Identifying Security Gaps Using the NIST Cybersecurity Framework: Part 1

Welcome to the first part of a five-part series exploring how the NIST Cybersecurity Framework (NIST CSF) 2.0 can help identify security gaps and assess what should be handled in-house versus outsourced to a trusted security partner. I'll explore the components of cybersecurity frameworks using NIST CSF 2.0 as our guide, breaking down its six core functions and highlighting where Bitdefender can support security teams.
A recent survey conducted by the SANS Institute found that nearly 70% of participants used a cybersecurity framework to help define and measure their internal security team and 74% of those using one, use NIST. So, what exactly is NIST CSF 2.0?
NIST CSF 2.0
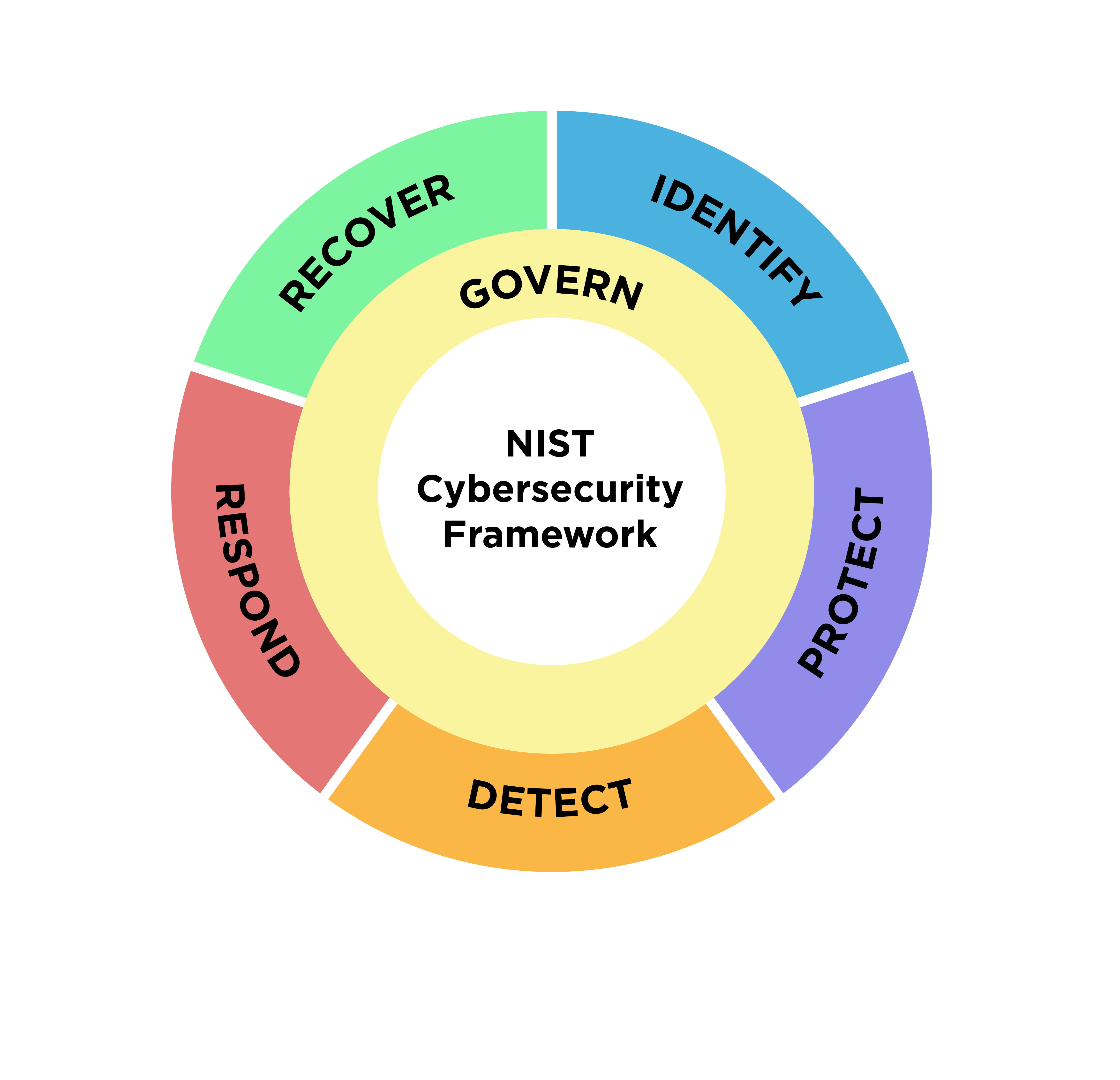
NIST CSF 2.0 is comprised of six high level functions that are descriptive in name and provide the structure for how an organization focuses and addresses their cybersecurity needs. These are Govern (new to 2.0), Identify, Protect, Detect, Respond, and Recover. Under each function there are a series of categories that define a specific security outcome. Those categories are then also broken down into subcategories that further define more specific outcomes of technical and management activities.
