How to manage the headache of defending Industrial IT Infrastructures (Industrial IoT) – Part 1
This is the first of a two-part series of blog posts covering the challenges of securing Industrial IT infrastructures. This part covers:
- Industrial IoT lowers the traditional security barriers between OT and IT
- Lack of built-in security mechanisms, limited visibility and lack of awareness are the fundamental IIoT cybersecurity challenges
- Enabled by the increased attack surface, IIoT security incidents have surged in recent years
Why is Industrial IoT such a big cybersecurity challenge?
The answer is hidden in what Industrial Internet of Things actually is. IIoT generally refers to interconnected sensors, instruments, devices and industrial applications like manufacturing and energy management. This connectivity enables data collection, exchange and analysis, and aims to improve productivity and efficiency. We need to delve deeper into this definition by clarifying another 2 important concepts: industrial control systems (ICS) and operational technology (OT).
- Industrial control system (ICS) is a general term that covers several types of control systems and associated instrumentation for industrial process control. These systems can range from a few modular panel-mounted controllers to large interconnected and interactively distributed control systems with thousands of field connections.
- Operational Technology (OT) is the hardware and software dedicated to detecting or causing changes in physical processes through direct monitoring and/or control of physical devices.
ICS and OT are the realms of Supervisory Control and Data Acquisition (SCADA) systems, distributed control systems (DCS), Remote Terminal Unit (RTU) and programmable logic controllers (PLC). ICS and OT are not new concepts, and many of their underlying technologies and protocols are as old as the Internet itself. The architectural models that have traditionally governed ICS and OT define a clear separation or “air-gap” between industrial control and general IT infrastructure. In the Purdue Model, the air-gap, or demilitarized zone, is placed between Zone 3 and Zone 4 (Figure). This air-gap is important to ensure the security of Operation Technology.
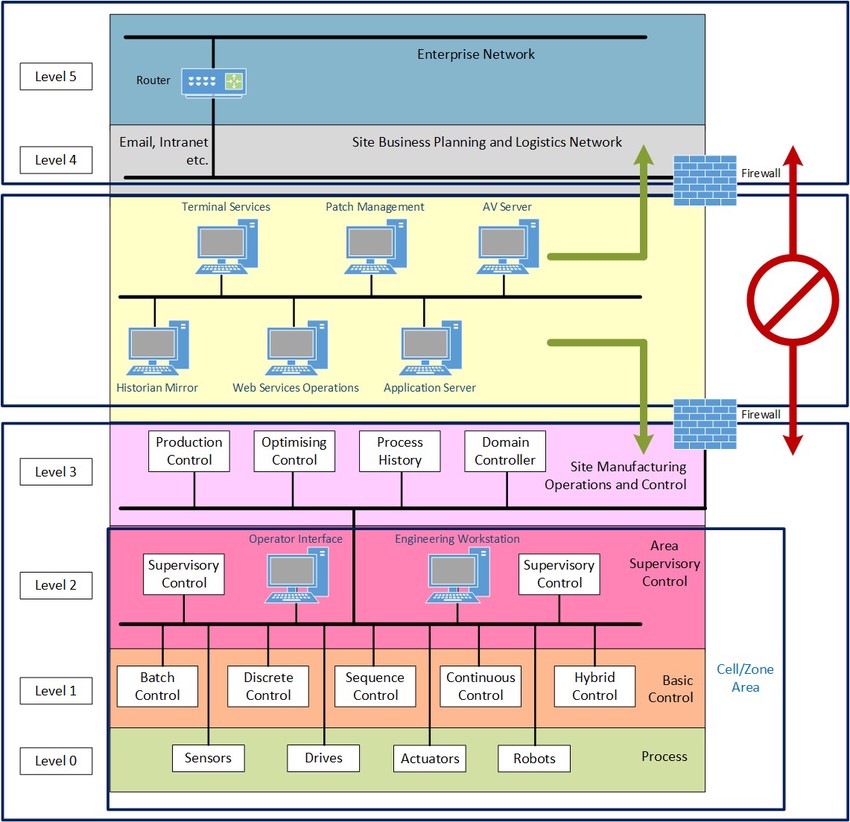
Over time, industry experts figured out that by-passing the air-gap and connecting OT with IT and the Internet could bring organizations even more benefits, like lower costs, and increased performance, productivity and agility. And so, Industrial IoT, or Industry 4.0, was born.
For all its benefits, though, the convergence of OT and IT creates a huge problem: security. Relying on clear separation of the world, the decade-old OT equipment and control systems were not designed with built-in security mechanisms, let alone Internet-ready. OT networks are much more complex, less standardized and more diverse than IT networks. A myriad of technologies and communication protocols, many of them proprietary, are not designed to support modern cyber security mechanisms.
Today, we have a handful of fundamental security problems with OT:
- Lack of built-in cybersecurity mechanisms and enforceable standards
- Very limited visibility (nowhere near what we are used to in the IT space)
- Lack of awareness of (specific) cybersecurity practice
The gradual IT/OT convergence and the development of industrial IoT have spawned new risk scenarios. Historically speaking, attacks on ICS systems have been occurring since the 1990s. The Stuxnet attack in 2010 was highly publicized, highlighting what could happen when ICS systems are compromised. The last three years have seen a significant escalation of IIoT-related cyber events like:
- The US Department of Homeland Security/FBI identifies Russia as the source of the years-long attack on US critical infrastructure and manufacturing
- Hacks cause temporary shutdown of oil pipeline systems
- Vulnerabilities detected in multiple types of industrial hardware and software, including some PLCs, security cameras, routers, bridges/access points, and network management software
- The emergence of a new TRITON/TRISIS variant that can be used to attack many more brands of safety system hardware and has breached US firms
- It is revealed that the China-based “Thrip” group has infiltrated satellite communication, telecom, geospatial imaging, and defense organizations in the US and Southeast Asia
In my next blog I will discuss potential solutions to defend against these types of attacks. What strategies have you implemented against these risks in your organization?
tags
Author

Acting Cybersecurity Professional and Product Marketing Director at Bitdefender, Bogdan has extensive international experience in various roles across IT Industry, including IT Systems Integration, Cybersecurity, Sales Engineering, and Product Management. He enjoys combining his engineering background with industry knowledge and business sense to fulfill his professional mission: help businesses grow by leveraging technology.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks