Hypervisor Introspection: Fighting APTs in Business Environment – Part 2
Since nothing that’s being executed in raw memory is encrypted – just scrambled – APTs that try to execute malicious code on a machine will be intercepted by HVI long before they actually compromise the operating system. In fact, as soon as the malicious code, even delivered via zero-day exploit, tries to execute in the VMs memory, the introspection engine will immediately “see” the malicious action and the code that was trying to be executed.
Annihilating APTs using Bitdefender’s Hypervisor Introspection (HVI)
Unlike traditional heuristic technologies that analyze the behavior of an application with the operating system, HVI knows how malicious actions look at the memory level, regardless if from the operating system’s perspective everything looks fine.
Traditionally, the root of the problem has been that both advanced malware and the security solution were running with the same authority – ring 0. However, running in ring -1 has significant advantages when it comes with detecting APTs or zero-day exploits that can circumvent EPP security.
More than that, HVI can also deploy remediation tools inside the operating system, deleting threats after detecting them, without interfering with the native EPP solution.
How APTs Could Have Been Prevented With HVI
Some of the most media-covered APT attacks could have been prevented before causing any financial or data losses. Even government institutions that have been affected by APTs could have potentially avoided having networks, computers, and data compromised if HVI would have been in place.
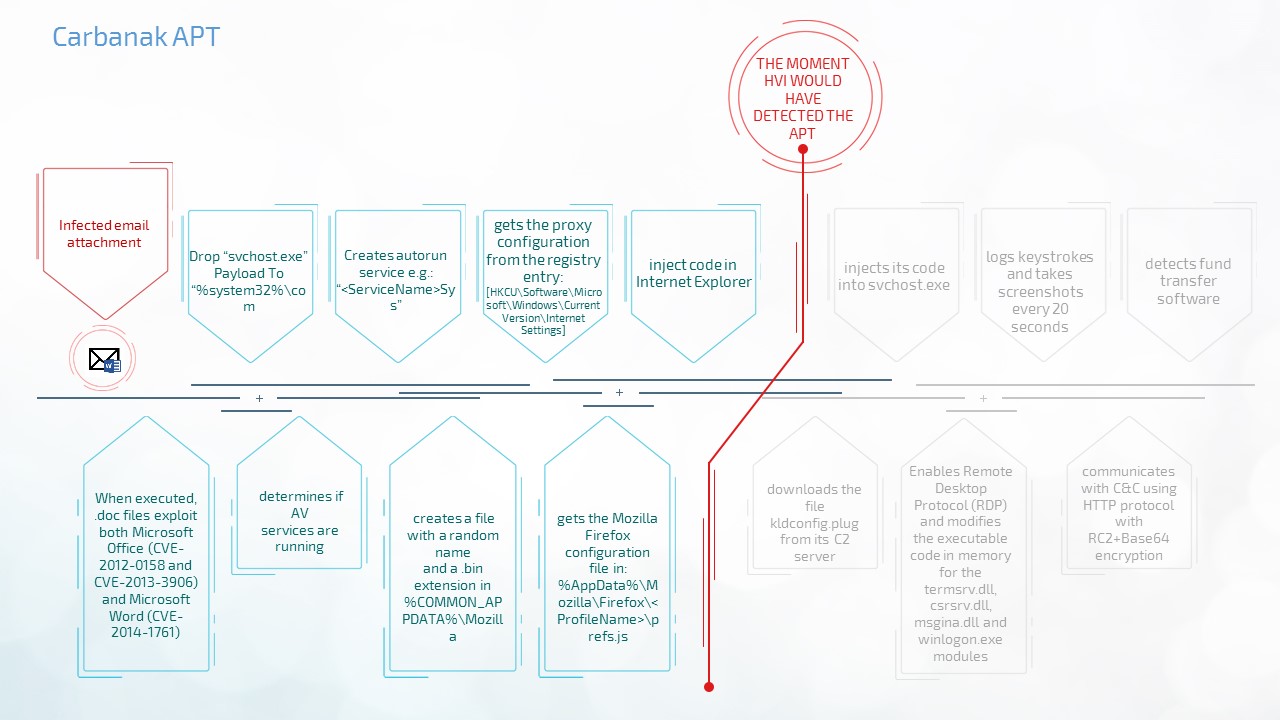
- Carbanak APT vs. HVI
For instance, HVI would have plugged the APT as soon as the user-app payload would have tried to inject the “iexplorer.exe” process.