The NIST CSF 2.0 graphic wheel is representative of the interconnectedness of each of the functions and a logical order in which to compose a cybersecurity program and address potential threats. Govern, newly introduced in version 2.0 this past year, sits in the middle because it oversees the internal processes for how an organization manages and prioritizes each of the other five functions. The other functions go in clockwise order starting with Identify where an organization categorizes the assets within their environment and then they Protect those assets with systems, processes, and tools. They then monitor those tools and systems to Detect and Respond to threats. Finally, they create a plan to Recover from a cybersecurity incident.
Each function is vital to the implementation and success of a cybersecurity program and often the functions overlap or cannot be addressed in isolation without consideration for another. For example, it’s not possible to create a plan and deploy a set of security tools to protect assets that haven’t been identified, categorized, assessed, and prioritized first. However, many organizations don’t have the ability to dedicate equal attention and resources to each function often due to the lack of staff manpower, time, or even general security knowledge and expertise.
The Six Functions
While I’ll dive deeper into each of the functions in the later blogs, I want to spend some time highlighting each function and their top-level categories before we dive into how to use this framework to perform an assessment.
Govern
As mentioned above, Govern oversees and sets the foundations for how an organization views, discusses, communicates, plans, and prioritizes the other five functions. It’s all about creating the team who will oversee the program, the creation and dissemination of the plan, the defining of roles and responsibilities across the org, and the implementation of the policies, processes, and procedures. There are six categories that fall under Govern:
- Organizational Context: How an organization understands its own unique environment, the company size, dependencies, mission and expectations, etc, and how that informs their cybersecurity risk management decisions
- Risk Management Strategy: How an organization establishes, communicates and uses a strategy plan around their priorities, constraints and risk tolerance when making operational decisions.
- Roles, Responsibilities, and Authorities: How an organization defines the cybersecurity roles, responsibilities and authorities to ensure accountability, performance assessment, and continuous improvement.
- Policy: How an organization creates, communicates and enforces its cybersecurity policies.
- Oversight: How an organization assesses their risk management strategy in order to continually adjust and improve it.
- Cybersecurity Supply Chain Risk Management: How an organization plans, implements, and manages the process and strategy used to oversee supply chain risk.
Identify
Starting with the first of the primary functions, Identify refers to how the organization discovers, manages, and prioritizes all their assets. In this case, assets mean all the things that may fall under a cybersecurity umbrella or need to have some form of security oversight such as data, hardware, software, systems, facilities, services and people. This also includes the identification of areas of improvement across the organization’s policies, plans, processes, procedures and practices that support or overlap with a cybersecurity risk management plan. There are three categories under the Identify function:
- Asset Management: The goal is to maintain a comprehensive inventory of all the organization's assets—both physical (like physical premises, computers, servers, and networking equipment), people (like user accounts, identities, emails, and third-party users or companies), and digital (like software, data, and intellectual property). Proper asset management ensures that the organization knows what needs protection, where potential vulnerabilities might exist, and how assets are interconnected.
- Risk Assessment: The aim is to systematically identify potential threats, vulnerabilities, and the likelihood of various cybersecurity events. By understanding the risks, organizations can make informed decisions about where to focus their cybersecurity efforts, what controls to implement, and how to balance security with other business needs.
- Improvement: The goal is to continually refine and strengthen the organization’s cybersecurity practices. Continuous improvement is critical for managing cybersecurity risk. It ensures that the organization does not become complacent and that its defenses remain effective over time.
Protect
Next, the Protect function is how an organization develops and implements appropriate safeguards that can protect critical assets, data, and systems from a variety of threats or vulnerabilities. In essence, it’s all the plans, processes, tools, and systems that are implemented to help organizations prepare for and prevent threats or to help maintain uptime, availability and eliminate other obstructions. It is essential for reducing the risk of security breaches and ensuring that, even if an incident does occur, its impact is minimized.
- Identity Management, Authentication, and Access Control: Manages who can access what within the organization ensuring only authorized users, devices, and systems can access resources and perform specific actions. Proper identity management and access control are critical for preventing unauthorized access to sensitive data and systems, reducing the risk of insider threats, and ensuring that users can only access what they need to do their jobs.
- Awareness and Training: Educating and empowering employees to protect the organization’s assets to ensure that everyone in the organization understands their unique roles, cybersecurity risks, and knows how to avoid common pitfalls like phishing attacks, weak passwords, and other vulnerabilities.
- Data Security: Protecting data from unauthorized access, alteration, or destruction, whether it’s at rest, in transit, or in use. Effective data security measures help prevent data loss, theft, and corruption (digitally and physically).
- Platform Security: To safeguard the integrity, availability, and confidentiality of the platforms that support critical systems and applications. If the platform is compromised, it can undermine the security of all applications and data hosted on it.
- Technology Infrastructure Resilience: To maintain the continuous operation of critical systems and services by building resilience into the technology infrastructure. It minimizes downtime, protects against data loss, and helps maintain the trust of customers and stakeholders by ensuring that critical services remain available.
Detect
The detect function is all about the on-going process to monitor the tools and systems deployed to discover threats quickly. It’s about how an organization creates and manages their team members, and the processes and plans put in place to ensure that events and alerts are being monitored and investigated to ensure the timely detection of threats.
- Continuous Monitoring: This category is all about the ongoing, real-time observation of the organization’s IT environment to detect cybersecurity threats and ensure that protective measures are effective. Continuous Monitoring is crucial for early detection of cybersecurity threats, allowing the organization to respond quickly and effectively. By maintaining real-time awareness of the security status of their IT environment, organizations can minimize the potential damage from incidents and ensure that security controls remain effective over time.
- Adverse Event Analysis: The systematic examination and evaluation of security events detected to determine their nature, impact, and appropriate response. Proper analysis of adverse events is essential for distinguishing between true security incidents and benign anomalies, allowing organizations to prioritize their response efforts effectively.
Respond
Security teams are only as successful as their ability to correctly and efficiently respond to the threats they’ve detected. A proper response program is critical for managing and minimizing the effects of a cybersecurity incident. It involves a set of coordinated activities designed to address and mitigate the immediate impacts of an incident, restore normal operations, and prevent future incidents.
- Incident Management: Ensuring that the organization has a structured approach for managing and coordinating response efforts during a cybersecurity incident. This includes defining policies, procedures, and playbooks that detail roles, responsibilities, for all stages of an incident. Effective incident management ensures that incidents are handled in a consistent and coordinated manner, minimizing confusion, reducing response times, and helping to mitigate the impact of the incident on the organization.
- Incident Analysis: The thorough analysis of detected incidents to determine their cause, impact, and potential implications. The goal is to gain a clear understanding of what happened, how it happened, and what could be affected. Incident analysis is crucial for determining the priorities and best course of action during an incident. By understanding the incident's details, the organization can effectively contain the threat, prevent further damage, and begin recovery.
- Incident Response Reporting and Communication: Ensuring a plan is in place for the structured and timely sharing of information about the incident with all relevant stakeholders. During an incident, there are a variety of levels of stakeholders to inform including employees, regulatory bodies, customers, shareholders and other affected parties. An effective communication and reporting plan ensures that everyone involved is aware of the situation and their role in addressing it for a proper coordination of response efforts. Proper communication also helps maintain trust with outside stakeholders and customers.
- Incident Mitigation: Focuses on the actions taken to limit the impact of a cybersecurity incident and prevent it from escalating. Mitigation efforts aim to stop the spread of the incident and protect unaffected systems and data. Quick and effective mitigation actions can prevent further damage, reduce recovery times, and help protect the organization’s assets and reputation.
Recover
The Recover function is essential for restoring systems, data, and operations after an incident and for strengthening the organization’s ability to deal with future incidents. It’s focused on the plans and processes in place (including rigorous testing and tabletop scenarios) ensuring that an organization can recover and get back up and running after an incident in a timely manner. Effective recovery is critical for minimizing downtime, reducing financial and reputational damage, and ensuring the continuity of business operations. It also helps build organizational resilience by incorporating lessons learned into future planning and improving overall security practices.
- Incident Recovery Plan Execution: Involves carrying out the steps defined in the recovery plan to restore systems, data, and business operations following a cybersecurity incident. The goal is to ensure that the organization can effectively and efficiently restore its operations and services to normal after an incident minimizing downtime and reducing the financial and operational impact of the incident.
- Incident Recovery Communication: In the event of an incident, information must be communicated efficiently and with proper oversight to all relevant stakeholders both internal and external. The goal is to keep stakeholders informed about the status of recovery efforts, expected timelines, and any necessary actions they need to take. Effective communication during recovery helps manage expectations, maintain transparency, and support coordinated efforts to restore normal operations.
Grouping the Categories
Personally, when I look at cybersecurity frameworks, and especially NIST CSF 2.0, I like to simplify it and group each of these functions into 3 distinct phases tied to what I’ll call the lifecycle of a threat:
- Preparation (pre-threat): Comprised of the 3 functions Govern, Identify, and Protect. This is focused on the tools implements, processes put in place, and how the cybersecurity program is implemented to help prevent and mitigate threats.
- Incident (active threat): Comprised of Detect and Respond, this phase is all about an active threat occurring in real time. How is the team monitoring and analyzing events to detect threats quickly and how do they respond efficiently and effectively to prevent the threat from causing damage.
- Breach (post threat): Compromised of Recover and is focused all on disaster recovery and business continuity in the event a threat was successful.
Preparation
When thinking about the lifecycle of a threat or attack, it all begins with preparation (on both sides of the coin). It’s about how organizations prepare their team and environment to reduce the likelihood of an attack being successful. It’s how they build and train their security team, how they invest, implement and harden their security tools, and how they plan, organize, and manage all their assets and users, with the policies and procedures put in place to help reduce and mitigate risks as much as possible.
Incident
This is when live bullets are firing. An attack is underway, and the threat is real. How does the organization handle the detection of a threat as the attacker uses a variety of tactics and techniques to compromise users, systems, applications, etc. How does the security team monitor event logs, perform investigations and identify malicious activity? Once the threat is discovered, what’s the response to boot the attacker out and ensure that systems are clean and users are no longer compromised?
Breach
The final stage of a successful attack, which every organization hopes to avoid, involves recovery and business continuity after a successful breach. In this post-threat phase, the attackers have gained access to data, and the focus shifts to cleanup, restoring systems to working order, and resuming business operations. It’s essential to evaluate how to recover efficiently, restore normal operations, and apply lessons learned to strengthen current capabilities and continuously improve defenses.
Using the Three Phases
By breaking down the framework into these three distinct phases, organizations can understand the risk profile of each function a little better in the context of an attack chain. It’ll make it easier to prioritize areas of focus and direct attention to areas that have the highest return on investment by reducing the greatest amount of risk and vulnerabilities the quickest without compromising security or other areas. The above also allows for easy articulation of the current cybersecurity posture in an easily digestible format for non-technical stakeholders within the senior management team.
That’s Great...Now How do we Use NIST CSF 2.0?
Understanding each of the functions that comprise a cybersecurity framework like NIST CSF 2.0 can help organizations understand the series of objectives and tasks required to implement a proper cybersecurity program. Using these frameworks can help organizations perform a full assessment to identify what they might already be doing, what they are currently not doing or overlooking, and where they might be well covered or have security gaps.
This blog has covered a substantial amount of information, and there’s much more to explore. In the next part of this series, we’ll delve into how to leverage NIST CSF 2.0 to identify security gaps and strengthen your organization’s cybersecurity posture.
If you're looking to get your cybersecurity journey started, check out how Bitdefender's security platform can help you. Read up on our GravityZone XDR solution or learn how our MDR service can help empower your team.
tags
Author
Kevin is the Principal Product Marketing Manager at Bitdefender. With a technical background, he excels at storytelling and messaging across a variety of cybersecurity fields.
View all postsYou might also like
Bookmarks


