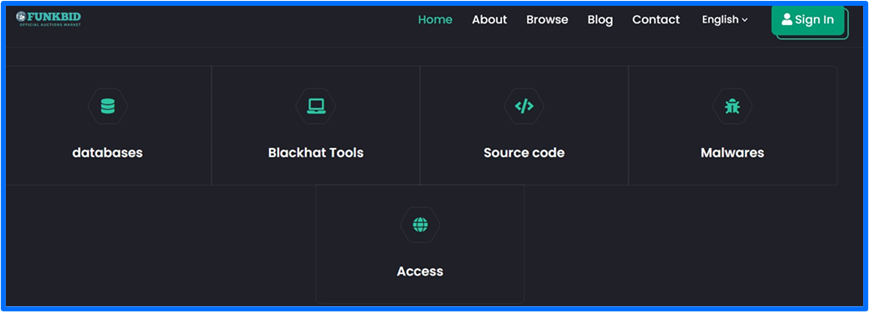
Figure 4: Sections of FunkBID
FunkBID’s Central Location
FunkBID Contact page lists the coordinates: 51°30'11.5"N 0°07'10.3"W. These coordinates point to a location south of the River Thames in London. While this area is not a match with prior locations linked to FunkSec’s user activities and history such as Algeria and Brazil, it is possible that FunkSec selected London as a base of operations to reduce suspicions or as deception tactic. They might have also selected London to offset limitations such as travel restrictions and stipulations surrounding the exchange of cryptocurrencies.
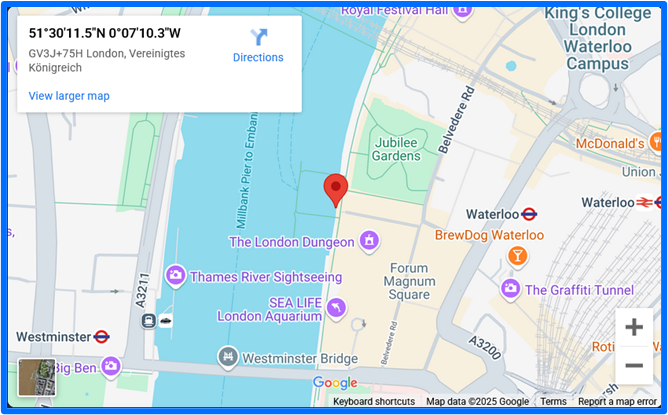
Figure 5: FunkBID Contact Coordinates: 51°30'11.5"N 0°07'10.3"W.
The FunkSec Forum and Premium Benefits
FunkSec added a forum to their main site in January of 2025. The FunkForum encourages users, including members and interested buyers, to interact, share information about hacking and black hat activities, and view FunkSec updates. Site visitors can sign up and create an account after entering a username, email address, date of birth, and password.
Users who pay $100 can become FunkSec premium members and receive additional benefits. These include the ability to download files from the forum, upload files, create news stories, and start polls. Premium users also receive 20% of FunkSec’s sales transactions, access to a ChatGPT tool and access to a minilocker ransomware builder.
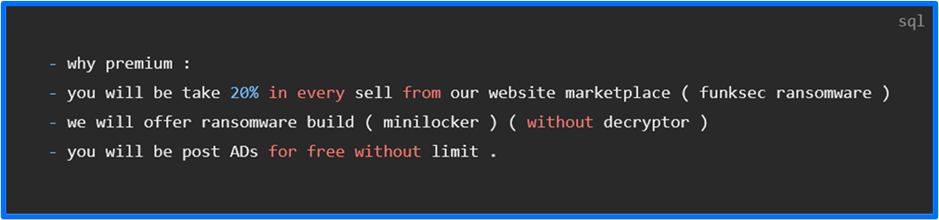
Figure 6: Premium Benefits
FunkSec Ransomware Support: Tickets
Organizations impacted by FunkSec ransomware can submit a ticket on their site after navigating to Ticket. The information included in the ticket is a session ID, name, email address, and a message with one encrypted file. The encrypted file is necessary for the group to verify that the organization reaching out to them is a victim and can receive a decrypted version of the sample encrypted file.