This means that while the payload would have reached the victim, it would have never been able to compromise the system. However, HVI could have potentially been able go even further back in time, stopping the infected email attachment from exploiting the CVE vulnerabilities that would have downloaded the dropper on the victim’s computer. User mode injection through old or new exploits can easily be detected and plugged by HVI, as it’s able to look at how the code is being allocated and executed in the memory from outside the operating system, by leveraging Citrix’s hypervisor.

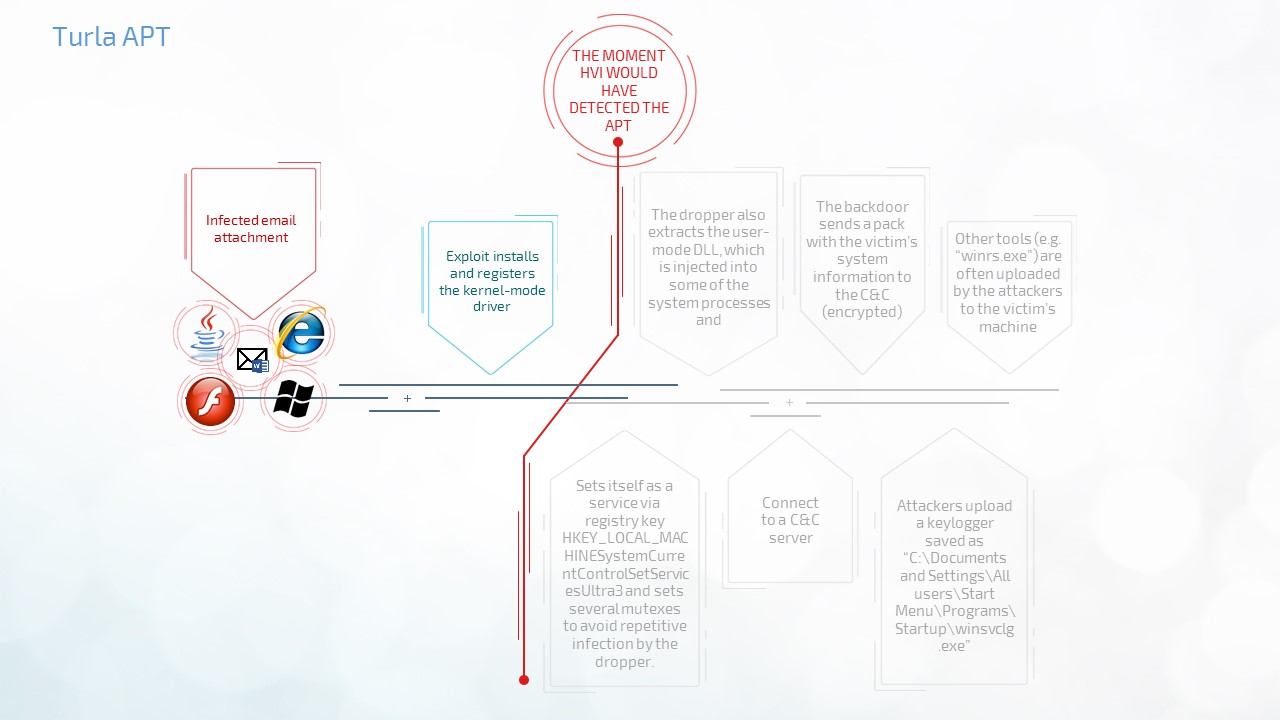
- Turla APT vs. HVI
While financial institutions have constantly been targeted by threats, governments have had their share of sophisticated cyber-espionage threats to deal with. The Turla APT infected hundreds of government computers ranging from military, education, research and pharmaceutical companies across 45 countries.
HVI would have detected any inline hooking performed by the APT when it would have tried to register the kernel mode drivers, which means it would have been right after the infected searching document would have been opened on the victim’s computer. This means that no dropper would have ever reached the system, allowing a backdoor for attackers in order to fortify their foothold.
