Mobile Stock Trading Apps Found To Be Poorly Secured
Security research firm IOActive recently set out to investigate the security of 21 mobile brokerage apps used for trading stocks and other equities. The results were less than reassuring.
In an analysis recently published by Alejandro Hernández (@nitr0usmx) the 14 security controls listed below were tested:
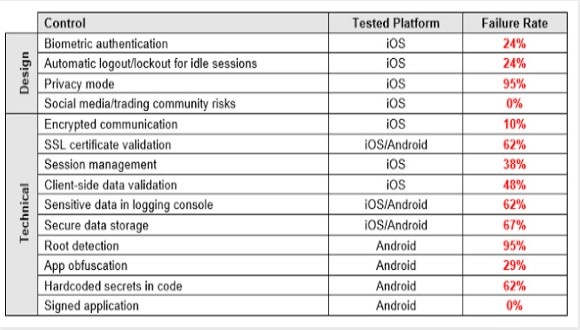
Let’s take a look at authentication. First is the cleartext password exposure. According to Hernández’s research it’s possible to extract passwords from four apps (19% of the apps) because the user’s password is sent in some form of cleartext. Now, while obtaining the password would require physical access to the device — and this certainly mitigates the danger here somewhere — there’s no excuse for such apps having such lackadaisical design.
When it comes to authentication woes in the trading apps, two apps conducted authentication through unencrypted HTTP and another app exposed the password in the logging console after a password change.
In addition to poor authentication hygiene, the mobile trading apps leaked more information than they should. In fact, according to Hernández, 62 percent of the applications sent sensitive data to log files, and 67% stored it unencrypted. Physical access to the device is required to extract this data. “This sensitive data encompasses values such as personal data, general balances, cash balance, margin balance, net worth, net liquidity, the number of positions, recently quoted symbols, watchlists, buy/sell orders, alerts, equity, buying power, and deposits. Additionally, sensitive technical values such as username, password, session ID, URLs, and cryptographic tokens should not be exposed either,” Hernández wrote.
Again, not the end of the world but no excuse.
During communications of trades and market data, two apps examined rely on unencrypted HTTP channels to transmit and receive all data. While 13 of the 19 applications that do employ HTTPS don’t check authenticity of the remote endpoint through SSL certificate verification. This makes man-in-the-middle attacks feasible, both to snoop and to change data.
This is a serious and completely unacceptable way to manage trading data. “A malicious actor could intercept and alter values, such as the bid or ask prices of an instrument, and cause a user to buy or sell securities based on misleading information,” he wrote.
In most of the apps that fail to check SSL certificates, it’s possible for man-in-the-middle attackers to inject malicious JavaScript or HTML code in the server responses. “Since the Web Views in ten apps are configured to execute JavaScript code, it’s possible to trigger common Cross-site Scripting (XSS) attacks,” Hernández wrote.
As Hernández concluded, there’s much that needs to be done to better secure mobile trading apps. He provided the following guidance:
- Desktop and web platforms should also be tested and improved.
- Regulators should encourage brokers to implement safeguards for a better trading environment.
- In addition to the generic IT best practices for secure software development, regulators should develop trading-specific guidelines to be followed by the brokerage firms and FinTech companies in charge of creating trading software.
- Brokerage firms should perform regular internal audits to continuously improve the security posture of their trading platforms.
- Developers should analyze their apps to determine if they suffer from the vulnerabilities I have described in this post, and if so, fix them.
- Developers should design new, more secure financial software following secure coding practices.
- End users should enable all of the security mechanisms their apps offer.
tags
Author

George V. Hulme is an internationally recognized information security and business technology writer. For more than 20 years Hulme has written about business, technology, and IT security topics. From March 2000 through March 2005, as senior editor at InformationWeek magazine, he covered the IT security and homeland security beats. His work has appeared in CSOOnline, ComputerWorld, Network Computing, Government Computer News, Network World, San Francisco Examiner, TechWeb, VARBusiness, and dozens of other technology publications.
View all postsRight now Top posts
FOLLOW US ON SOCIAL MEDIA
SUBSCRIBE TO OUR NEWSLETTER
Don’t miss out on exclusive content and exciting announcements!
You might also like
Bookmarks