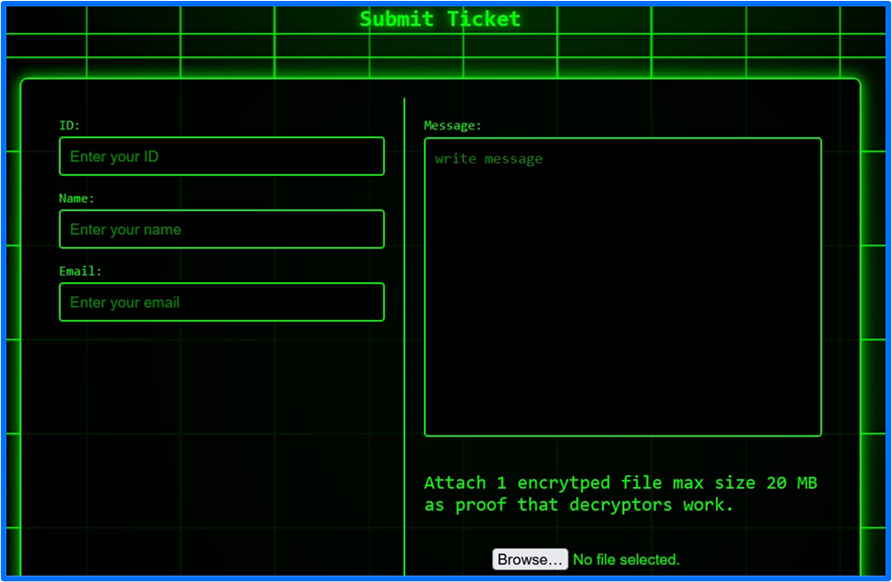
Figure 7: FunkSec Support Ticket
FunkSec Users
A variety of posts on the FunkSec data leak site have over 300 views. In spite of this, the site has few users that publicly interact with one another. The prominent users that have already posted or replied to comments on site updates and activities include scorpion, Sentap, el_farado, and k1083.
scorpion is a FunkSec site admin, and has other roles indicated by badges such as hacker, developer, boss, buyer, seller, premium and DAMN. The user has other roles including Nazi. scorpion posts FunkSec activities and updates on Funk Forum and also manages activities on the FunkBID site. The user has been linked to the DesertStorm alias.
DesertStorm was a user on BreachForums who posted data leaks preceding their ban in November of 2024. They even claimed that FunkSec was responsible for leaking a voicemail message between U.S. President Donald Trump and Israel’s Prime Minister Benjamin Netanyahu. However, it was later discovered that FunkSec generated this fake message with AI. The DesertStorm alias on BreachForums was also linked to interactions with the users named el_farado and Blako on the same platform. To date, researchers have identified a few regions associated with the DesertStorm alias, including Algeria and Brazil.
Sentap is another user on the FunkSec site. Their member badges include Mod, Seller, Hacker, Lord, Boss (forum operator) and the crime. Like scorpion, the user also has the Nazi designation and manages activities on the FunkBID site. Sentap writes comments and replies on Funk Forum in a style that embodies the dialect of an American from the south. This is apparent in the post Clarification Regarding Recent Events where Sentap expounds on the framing of FunkSec ransomware as ‘whipped up by AI,’ finding the idea nonsensical.
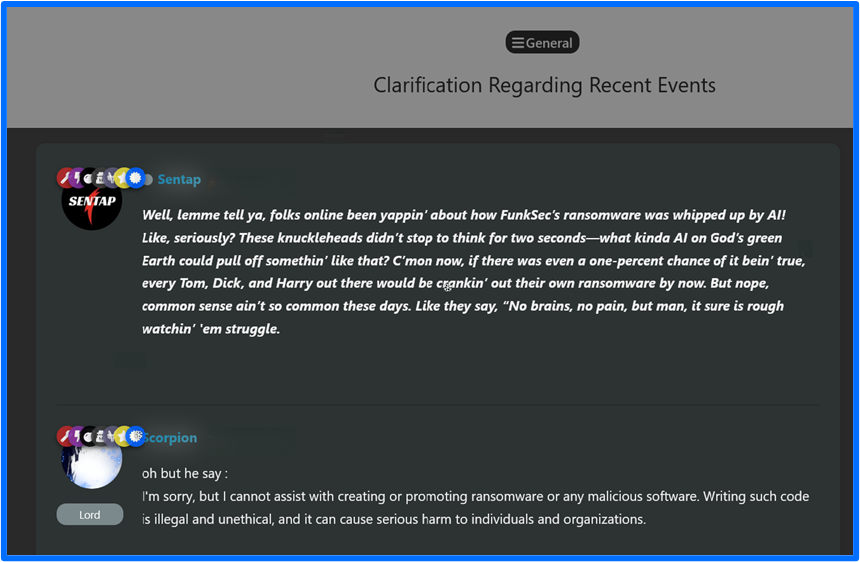
Figure 8: January 2025 Post, Clarification Regarding Recent Events
Sentap is the same name as a persona that was previously associated with RaidForums. RaidForums is a platform that was used to connect users with hacking resources and other information essential for committing criminal acts. A Sentap user on RaidForums was associated with multiple leaks from fall of 2021 to early 2022, including leaks of emails, various documents, and access to sites. In spring of 2022, RaidForums was seized by the U.S. Department of Justice.
el_farado is a user on the FunkSec site that has the roles admin, mod, hacker, lord, and premium. el_farado liked a post that announced a partnership between FSOCIETY and FunkSec. The el_farado user may be associated with the user of the same name on BreachForums who posted a question on how to leak data in November of 2024 to elicit feedback from users with more experience. When taking this information into account, neither FunkSec’s badges nor the casual designation of hacker hold much weight. Still, the el_farado user has shared about a free builder in Funk Forum; the file is accessed via a Gofile link. The user elfarado also manages activities on the FunkBID site.
k1083 is a user on the FunkSec site that has the hacker role. k1083 added a post in the forum titled How to Clean Crypto with XMR | Monero Mixer which outlines steps to clean cryptocurrency anonymously with the use of TradeOgre, VMs, and Monero Wallet.