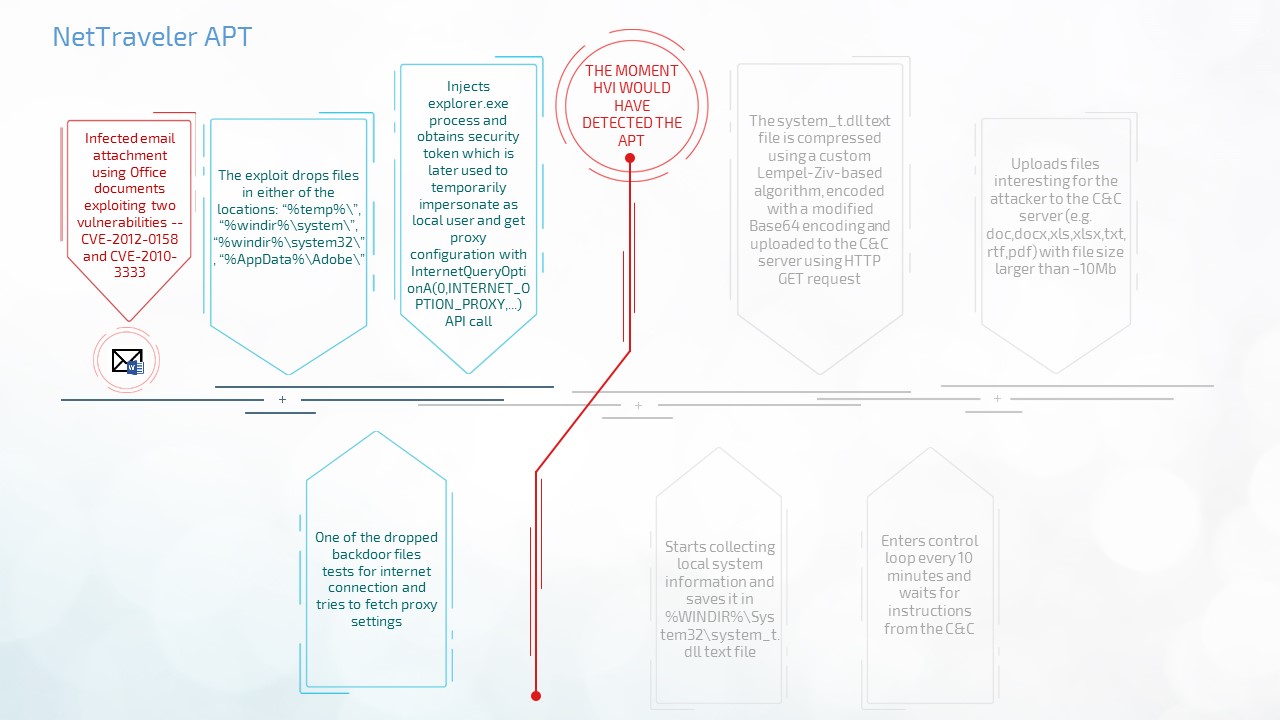
- Net Traveler vs. HVI
Another great example of information-stealing APTs is Net Traveler. Quietly stealing information since 2004, more than 22 gigabytes of data pertaining to aerospace, nanotechnology, nuclear power cells, lasers, drilling, manufacturing in extreme conditions, and radio wave weapons have been exfiltrated without triggering any bells and whistles for a years.
HVI would have cut off the entire attack chain the minute the user-app payload would have tried to inject the “explorer.exe” process, and trigger a warning to the EPP solution installed on the machine. This would have completely plugged any attacker from “dialing in” to the victim and also instructed the EPP solution to delete/quarantine the payload and disinfect the machine.
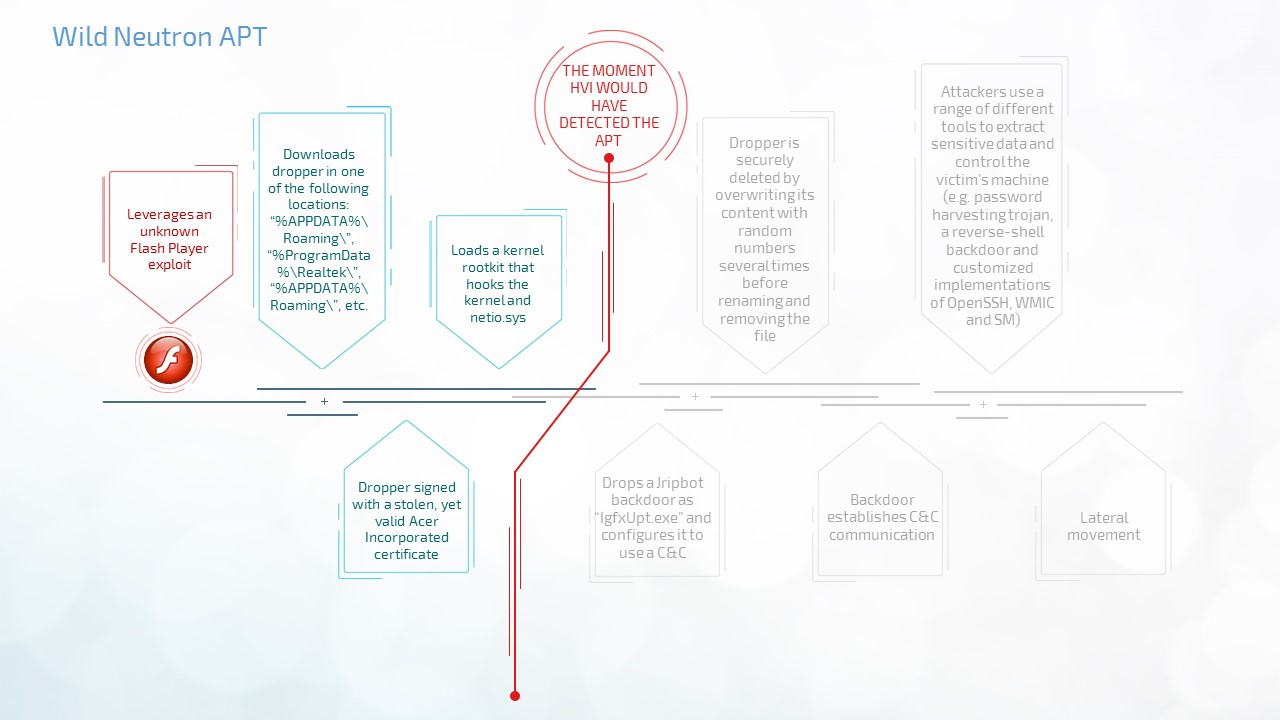
- Wild Neutron vs. HVI
Apple, Microsoft, Facebook, and Twitter were amongst the victims of this particular APT, as the APT not only used a stolen code signing certificate – belonging to Taiwanese electronics maker Acer – but also because it relied on an unknown Flash Player exploit to infect victims. This cyber-espionage APT was responsible for also affecting law firms, investment companies, IT companies, and healthcare companies across more than 11 countries and territories.
By looking at the raw memory stack, HVI would have been able to see any inline hooking and prevent the APT from loading the kernel rootkit, even if it was signed with a valid digital certificate. Regardless if it’s a legitimate application that tries to do hook the kernel, HVI notifies the EPP and triggers the appropriate response.
Bottom Line Benefits of Using HVI
With minimum performance impact on VMs, it has already proven to be effective against several known APTs, pointing that it’s more than capable of detecting APT attack types, patterns, and payloads.
Another major HVI benefit is that’s it assumes from the get-go that the VM is infected and doesn’t rely on any information coming from the operating system. Being able to read raw memory from the hypervisor level means that it’s completely unsusceptible to any type of APT attack aiming to compromise the VMs operating system.
tags
Author

Liviu Arsene is a Global Cybersecurity Researcher for Bitdefender, with a strong background in security and technology. Researching global trends and developments in cybersecurity, he focuses on advanced persistent threats and security incidents while assessing their impact in critical public and private business infrastructures. His passions revolve around innovative technologies and gadgets, focusing on their security applications and long-term strategic impact.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks











