How to Improve Threat Visibility and Reduce Time to Detection with Network Traffic Analytics (NTA)
Network Traffic Analytics is a new category of security solution designed to improve visibility into threat-related activity and reduce the dwell time of advanced attacks.
This blog provides an overview of NTA solutions and answers the following:
- What is NTA and how does it work?
- How does NTA fit into the existing security architecture?
- How does NTA facilitate threat-hunting and compliance efforts?
What is NTA and how does it work?
Despite effort by organizations around the world to improve incident detection and visibility, as an industry we are still obviously struggling. The 2018 Cost of a Data Breach Study by Ponemon Institute LLC shows the mean time to identify a breach in 2018 grew to 196 days, a full week longer than in 2017. In addition, Verizon disclosed in its 2018 Data Breach Investigation Report credits 60% of breach discoveries to third parties. That means six of every 10 organizations targeted by advanced attacks have no idea they were breached.
The problems of threat visibility and early breach detection are at the core of the new security solution category: Network Traffic Analytics. NTA relies on collecting and analyzing network traffic – flows and protocol data – to identify fraudulent or malicious intent. Complementing existing security architecture, NTA solutions focus on detecting advanced threats that may bypass other security controls. What sets NTA apart as a distinct category is the use of Artificial Intelligence and Behavior Analytics. Developments in AI in recent years have opened up new horizons and made possible brand new use-cases, such as unassisted learning of network behavior and detection of traffic anomalies.
NTA solutions are designed to capture, store and inspect all network traffic (i.e. machine A connecting to machine B within the internal network), and external network traffic (i.e. machine A communicating with server C on the Internet outside the boundary of the network).
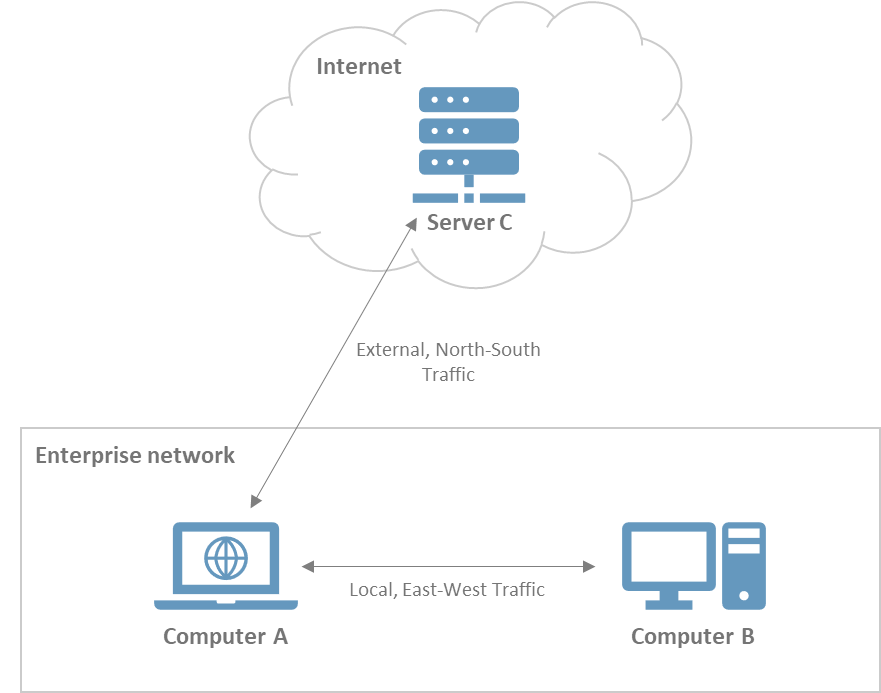
AI-based NTA solutions can apply machine learning algorithms to learn the typical behavior patterns on the network and spot anomalies. What anomalies? When an endpoint is compromised, its network interactions differ from traffic generated by endpoints conducting legitimate business operations. NTA solutions leverage these anomalies to spot attackers that have penetrated the network and expose their activities.
Where does NTA fit in the cybersecurity stack?
Two perspectives should be considered: security controls and security technologies.
Security Controls: As defined by the CISSP Common Body of Knowledge (CBK), cybersecurity controls include Directive, Preventive, Detective, Corrective and Recovery Controls. NTA is a detective control solution that uses network communications as the data source for detecting and investigating anomalous activity.
Security Technologies: NTA solutions are often compared to existing perimeter security technologies (especially Next-gen FW and IDS/IPS) and network monitoring. These solutions have proven their worth time and time again in defending the network perimeter. Cloud, mobile and IOT have riddled the enterprise network perimeter with holes. Networks are borderless. Devices in the modern workplace are mobile – laptops, tablets, smart devices, mobile phones – all of which are Endpoints outside the enterprise perimeter when connecting to the internet on public WiFi. When they rejoin your network, the threat walks right in, bypassing all perimeter controls.
Threats already operating within your network go undetected by perimeter controls due the inability to detect malicious intent on east/west traffic or encrypted traffic. Once inside the network, the attacker uses very different tools and techniques, aiming to move laterally and compromise other machines, than when breaching perimeter defenses.
NTA is not designed or intended to replace existing security architecture elements, but to complement them. It is purposely built to detect threats operating within the network and to provide complete visibility across an environment, covering both typical corporate endpoints and unmanaged devices like:
- Bring-Your-Own-Device (BYOD)
- IOT devices
- Embedded systems
- Medical devices
- Any network connected device
NTA can improve threat hunting effectiveness and facilitate compliance
Using network traffic as “the source of truth,” NTA can act as a single early warning system. The capacity to automatically triage and to provide context to each security incident also helps SOC teams focus on the incidents that are important to investigate. NTA solutions can store traffic meta-data for extended periods (years), facilitating forensics as well as proactive threat hunting for newly discovered IOC (indicators of compromise).
NTA solutions can give organizations greater visibility into all threats related to network activities and help detect threats faster. In addition, full visibility into network activity and extended data retention capabilities dramatically improve insider threat detection and help achieve compliance.
Want to know more?
Watch our on-demand webinar if want to learn more about how to improve threat visibility and reduce time-to-detection. We also recommend reviewing the “Combating Advanced Threats with Network Traffic Analytics” whitepaper and visiting the Bitdefender Network Traffic Security Analytics webpage.
tags
Author

Acting Cybersecurity Professional and Product Marketing Director at Bitdefender, Bogdan has extensive international experience in various roles across IT Industry, including IT Systems Integration, Cybersecurity, Sales Engineering, and Product Management. He enjoys combining his engineering background with industry knowledge and business sense to fulfill his professional mission: help businesses grow by leveraging technology.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