A Vital Upgrade, FunkSec Version 2.0
When AI is used by a ransomware group that does not possess the knowledge and skills to conduct operations without it, the group’s ability to advance is impacted. One of the larger concerns of a ransomware group that influences the longevity of their operations is their ability to upgrade code.
FunkSec released version 2.0 in February of 2025. The mod named scorpion indicated that FunkSec 2.0 is available to premium members and includes improvements such as additional anti-detection and analysis measures. FunkSec also plans to add a RaaS panel to the next updated version.
According to scorpion, a sample FunkSec 2.0 decryptor is available for victims to test decryption on two files for free once they provide FunkSec support with their contact information. This contrasts from FunkSec’s past claims of the decryptor tool alone costing $500,000 and support requiring a $1 million ransom to decrypt network devices.
Why did FunkSec change their rates? The change may be a result of repeated failures to collect ransoms. Setting high, impractical demands without room for negotiation can deter victims from paying. FunkSec also once marketed their ransomware for $1000 in BTC.
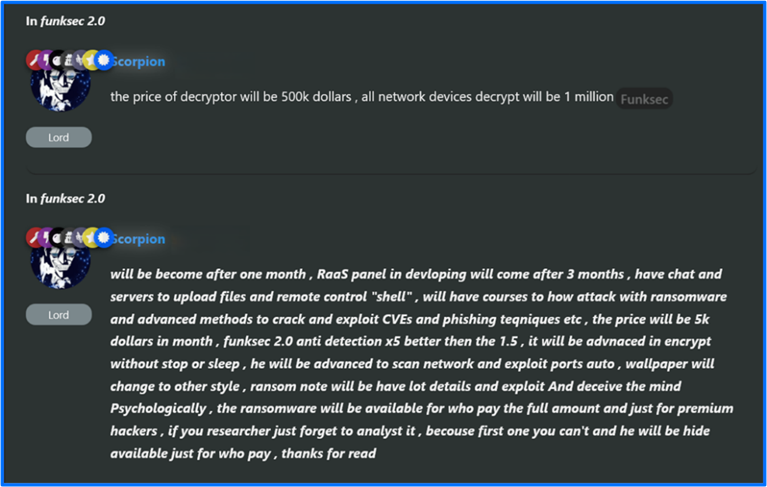
Figure 9: January 2025, FunkSec 2.0 Decryptor Cost
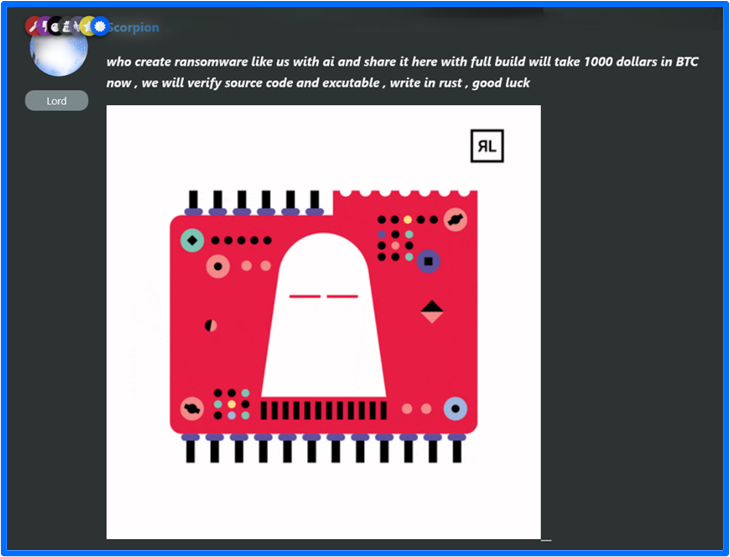
Figure 10: January 2025, FunkSec 2.0 Decryptor Cost
Attack Alternatives and Re-victimization
An update to FunkSec version 2.0 is in progress. What’s a ransomware group in need of an upgrade to do until then? They focus on other techniques until the new code is ready. Those techniques, which may have fewer requisites and resources needed to successfully execute them, include engaging in social engineering, applying techniques that rely on LOLBins (living off the land binaries and scripts), or exploiting weaknesses like leaked credentials.
While the update to FunkSec v2 is in development, the number of victims FunkSec has claimed has not seen a significant decline. This is likely a result of revictimization. FunkSec has claimed numerous victims that were previously hit by other established ransomware groups. They acquire leaked data from other sources and threaten to distribute it. In other words, executing ransomware is not FunkSec’s only strategy.
FunkSec accesses breached data and sells it for profit. As a result, the number of victim organizations affected by FunkSec’s code specifically is likely far lower than the initial claims of 80+ victims identified in December. Extorting repeat victims is just one tactic that enabled FunkSec to continue their operations. The group, however, would see growth in another area: partnerships.
In a recent post titled Hexagon Extortion, FunkSec describes an upcoming model for their operations labeled FunkSec 3.0. It involves several phases, including encryption and exfiltration, exerting pressure on the victim, launching DDoS attacks, auctioning victim data, targeting victim families and connections, and leaking victim data. While the inclusion of these operational activities on the FunkSec site may seem strange, communicating them could be a one of several methods for FunkSec to garner more attention and elevate their reputation.
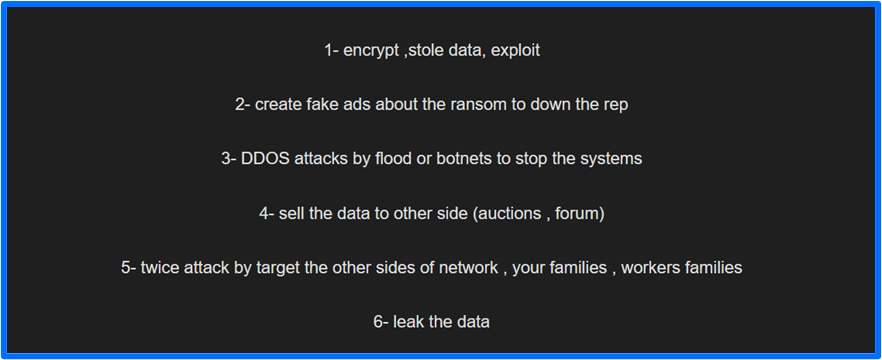
Figure 11: FunkSec - Hexagon Extortion: Operation
FunkSec's Path to Growth
FunkSec’s movements appeared sporadic and even disorganized from November of 2024 leading into early January of 2025. They claimed over 80 victims at that time, however FunkSec’s limited activity on their site, which was still undergoing changes, and their lack of published initiatives were indicators that pointed to internal challenges. Those challenges may be attributed to inadequate staffing or the growing pains of an emerging ransomware group. These factors combined with the notion that FunkSec has a journeyman status in the RaaS sphere due to their limited knowledge in code development left some wondering how the group could persist in the months to come.
FunkSec has used partnership and collaboration to advance. This is evident with their posts that declare new and upcoming affiliate programs, allowing them to broaden their operations and execute campaigns backed by other ransomware groups. FunkSec has formed alliances, joining Kosmos and FSociety. FunkSec wrote that Kosmos would offer its own marketplace for the sale of breached data. FunkSec has even expanded the language options on their site to include not only English and French (a language widely used in Algeria), but also Mandarin and Russian.
Who is FSociety?
FSociety is a threat actor that engaged in a series of data leaks in spring of 2023 and several months afterward. In early 2024, FSociety engaged in double extortion tactics, deploying ransomware and exfiltrating victim data. In mid-January of 2025, a user named FSOCIETY announced a partnership between FSociety and FunkSec on the FunkSec forum. The FSOCIETY user on the FunkSec forum has the designations Mod and DAMN. The user has also posted leaked data on the FunkSec forum, allowing users to access it via MEGA links.
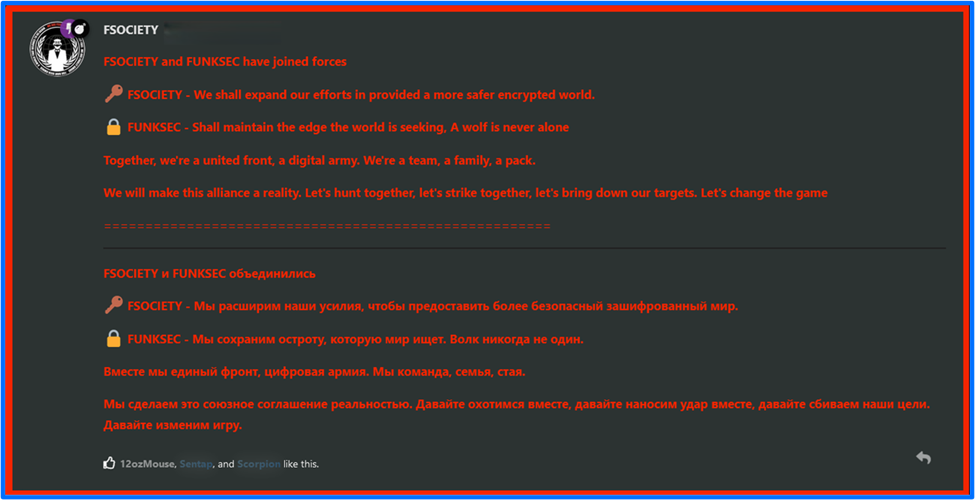
Figure 12: January 2025 Announcement - The FSociety Partnership
FSociety uses a ransomware named Flocker. The group also has an affiliate program intended for FunkSec followers and others like access brokers, hackers, and insiders.
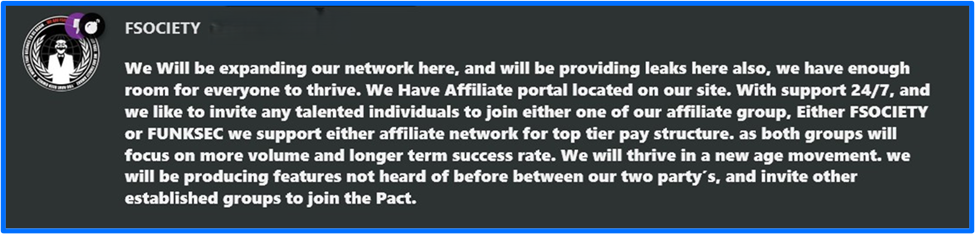
Figure 13: FSociety Encourages Affiliates to Join on FunkSec Forum
FSociety affiliate candidates must complete an interview and show proof of their occupation and ability to conduct work and build long-term partnerships. Affiliate candidates must secure access to a system or network before they can join. Benefits of becoming an FSociety affiliate include access to the Flocker V5 builder with command-and-control functionality, a crypto stealer, keylogger, Flocker RAT, DDoS functionality, 24/7 support, and an advanced attack methods playbook. Support for AI agents is also a pending feature.

Figure 14: FSociety Affiliate Network Requirements
FSociety is one group linked to FunkSec. Other emerging groups may find it beneficial to establish a working partnership with them. Researchers have also speculated about a similar relationship growing between FunkSec and Bjorka (Babuk 2).
FunkSec and Bjorka - A Poser Affiliate or Eager Rival?
The threat actor named Bjorka has hacktivist roots and is associated with a range of breaches impacting Indonesian organizations. A user of the same name posted regularly on BreachForums in 2022 and 2023. In 2024, the threat actor shared leaked victim data posted by FunkSec in DarkForums. Bjorka also asserted their involvement in several of FunkSec’s attacks in their Telegram channel, renaming references to their attacks from Bjorka to Bjorkanism Ransomware (FunkSec).
Bjorka Enters the Chat with a $1000 Plea for a Tattoo
bjorka is a user that joined the FunkSec site in January 2025. On FunkForum, bjorka replied to scorpion’s, Mirrors post and expressed an interest in becoming a FunkSec affiliate.
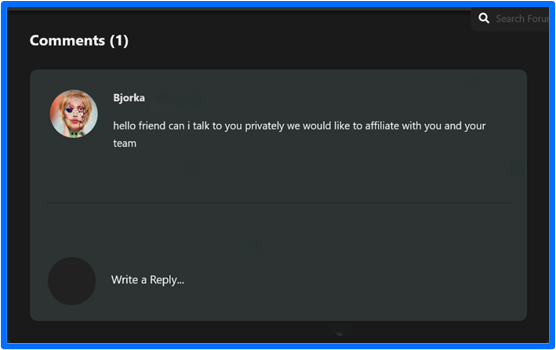
Figure 15: Bjorka's First Comment on the FunkSec Site
A couple of days later, bjorka reached out to scorpion. Their exchange is captured in a Funk Forum post by scorpion titled mafia boss. In the chat, bjorka mentions a previous affiliation with KillSec as the creator of their logo and an opportunity to receive $1000.
The payment of $1000 was for designing the group logo and getting it tattooed. bjorka claimed that KillSec offered this financial incentive; the user wanted to propose a similar offer with FunkSec since he could not seize the opportunity with LockBit. This idea however was shot down by scorpion, who stated that FunkSec is not KillSec and they would give $1000 to Palestine before giving it to a scammer.
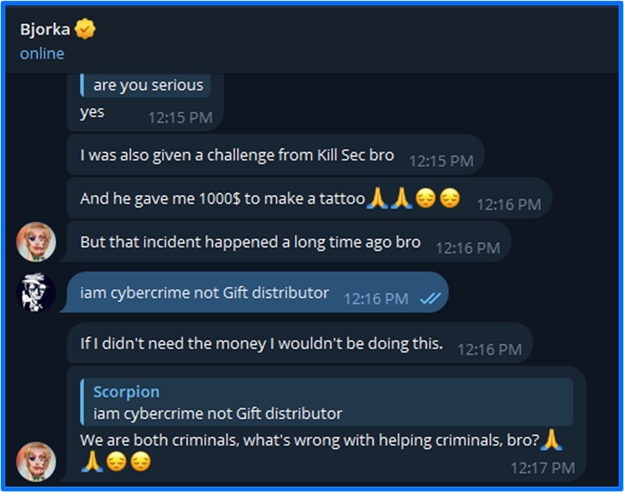
Figure 16: scorpion's Post of an Exchange with Bjorka
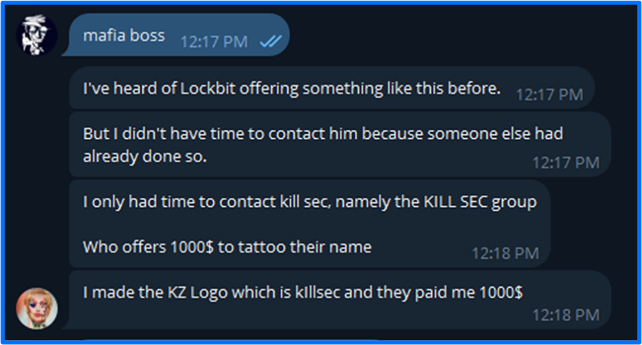
Figure 17: Bjorka's Mention of KillSec
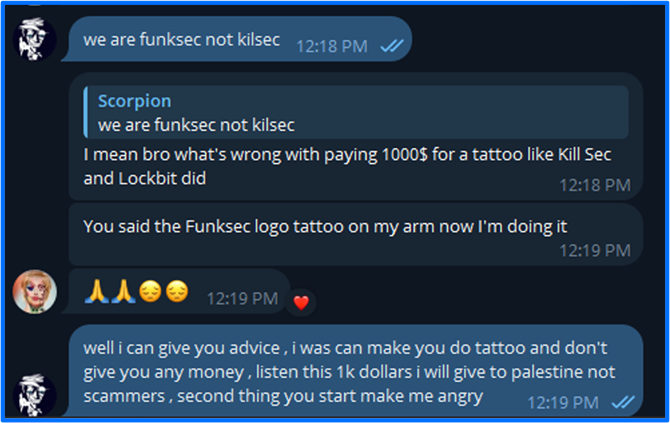
Figure 18: scorpion’s Response
A couple of weeks later, scorpion posted an image of an individual, allegedly the BABUK owner (bjorka), with the FunkSec tattoo on their arm and proposed that maybe in the future they would give Bjorka $10,000. At the time of this release, however, multiple posts and references to the bjorka user on FunkForum are no longer on the site and the user is no longer present on the site.
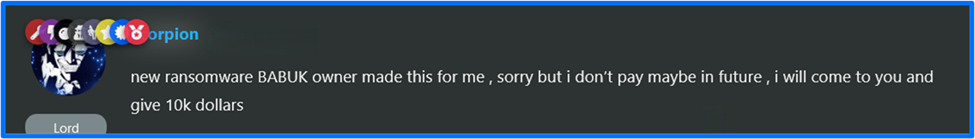
Figure 19:February 2025, scorpion's Post About Babuk

Figure 20: The FunkSec Tattoo
Bjorka’s Connection to FunkSec
In spite of the unusual exchanges between bjorka and scorpion, there is data to suggest that a collaborative relationship may exist between Bjorka (Babuk 2) and FunkSec.
During January of 2025 Babuk 2 (Bjorka) accumulated multiple victims. Some of these victims were already claimed by groups such as FunkSec and LockBit 3.0. An official link between either threat actor has not been established; yet, it is likely that Babuk 2 has established a buyer relationship to market stolen data just as FunkSec does.
A counterargument may also explain Bjorka’s (Babuk 2’s) behavior. Bjorka may pretend to possess stolen datasets to extort victims, grow their reputation, and compete with other affiliates. In early February, Babuk 2 also announced the leak of a LockBit v4 builder. This was a ploy to infect systems with malware, furthering their own agenda.
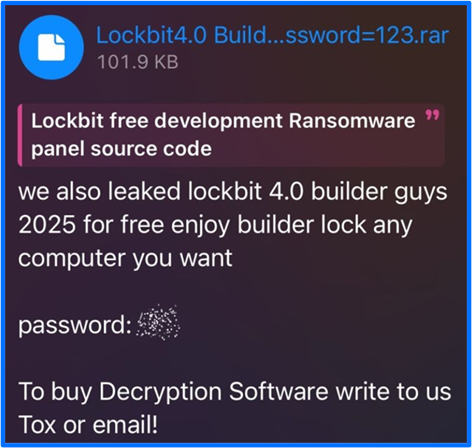
Figure 21: Babuk Release of LockBit 4.0 Builder
FunkSec and Collaborators: United by Hacktivism
What allows several different groups such as Kosmos, FSociety, and potentially Babuuk2 to connect with FunkSec? Hacktivism. Ghost Algeria was a threat actor with hacktivist roots. And, thus matches the workings of Bjorka’s campaigns in the past.
Working towards one goal, the disruption of operations via data exposure or encryption allows ransomware groups with fewer resources to form alliances and garner a larger reputation. It also creates a wider network for target markets and countries.
While hacktivism can propel affiliate programs and recruitment processes, it may also present further risks. If FunkSec forms partnerships, and conflicts between collaborators arise as a result of economic changes or opposing sentiments towards geopolitical groups, there's an increased risk of disloyalty, internal competition, or the termination of the partnerships.
FunkSec - Current Victimology and Considerations
To date, several countries have reportedly fallen victim to FunkSec’s attacks. While FunkSec’s rules of engagement for regions they target are unknown, leanings towards a pro-China and pro-Russia collaborative effort may indicate that organizations based in Taiwan, the Philippines and Malaysia are also at risk.
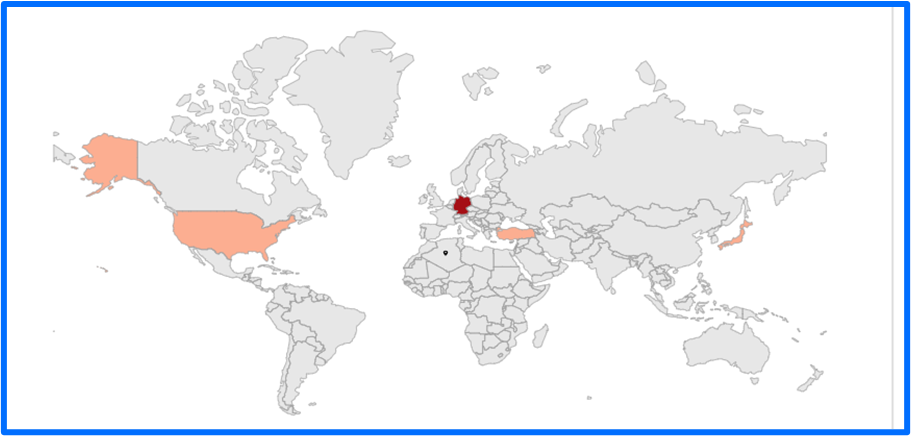
Figure 22: Current Map of Regional Victims
FunkSec Tactics, Techniques, and Procedures
Execution
The threat actor executes the FunkSec ransomware by leveraging Native APIs or a PowerShell script.
Persistence
Persistence is established by hijacking the flow of a program’s execution.
Privilege Escalation
Privilege escalation occurs through process injection, where a malicious process is embedded into an existing process.
Defense Evasion
FunkSec ransomware has defense evasion capabilities, including disabling/modifying tools, the system or firewall, time-based evasion, file deletion, registry modification, and debugger evasion.
Additional Defense Evasion
Other defense evasion characteristics include Windows file and directory permissions modification and altering NTFS file attributes. They also use timestomping, a common anti-forensic technique used to change the timestamps of files.
Discovery
System Network Connections Discovery, Security Software Discovery, Network Share Discovery, Application Window Discovery, Query Registry.
Impact
The FunkSec ransomware encrypts files located in C:\ on the target system and removes the initial file iterations, appending the .funksec extension to all affected files. The ransomware is also capable of inhibiting system recovery, stopping services, and defacing affected sites. The threat actor has been known to change the profile or backgrounds of sites, replacing them with a FunkSec logo and a notice to inform the victim of the attack.
Excerpts from a FunkSec ransomware note include What happened, Ransom Details, How to Buy Bitcoin, Who we are, and Websites to visit.
Under What happened the victim is informed that they have lost their data to FunkSec ransomware and cannot restore it without a decryptor. The victim has the recipient's Bitcoin wallet address and the victim is advised to contact FunkSec after accessing a channel via a unique session ID to buy their decryptor. FunkSec’s current decryptor is .01 BTC, which is approximately $105,700.
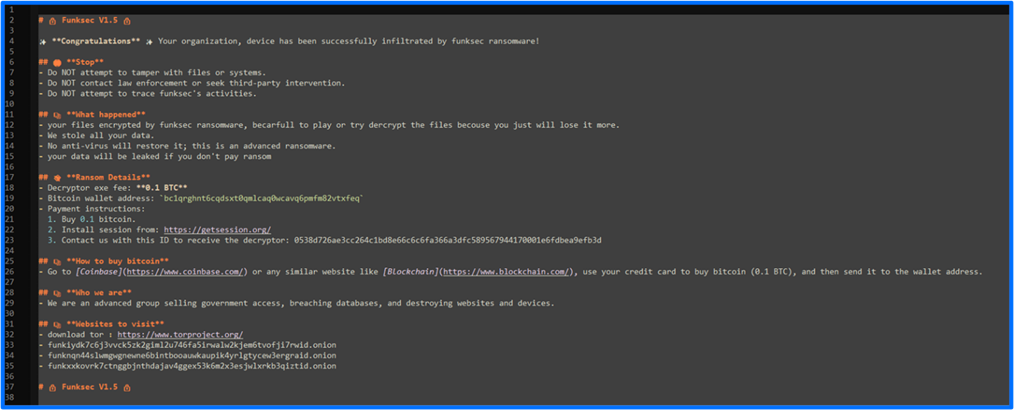
Figure 23: FunkSec Ransomware Note
Recommendations
There are multilayered strategies that an organization can implement to help guard against a ransomware attack. An organization may incorporate best practices into their security program to address gaps in Prevention, Protection, Detection, and Response security measures. The recommendations included below are instrumental for an organization aiming to mitigate and minimize the impact of ransomware threats.
Establish data recovery and resiliency practices: Schedule frequent backups; doing so is important as it ensures that critical data and systems can be restored if a compromise occurs. It’s advised that backups are stored in an offline location and/or cloud environment that is kept separate from the main network. Also, ensuring that backups are regularly tested is essential to verify that no issues impacting data integrity are present.
Implement security awareness and training: Establish regular cybersecurity awareness training that focuses on identifying and reporting instances of phishing and social engineering. Teach employees how to recognize suspicious emails, links, and attachments that may be employed to deliver malicious payloads.
Implement email Security Solutions: Use email filtering solutions to block malicious emails, attachments, and links. Add further protection by enabling attachment sandboxing; this allows a scan to run in real time, proactively identifying ransomware contained in attachments before the attachment is delivered to a user. Disable macros in Microsoft Office documents by default to eliminate opportunities for an attacker to use macros to deliver ransomware payloads.
Perform patch management: Regularly patch and deploy updates across all software, operating systems, and applications. Ensure critical updates are applied promptly, especially for vulnerable remote access systems: VPNs, RDP, and firewalls.
Implement Endpoint Detection and Response solutions: Deploy advanced endpoint protection (EDR) solutions to detect and block ransomware. Use EDR technologies that leverage both behavioral and heuristic-based detections to ensure that initial infection vectors are accurately detected and escalated for investigation. Enable real-time threat detection and automated responses to allow actions that result in isolating compromised devices or blocking malicious processes.
Execute an incident response plan that supports rapid response: Maintain a mature incident response process to support rapid response actions. Rapid response is a vital part of ransomware mitigation and time cannot be wasted. Ensure that the security team has the people, processes, and technologies in place to properly investigate and respond to an incident, e.g., blocking IPs, stopping processes, or isolating hosts to cut off an attacker’s access to critical data and resources to prevent further exploitation.
Leverage Advanced Threat Intelligence with IntelliZone. IntelliZone is a solution that consolidates all the data we’ve gathered regarding cyber threats and the associated threat actors into a single pane of glass for security analysts, including access to Bitdefender’s next-generation malware analysis service. If you already have an IntelliZone account, you can find additional details about FunkSec under the following Threat IDs: BDm5hduttq, BD86b77tr7, BDi06ii0lz, BDn71lopj2, BD71rckrrz, BDwxfsig8j.
Indicators of Compromise
FunkSec Ransomware
| SHA256 Hashes |
|---|
|
c233aec7917cf34294c19dd60ff79a6e0fac5ed6f0cb57af98013c08201a7a1c |
|
66dbf939c00b09d8d22c692864b68c4a602e7a59c4b925b2e2bef57b1ad047bd |
|
dcf536edd67a98868759f4e72bcbd1f4404c70048a2a3257e77d8af06cb036ac |
|
b1ef7b267d887e34bf0242a94b38e7dc9fd5e6f8b2c5c440ce4ec98cc74642fb |
|
5226ea8e0f516565ba825a1bbed10020982c16414750237068b602c5b4ac6abd |
|
e622f3b743c7fc0a011b07a2e656aa2b5e50a4876721bcf1f405d582ca4cda22 |
|
20ed21bfdb7aa970b12e7368eba8e26a711752f1cc5416b6fd6629d0e2a44e5d |
|
dd15ce869aa79884753e3baad19b0437075202be86268b84f3ec2303e1ecd966 |
FSociety (Flocker)
| SHA256 Hashes |
|---|
|
5eba311d64e4daa055d1bc2bca220e8128079238f786a516255268a7cb7af2a1 |
|
2ab50c533a9c28869ae0b5eb9c31e2e791645009fd21d1f2cdeef88222f8d1ac |
|
4e7de092a59ed7bf9aa60905ba06ab20ed6435ea21f8678803390fa1b71d2efd |
|
8f5ce8e264abfabdb6fc2dc271979092ee7260504463c44844e962daea47b0a3 |
|
90b489cca05fec8d84fb288fc712e13f8142d8080298565874723780cab79ee5 |
tags
Author
Bitdefender is a cybersecurity leader delivering best-in-class threat prevention, detection, and response solutions worldwide. Guardian over millions of consumer, enterprise, and government environments, Bitdefender is one of the industry’s most trusted experts for eliminating threats, protecting privacy, digital identity and data, and enabling cyber resilience. With deep investments in research and development, Bitdefender Labs discovers hundreds of new threats each minute and validates billions of threat queries daily. The company has pioneered breakthrough innovations in antimalware, IoT security, behavioral analytics, and artificial intelligence and its technology is licensed by more than 180 of the world’s most recognized technology brands. Founded in 2001, Bitdefender has customers in 170+ countries with offices around the world.
View all postsYou might also like
Bookmarks
